EC-Council Web Application Hacking Security Certification (WAHS)
January 10, 2023 2025-07-08 18:07EC-Council Web Application Hacking Security Certification (WAHS)

EC-Council Web Application Hacking & Security Certification (WAHS)
Bestseller
2000+ Student Reviews
Enroll now to transform your basic web application knowledge with the help of EC-Council WAHS Certification or Web Application Hacking Security facilitated by Craw Security’s high-end mentorship at Saket and Laxmi Nagar’s state-of-the-art elevations. With the help of world-class training instructors having many years of authentic experience, Craw Security is offering its immense qualitative training under the strict supervision of professional instructors. Become a person who is entirely responsible for handling web application hacking and security protocols with this Web Application Security Professional.
- Course Duration : 40 Hours
- Language : Hindi | English
- Course Delivery : Online | offline
Book a Trial Demo Class
Training Available 24*7 Call at 9513805401
Web Application Hacking and Security (WAHS) Course Overview
Initially, Web Application Hacking Security has several challenges that are derived from the engrossing iLab ecosystems of EC-Council, right from the EC-Council CEH to the Certified Penetration Testing Professional (CPENT) Certification from Certified Application Security Engineer (CASE) .Net to Java. However, web application hacking security leads further to more intricate scenarios as you rise through every problem.
Furthermore, the Web Application Hacking Course and Capture-the-Flag (CTF) tournaments, which test your hacking skills, are very similar. Nonetheless, you may easily keep up your speed by making an effort to verify your goal. Regarding this, you can either follow the teacher during a walkthrough to help you understand Certified Web Application Hacking Security (WAHS) or put your talents to the test and work alone to control complicated worries.
EC-Council WAHS Course Content
Module 01: Advanced Web Application Penetration Testing
Module 02: Advanced SQL Injection (SQLi)
Module 03: Reflected, Stored and DOM-based Cross Site Scripting (XSS)
Module 04: Cross Site Request Forgery (CSRF) – GET and POST Methods
Module 05: Server-Side Request Forgery (SSRF)
Module 06: Security Misconfigurations
Module 07: Directory Browsing/Bruteforcing
Module 08: Network Scanning
Module 09: Auth Bypass
Module 10: Web App Enumeration
Module 11: Dictionary Attack
Module 12: Insecure Direct Object Reference Prevention (IDOR)
Module 13: Broken Access Control
Module 14: Local File Inclusion (LFI)
Module 15: Remote File Inclusion (RFI)
Module 16: Arbitrary File Download
Module 17: Arbitrary File Upload
Module 18: Using Components with Known Vulnerabilities
Module 19: Command Injection
Module 20: Remote Code Execution
Module 21: File Tampering
Module 22: Privilege Escalation
Module 23: Log Poisoning
Module 24: Weak SSL Ciphers
Module 25: Cookie Modification
Module 26: Source Code Analysis
Module 27: HTTP Header modification
Module 28: Session Fixation
Module 29: Clickjacking
Talk to Our Course Advisor
What is Web Application Hacking Security (WAHS)?
This highly affiliated training for Certified Web Application Security Professionals is the best one you can choose to learn Web Application Hacking Security certification right from the best cyber security training institute in India, and that is Craw Security. In this regard, EC-Council WAHS Certification or Web Application Hacking and Security is the best fit in the current market that is coming from the House of EC-Council.
In addition to this, it is also the only experiential curriculum that provides a wealth of knowledge and only employs hands-on learning. Many cybersecurity professionals also find it helpful in understanding, testing, hacking, and protecting web applications from emerging and present security risks. Consequently, this proactive program — which was created and refined by multiple professionals from various firms across the globe — allows one to learn about web application hacking techniques and application vulnerabilities.
Moreover, students will certainly be amazed to know that at Craw Security, there are plenty of other training and certifications from the House of EC-Council and other prominent houses that provide information security courses with sources rich in informational material.
Who Should Do This EC-Council WAHS Certification?
- Persons inclined with implementing, managing, or protecting web applications.
- Individuals who are cybersecurity or tech experts duly interested in learning mitigation protocols for a myriad of web security issues and wish for a pure practical program.
- Other varied individuals are willing to learn web application hacking security programs.
