Learn End Point Security Course in Delhi
June 17, 2021 2025-03-30 11:22Learn End Point Security Course in Delhi
End Point Security Course with AI in Delhi | Best Endpoint Security Certification
Bestseller
1900+ Student Reviews
Although it is a wonderful experience for humanity to live in a world full of internet-based smart devices that operate independently using various AI and machine learning concepts, it is also important to realize that protecting the entry and endpoints of IoT (Internet of Things) devices is the most difficult situation to handle. Additionally, this adaptable Endpoint Security Course with AI from the most authentic cybersecurity school, Craw Security, with locations in Saket and Laxmi Nagar, provides the charm that increases students’ validation when they go for interviews in prestigious IT companies.
- Course Duration : 60 Hours
- Language : Hindi | English
- Course Delivery : Online | offline

FutureSkills Prime Partner (A MeitY NASSCOM Digital Skilling Initiative)
Accredited by NASSCOM, approved by the Government of India
Book a Trial Demo Class
Training Available 24*7 Call at 9513805401
What will you learn in Endpoint Security Course with AI in Delhi?
Since network threats frequently impact the weakest link in a network’s security, protecting the security of the entry and endpoints is one of the most important aspects of the network to defend. As a result, Craw Security has developed an authentic Endpoint Security Course with AI curriculum that includes all the necessary materials for anyone interested in Endpoint Security Training in Delhi.
Additionally, this particular Endpoint Security Course with AI curriculum will enable you to fully comprehend all of the core ideas related to the Best Endpoint Security Certification and Training.
As a result, candidates must sign up for the Endpoint Security Course with AI, which is offered both online and offline through instructor-led interactive classroom sessions and by top-notch teaching faculty and mentors in a safe and convenient setting.
Book a Trial Demo Class
Training Available 24*7 Call at +91 9513805401

Endpoint Security Course Content
Lesson 01: Importance of Internet Security
Lesson 02: Malware
Lesson 03: Antivirus protection
Lesson 04: Internet security tips to know
Lesson 01: Three Main Types of MFA Authentication Methods
Lesson 02: How Multi-Factor Authentication Works
Lesson 03: MFA Examples
Lesson 04: Two-Factor Authentication (2FA)
Lesson 05: Adaptive Authentication or Risk-based Authentication
Lesson 01: What is mobile device management
Lesson 02: How mobile device management works
Lesson 03: Application security
Lesson 04: Identity and access management (IAM)
Lesson 05: Endpoint security
Lesson 06: BYOD mobile device management
Lesson 01: DLP Basics
Lesson 02: Who use DLP
Lesson 03: Why we need DLP
Lesson 04: How does DLP works
Lesson 05: DLP solutions
Lesson 01: Introduction to AI in SIEM
Lesson 02: AI-Enhanced Indexing
Lesson 03: AI-Powered Analysis logs and Alerts
Lesson 04: AI-Driven Dashboard creation
Lesson 05: AI for Event TypeClassification and Prediction
Lesson 01: What is APT Attack
Lesson 02: Advanced persistent threat (APT) progression
Lesson 03: APT security measures
Lesson 04: Application and domain whitelisting
Lesson 05: Access control
Lesson 01: Introduction to Mitre
Lesson 02: Matrix
Lesson 03: Tactics
Lesson 04: Techniques and Sub-Techniques
Lesson 05: Mitigation
Lesson 01:Introduction to AI in EDR/XDR
Lesson 02: AI-Enhanced Common EDR/XDR Products
Lesson 03:AI-Powered Process Termination and Threat Mitigation
Lesson 04:AI-Driven Endpoint Management with EDR/XDR
Lesson 05: Integrated Use Cases: AI in SIEM, EDR, and XDR
Lesson 01: Introduction to Unified Threat Management
Lesson 02: Feature of UTM
Lesson 03: Benefit of using UTM Solution
Lesson 01:Introduction of AI in Firewall
Lesson 02:AI-Powered Reasons behind the need for Firewalls
Lesson 03:AI for Modern Firewalls
Lesson 04:AI Reinforced Basic firewall technologies
Lesson 05:AI-based Next Gen Firewalls
Talk to Our Course Advisor
Endpoint Security Fundamental Course | Best Online Endpoint Security Course with AI
The principles properly taught in the Endpoint Security Course with AI are always taken into consideration when it comes to protecting the entry and exit points of an IoT device loop. Therefore, learning this important and delicate Endpoint Security Course with AI from a reputable and validated university that offers you a lasting educational experience from the most flexible and subject matter experts as faculty members are always required.
