Ethical Hacking: Profitable CEH Jobs for Freshers Salary
Businesses all over the world are looking for competent people to …
Best CEH Training Institute in Delhi | Craw Security
CEH Training Institute in Delhi In today’s time, people are inclined …
Get Hands-On Experience in Ethical Hacking | CEH v13 Ai
Get Hands-On Experience in Ethical Hacking EC-Council is extremely careful to …
What is Penetration Testing | Introduction to Penetration Testing
Protecting your digital assets is more important than ever in the …
Brief Introduction To Ethical Hacking | CEH Tutorial
Brief Introduction To Ethical Hacking | CEH Tutorial …
Python File Handling: How to Create, Open, Read, Write
Python File Handling is literally a crucial segment in Python Programming …
Introduction to Artificial Neural Networks
With a basic understanding, Artificial Neural Networks (ANN) can be best …
What is Cloud Computing? A Beginner’s Guide!
What is Cloud Computing in Simple Terms? To tell you the …
Hacking Web Applications – Ethical Hacking | Certified Ethical Hacker | Best CEH V11 Tutorial
Hacking Web Applications – Ethical Hacking | Certified Ethical Hacker | …
DVWA – Brute Force – Ethical Hacking | CEH V11 Tutorial Free Ethical Hacking Training
DVWA – Brute Force – Ethical Hacking | CEH V11 Tutorial …
Python Packages – Python Training | Python Programming for Beginners Video Tutorial
Python Packages – Python Training | Python Programming for Beginners Video …
What is Session Hijacking and How Does It Works? [2025]
As the term suggests, Session Hijacking, which is also famous as …
Installing and Updating Software Packages – RedHat Training
Installing and Updating Software Packages – RedHat Training Installing and Updating …
What is SQL Injection and How It Works?
What Are SQL Queries? An SQL injection is a cyber attack …
Beginner to Advance Penetration Testing Course in Delhi
Beginner to Advance Penetration Testing Course In order to understand the …
Best Ethical Hacking Course Online In India
Ethical Hacking Course Online in India With the help of many …
Online Cyber Security Course with Certification in India [2025]
Introduction to Cybersecurity We all know that cybersecurity is no longer …
Pink whats app virus links fake or real
Pink, what’s app virus links fake or real cyber security expert …
Domino’s hacked in India. 10 lakh Users Details Leaked like Emails, Phone Number
Hacking News : Domino’s Database leaked in India Domino’s hacked in …
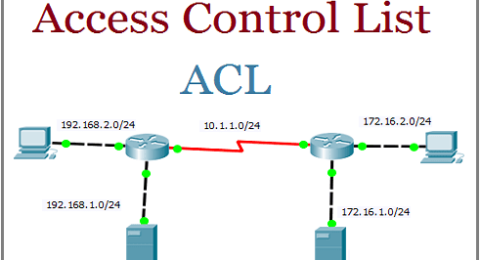
Understands The Access Control List in Networking
What is an access control list (ACL)? An access control list, …
Network Switch: Managed vs Unmanaged
Managed vs. Unmanaged Switches: What are the Differences? Introduction: The control …
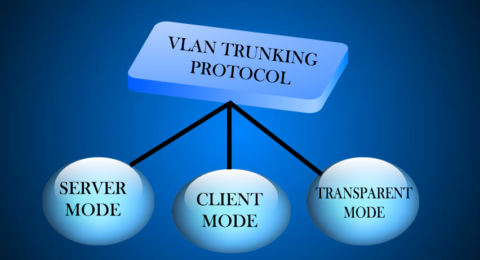
Understanding VLAN Trunking Protocol | CCNA Study
Understanding VLAN Trunking Protocol (VTP) One must first configure the switch …
Best Cyber Security Course Institute in Delhi
Best Cyber Security Training Institute in Delhi With the transition of …