Mobile Application Security Course in Delhi
June 11, 2021 2025-07-08 18:19Mobile Application Security Course in Delhi
Mobile Application Security Course with AI in Delhi
Bestseller
2000+ Student Reviews
Learn Mobile Application Security Course with AI in Delhi from the world-class teaching fraternities and mentorship via experienced mentors providing authentic live classroom sessions at Saket and Laxmi Nagar locations of Delhi. During this Mobile Application Security Course with AI, one will learn the most important tools and techniques duly employed to detect any kinds of vulnerabilities and threats associated with a concerning target Mobile Application. After completing Mobile Application Security Training in Delhi, one can genuinely find good positions in leading IT organizations.
- Course Duration : 60 Hours
- Language : Hindi | English
- Course Delivery : Online | offline

FutureSkills Prime Partner (A MeitY NASSCOM Digital Skilling Initiative)
Accredited by NASSCOM, approved by the Government of India
Book a Trial Demo Class
Training Available 24*7 Call at 9513805401
What will you learn in Mobile Application Security Course with AI in Delhi?
Through the exclusively constructed methodologies associated with the Mobile Application Security Course with AI, the trainers at Craw Security provide their authentic self-made techniques to describe the most complex topics of the Mobile Application Security Course with AI.
Many institutes are widely present in the market nowadays and are providing versatile Mobile App Security Training including the useless courses in the package which are certainly not necessary. On the other hand, Craw Security offers its top-notch mentorship with experienced trainers on the job to train our undergraduates with the detailed and exact knowledge that one is required to process in the corresponding Mobile Application Security Course with AI.
Book a Trial Demo Class
Training Available 24*7 Call at +91 9513805401

Mobile Application Security Course Content
Lesson 01: Scope
Lesson 02: Methodology
Lesson 03: Tools
Lesson 01: Kali lab setup
Lesson 02: Burp suite setup
Lesson 03: Mobile penetration testing lab setup
Lesson 01: Layers of Android architecture
Lesson 02: Key Components
Lesson 03: Application lifecycle
Lesson 04: Security Model
Lesson 01: Core components
Lesson 02: Common file structure patterns
Lesson 03: File structure example
Lesson 01: Overviews
Lesson 02: Functionality
Lesson 03: Installation
Lesson 04: Usage
Lesson 05: Common usage case
Lesson 01: Overviews
Lesson 02: Functionality
Lesson 03: Installation and setup
Lesson 04: Feature and Capabilities
Lesson 05: Scan the app with mobsf
Lesson 01: Types of static analysis
Lesson 02: Tools and techniques
Lesson 03: Benefits
Lesson 04: How to perform static analysis
Lesson 01: Overviews
Lesson 02: Dynamic analysis
Lesson 03: Injection attacks
Lesson 04: Exploitation
Lesson 01: Definition
Lesson 02: attacks
Lesson 03: Impact
Lesson 04: Mitigation
Lesson 05: Tools and resources
Lesson 01: Definition
Lesson 02: Storing passwords in plain text
Lesson 03: Unprotected databases
Lesson 04: Impact
Lesson 05: Mitigation
Lesson 06: Tools and resources
Lesson 01: Definition
Lesson 02: Unencrypted protocols
Lesson 03: Missing or misconfigured SSL/TLS
Lesson 04: Impact
Lesson 05: Mitigation
Lesson 06: Tools and resources
Lesson 01: Definition
Lesson 02: Weak password policies
Lesson 03: Lack of multi-factor authentication
Lesson 04: Impact
Lesson 05: Mitigation
Lesson 06: Tools and resources
Lesson 01: Common vulnerability
Lesson 02: Impact
Lesson 03: Prevention and Mitigation
Lesson 04: Continuous monitoring and updates
Lesson 01: Common vulnerability
Lesson 02: Impact
Lesson 03: Prevention and Mitigation
Lesson 01: Important of client code quality
Lesson 02: Code structure and Organization
Lesson 03: Readability and Maintainability
Lesson 01: Objective
Lesson 02: Techniques
Lesson 03: Detection and Prevention
Lesson 04: Implications
Lesson 01: Purpose