The more you recall the Endpoint Security Fundamental Course, the more you will benefit from its real-world effects while protecting IoT device loops and endpoints, network security, a target website, or any other IT infrastructure that could be the focus of a determined hacker.
In addition, Craw Security provides the Best Online Endpoint Security Course with AI, which gives students who are waiting for the ideal online security course the opportunity to study at their own pace.
Key specifications to End Point Security Training in Delhi:
- Implementing Internet Security Anti Virus.
- Mobile Device Management For Industry
- Security Information and Event Management
- Two-Factor Authentication Implementation
- Data Loss Prevention Overview & Implementation
- Unified Threat Management
- Next-Generation Firewall
- ISO 27001 Lead Auditor Guidelines
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
Endpoint Security Course Description
From the person standing in the middle of a metropolis with a smartphone in hand to the person living in a far-off village, we can claim that the advancement of technology has had a significant impact on everyone’s life.
In this specialized Endpoint Protection Training from Craw Security’s cutting-edge campuses in Saket and Laxmi Nagar, highly qualified instructors and trainers on the job teach all the essential fundamentals and concepts using the newest technology and equipment.
One will fully understand the Endpoint Security Planning tools and techniques as well as the foundations associated with our top-ranked Cyber Security Institute of Craw Security’s best-in-class Endpoint Security Course with AI Training in the NCT of Delhi, thanks to excellent instructors and mentors carrying out the honors.
Craw Security's Students Awarded











Related Cyber Security Course
Latest Blogs
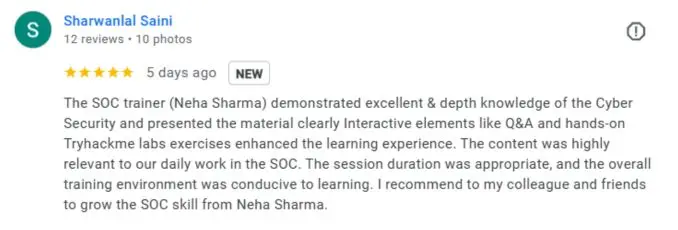
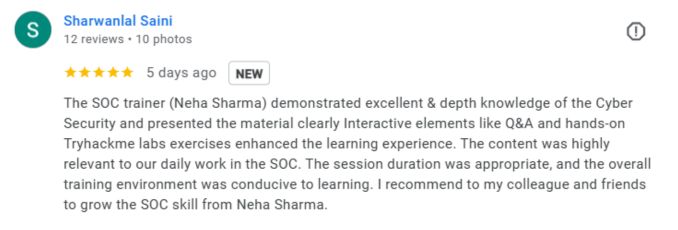
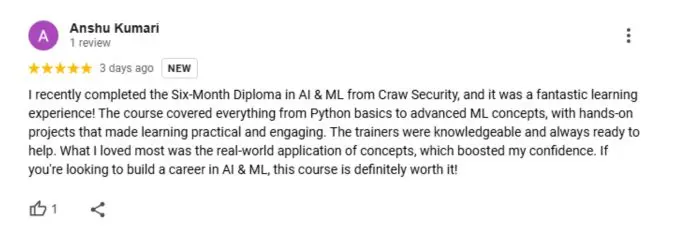
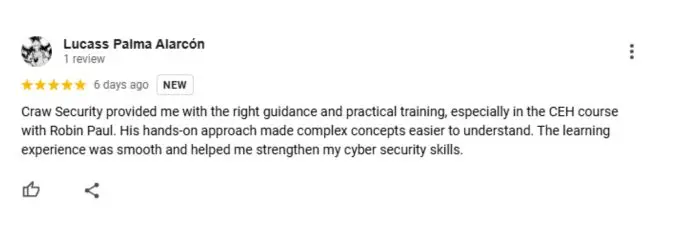
What People Are Saying About Craw Security
Google Review (1900+) ★★★★★
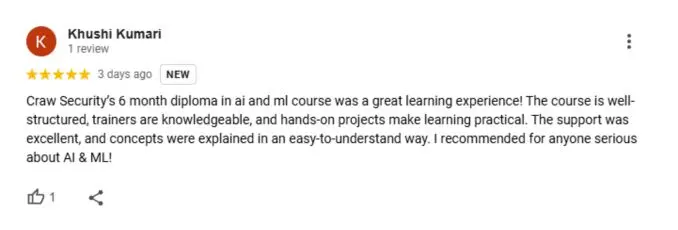
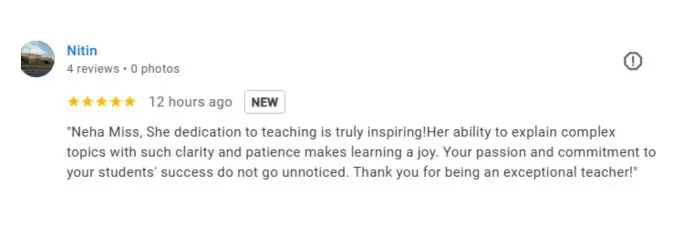
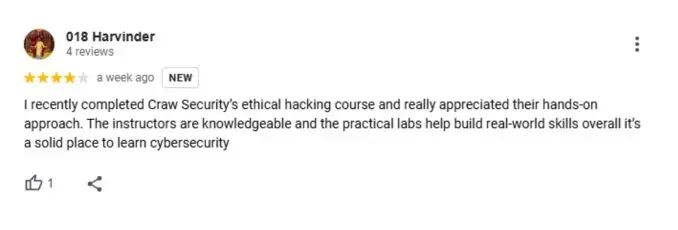
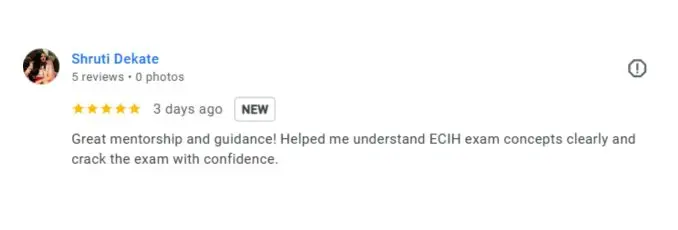
List of Companies you can get placements in

Endpoint Security Frequently Asked Questions
Endpoint security is the primary practice of preventing malevolent individuals and entities from compromising the entry points or endpoints of end-user IoT devices, including desktops, laptops, and smartphones. Endpoint security systems often protect these endpoints on a cloud server or preferred network from cyberattacks and other cybersecurity risks.