As we can generally understand this WAHS Certification comes from the House of EC-Council, which is a tech supergiant in the modern world, facilitating the world with many vendor-neutral cybersecurity programs and certifications. Hence, it is pretty sure that if a person completes this world-class training in Web Application Hacking Security from its accredited training partner – Craw Security, the same will not face difficulty in finding a maiden job at much sense.
Instead, there are many chances that the same would get placed before one gets a hand on the certificate from the EC-Council for the same course. Subsequently, as mentioned on the official website of the EC-Council, Penetration testers’ salaries range from $57,000 to $134,000, depending on the IT security analyst’s experience level.
Moreover, several dedicated job opportunities are there that a person can opt for after certainly completing the EC-Council’s Web Application Hacking Security Program. Some of them are mentioned below:
Job Experience | Job Roles | Job Profiles |
Beginner | Cybersecurity Technician | IT Support Specialist, IT Networking Specialist, Cybersecurity Technicians, Network Engineers, SOC Analyst |
Core | Network Security | Entry-level Network Administrators, Entry-level Network Security Administrators, Data Security Analyst, Junior Network Security Engineer, Junior Network Defense Technician, Security Analyst, Security Operator, Network Security Engineer |
Ethical Hacking | Mid-Level Information Security Auditor, Cybersecurity Auditor, Security Administrator, IT Security Administrator, Cyber Defense Analyst, Vulnerability Assessment Analyst, Warning Analyst, Information Security Analyst L1, Security Analyst L1, Infosec Security Administrator, Cybersecurity Analyst L1, L2, & L3, Network Security Engineer, SOC Security Analyst, Security Analyst, Network Engineer, Senior Security consultant, Information Security Manager, Senior SOC Analyst, Solution Architect, Cybersecurity Consultant | |
Specialization | Penetration Testing | Penetration Testers, Network Server Administrators, Firewall Administrators, Security Testers, System Administrators and Risk Assessment professionals, Cybersecurity Forensic Analysts, Cyberthreat Analysts, Cloud Security Analysts, Information Security Analysts, Application Security Analysts, Cybersecurity Assurance Engineers, Security Operations Center (SOC) Analyst, Technical Operations Network Engineer, Information Security Engineer, Network Security Penetration Tester, Network Security Engineer, Information Security Architect |
Application Security | Application Security Engineer, Application Security Analyst, Application Security Tester, Application Security Consultant, Application Security Specialist, Secure SDLC Engineer, Security Engineer-Secure SDLC, Security Engineer-Application Security |
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class
One can also opt for the prerecorded video sessions available at any point of time from any particular location.

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
Craw Security's Students Awarded











Related Cyber Security Course