Lesson 02: Techniques
Lesson 03: Tools
Lesson 04: Reversing Malware
Lesson 01: Security risks
Lesson 02: User Experience (UX) issues
Lesson 03: Code review and refactoring
Lesson 04: Automated Analysis tools
Lesson 01: Public key Pinning
Lesson 02: Certificate Pinning
Lesson 03: Benefits of SSL pinning
Lesson 04: Certificate Authority (CA)
Lesson 01: Packet Capture
Lesson 02: Network sniffing
Lesson 03: Protocol Analysis
Lesson 04: Traffic Decryption
Lesson 01: Introduction to Dynamic Analysis
Lesson 02: How to perform dynamic analysis
Lesson 03: Dynamic Debugging
Lesson 04: Dynamic Decomplication
Lesson 01: Consider the objective of the report
Lesson 02: The test compiles a comprehensive report
Lesson 03: Detailing their findings of vulnerability
Lesson 01: Introduction to IOS Penetration testing
Lesson 02: IOS structure
Lesson 03: How to secure you application
Lesson 01: Proof of Concept (POC)
Lesson 02: Executive and Management Report
Lesson 03: Technical Report For IT and security department
Talk to Our Course Advisor
Mobile Security Certification Course
Firstly, Mobile Application Pentesting is the initial key to tracking down all the available security breaches, threats, and vulnerabilities present in a corresponding target Mobile Application. With a thorough process of Mobile Application Pentesting, one can sincerely learn all the essential aspects associated with the Mobile Security Certification Course that can transfer all the needed knowledge to counter all the issues and concerns related to Mobile Application Security protocols.
What is the Training Objective of Mobile Application Security?
- Secure Mobile Applications Security from specialized and business rationale viewpoints.
- Distinguish business rationale and specialized weaknesses in your Mobile application’s security.
- Understand real-world attack techniques.
- Catch the business rationale stream of the Mobile Application Security.
- Distinguish the application’s weaknesses that can be abused utilizing introduced applications on cell phones.
- Evaluate cell phone security issues.
- Test and find weaknesses present in cell phones, Mobile applications, workers, and the organization.
Key specifications of Mobile Application Security Course with AI
- Understand Mobile Application Threats and Vulnerabilities.
- Implement Mobile Application Controls and Protocols.
- Design and Implement Mobile Security Policies.
- Learn fundamentals of Mobile Application and Defense Techniques.
- Real-Time Application Analysis.
- Practicals on Vulnerable Mobile Application.
- Malware Protection – Permission.
- Ensure and Manage VPN Security.
- Secure Wireless Networks.
- Monitor and Analyze Mobile Session Traffic.
- Understand mobile Application Risks and Vulnerabilities.
- Mobile Application Incident Response and Management.
- Define Physical Security Controls and Authentication Techniques.
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
Mobile Application Security Course Description
In the vast and in-depth curriculum associated with Mobile App Security Training from the dedicated institutions of Craw Security at Saket and Laxmi Nagar branches, one will learn most of the important tools and techniques used for the security of your Mobile Devices and Applications.
During this course, with the help of its high-tech trainers and experienced mentors Craw Security offers world-class AI-based Mobile Application Security Training in Delhi that can hardly be found anywhere else in the vicinity of NCT of Delhi.
Within this magnificent Mobile Application Security Course with AI in Delhi, a Security Enthusiast will learn the most authentic and practical methodologies associated with the security concerns associated with mobile devices and apps.
After completion of this splendid Mobile Application Security Course with AI, one will be able to test vulnerabilities hidden in a particular target mobile application and submit the same to the concerned authorities with utmost ease factor, and proficiency.