In order to protect end-user IoT devices from malevolent individuals, campaigns, and entities, there are up to eleven different types of endpoint security methods. Below are a few examples of specific Endpoint Security categories:
- Internet of Things (IoT) Security.
- Antivirus Solutions.
- Endpoint Detection and Response.
- URL Filtering.
- Application Control.
- Network Access Control.
- Browser Isolation.
- Cloud Perimeter Security.
An antivirus program protects a personal system or device from being compromised by an unexpected cyberattack or malicious campaigns, whereas endpoint security software protects all network endpoints from various threats and cyberattacks. This is the main distinction between the two types of software.
A working professional can genuinely secure the endpoints using a number of specific techniques, such as the methodology below, which is strongly advised to protect the entry and endpoints of an end-user IoT device:
- Do the basics well.
- Recognize your endpoints.
- Install Automated and Advanced Endpoint Security.
- Set detection and response priorities and automate the process.
- Employees should be your ally.
These days, the market offers a wide range of Endpoint Protection services. Nevertheless, I advise you to attempt the following fixes:
- The Bit Defender GravityZone Advanced Business Security Antivirus program is available for free in its beta form, but after it is installed on your computer, you will be prompted to purchase the skippable premium version.
- Business antivirus software from Avast.
- ESET PROTECT. A complete endpoint security package.
- Security of Panda WatchGuard Endpoints.
A specialized API management system that helps an end-user protect, build, regulate, analyze, and manage quotas on your APIs is known as an endpoint in the cloud. Your APIs are hosted by the Endpoints using the Extensible Service Proxy (ESP) or Extensible Service Proxy V2 Beta (ESPv2 Beta).
Endpoint security tools are specialized software programs designed to identify, monitor, and manage the many endpoint devices that a company uses, including desktop computers, laptops, tablets, and smartphones. For example, Palo Alto Networks Cortex XDR, Trend Micro Apex One, F-Secure Rapid Detection & Response, Crowdstrike Falcon, etc.
- Step One: Triage and Prioritize Resources. Regularly run vulnerability scans of known assets for weaknesses and vulnerabilities, cross-referencing against asset lists. …
- Step Two: Automate. Automation is the key to maximizing resources. …
- Step Three: Have (and Practice) Your Plan. …
- Step Four: Learn From Your Incidents.