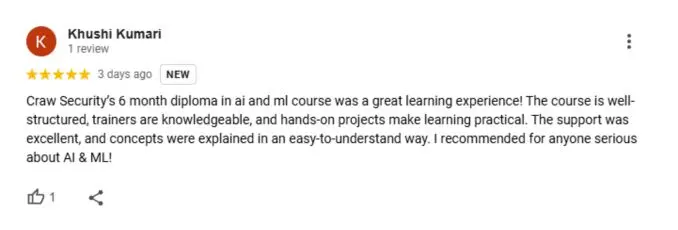
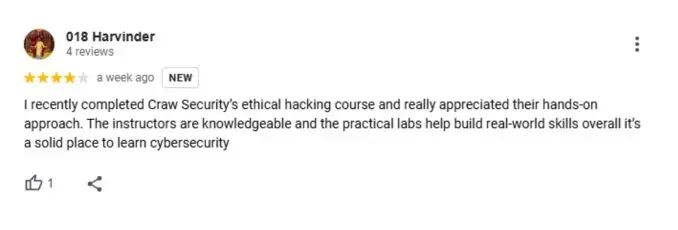
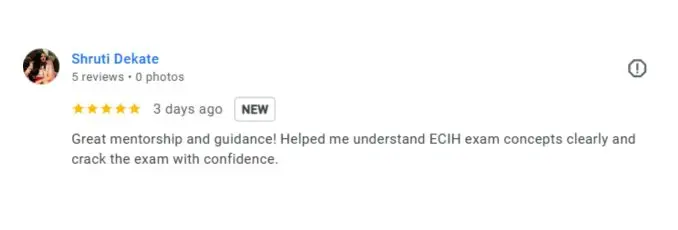
What People Are Saying About Craw Security
Google Review (2000+) ★★★★★
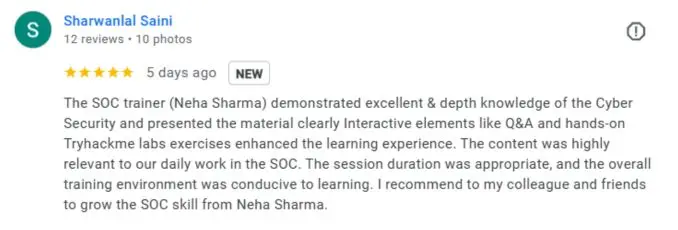
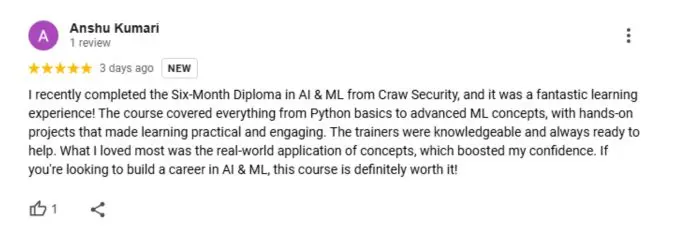
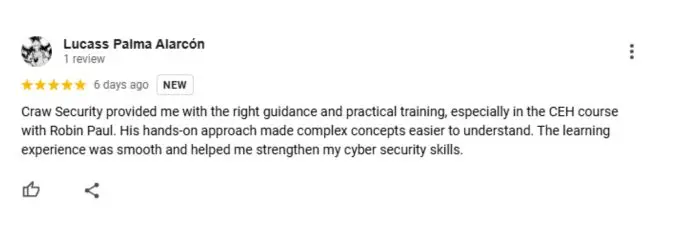
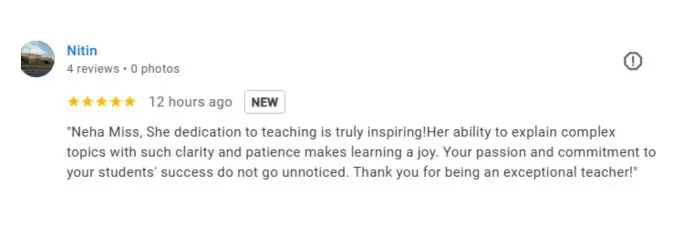
Frequently Asked Questions
About Web Application Hacking Security
Yes, a web application can be hacked. Hackers typically use malicious code, such as viruses, worms, and Trojan horses, to gain access to a web application. Additionally, hackers may exploit vulnerabilities in the application itself, such as weak passwords, insecure coding practices, and unpatched software.
Web application security is a branch of cyber security that focuses on protecting websites, web applications, and web services from malicious attacks. It is an important part of an organization’s overall security program and involves a comprehensive set of security measures designed to protect websites, web applications, web services, and their associated data from unauthorized access, misuse, and modification. These measures include input validation, output encoding, authentication, and authorization. Web application security also involves monitoring and testing to ensure that security measures are effective and up to date.
By using the following protocols, anyone can save web applications from being compromised:
- Secure authentication
- Input validation
- Encrypt sensitive data
- Implement access control
- Use a web application firewall
- Monitor and log activity
- Perform regular security scans
Web application vulnerabilities are security weaknesses commonly found in web applications, such as web browsers, web servers, and web services. These vulnerabilities can be exploited to gain unauthorized access to sensitive data, cause a denial of service, or perform malicious code injection. Common web application vulnerabilities include cross-site scripting (XSS), SQL injection, broken authentication, and insecure direct object references.
Some basic web application attacks are as follows:
- SQL Injection
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- Buffer Overflows
- Malicious File Execution
- Password Attacks
- Privilege Escalation
The most common way web applications are hacked is through injection attacks, such as SQL injection. Injection attacks are used to gain access to a website’s database and potentially sensitive information. Other common web application hacking techniques include cross-site scripting (XSS), remote file inclusion (RFI), and cross-site request forgery (CSRF).
Web application security is important because it helps protect websites and the sensitive data stored on them from malicious attacks. These attacks can be devastating, causing financial losses, loss of customer trust, and reputational damage. Web application security can help to protect against malicious attacks, such as SQL injection, cross-site scripting, and session hijacking, as well as other types of threats. It is also important to ensure that websites are regularly updated to patch any security vulnerabilities.