Nowadays, Mobile has become an integral part of all our lives, and since all the major and minor organizations have made their own mobile applications to let their clientele connect with them at any point in time, we have constructed an in-depth curriculum that provides the finest Mobile Application Security Course with AI in Delhi through the verified and authenticated Mobile Security Syllabus.
In today’s day and age, it has become the need of the hour for our mobile to be totally secured against malfunctions and vulnerabilities. Craw Security offers a quality Mobile Application Security Course with AI in Delhi, which provides you with a brief overview of Mobile Architecture and the nitty-gritty of Mobile Application Security. After the completion of this specific Mobile Device Training Course, the students will be able to remove vulnerabilities and threats from their mobile.
One can also find all the technical details associated with this magnificent Mobile Application Security Course with AI in an online format with self-paced learning mode availability.
The various Mobile Application Security Courses with AI Tools that are available and taught at the premises of Craw Security are as follows:
- Apktool,
- JADX,
- JD-GUI,
- Dex2Jar,
- Bytecode-viewer,
- Androguard,
- Androbug,
- Mob-SF,
- MARA Framework,
- Drozer,
- Burp Suite Professional,
- Burp Suite Mobile Assistant,
- Objection,
- QARK,
- Frida, etc.
Various aspirants can sincerely join this splendid Mobile Application Security Course with AI at the earliest described below:
- Security Enthusiasts,
- IT professionals, and
- Mobile Application Developers who want to learn about mobile application security issues in detail.
Craw Security's Students Awarded











Related Cyber Security Course
Latest Blogs
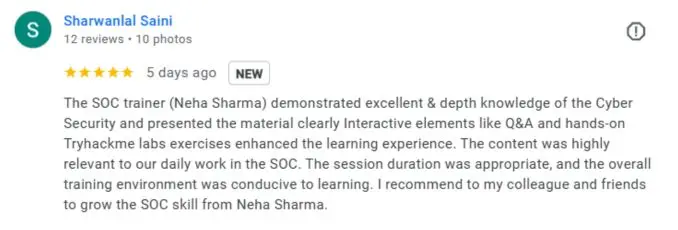
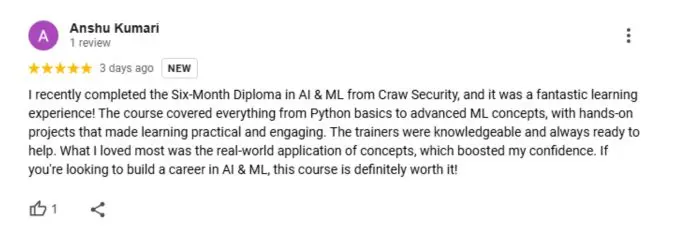
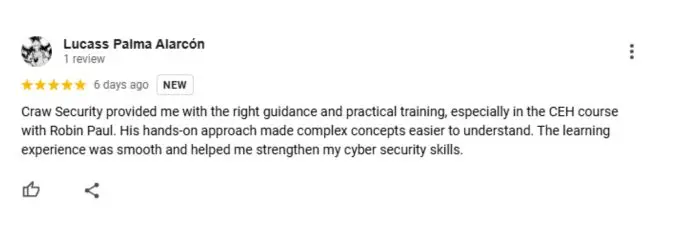
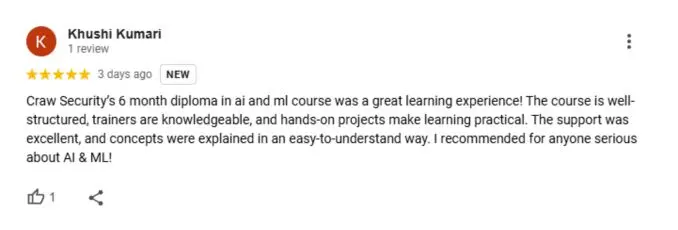
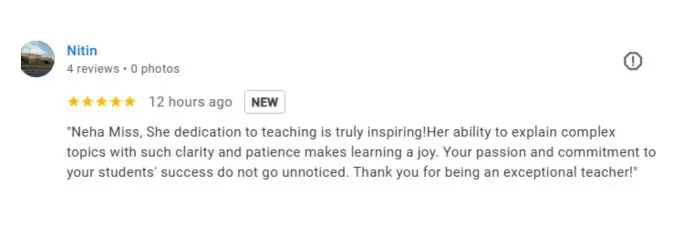
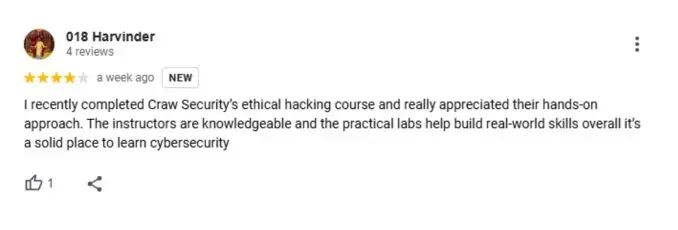
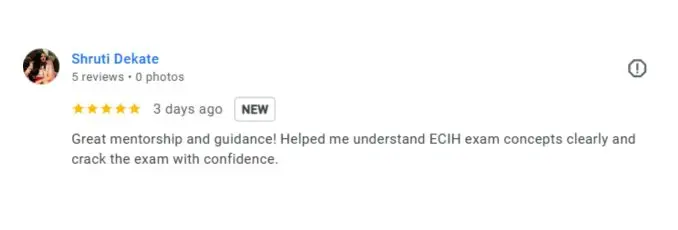
What People Are Saying About Craw Security
Google Review (2000+) ★★★★★
Mobile Application Security with AI Frequently Asked Questions
There are many security techniques available that can be employed to safeguard an application with the safest methods, such as the following:
- Source Code Encryption,
- Penetration Tests – Perform a Thorough QA & Security Check,
- Secure the Data-in-transit,
- File-Level & Database Encryption,
- Employing the Latest Cryptography Techniques,
- High-level Authentication,
- Secure the Backend,
- Minimize Storage of Sensitive Data, etc.
One can understand the widely-known mobile application security threats as follows:
- Insecure Communication,
- Lack of Input Validation,
- Insecure Data Storage,
- Client Code Security,
- Insufficient Authentication and Authorization Controls,
- Poor Encryption,
- Reverse Engineering, etc.
The Android Application Security can be defined as the numerous methodologies associated with mobile application software development that is being used by its AI program to forbid access to resources in case it is used incorrectly or maliciously, or any other distinguished forms by which a concerning mobile application can be compromised.
Since all the major and minor websites are becoming mobile-friendly and bringing their hard-earned database to the mobile applications’ interfaces, they are becoming the prime targets of illicit hackers who have ill intentions to steal all the sensitive and crucial information encrypted in the servers of those concerning mobile applications.
We can genuinely say that there are multiple kinds of databases stored in the respective servers of mobile applications such as personal files, banking credentials, sensitive customer information, and many more which can single data breach can compromise.
The prominent Application Security is the methodology of crafting, developing, adding, and testing security aspects within the concerning applications to hinder security vulnerabilities like illegitimate access and alteration.
According to various studies conducted by several independent researchers and organizations, it seems that iPhone and iPad users are more secure than Android users all around the globe. The two platforms have distinguishably different in terms of their security concerns, working functions, complexity factors, etc.
There are certain practices that one can employ to confirm the security status of one’s Android device’s applications to some certain level. Some of them are defined below:
- Always install apps from secured and authorized sections such as Play Store, App Store, etc.
- Always give permissions to the apps after reading the T&C sections so precisely which may contain some unwanted access to the application which may lead to data theft or anything more malicious.
- Never use public Wi-Fi, which may give unauthorized access to malicious actors on your Android devices.
- Secure your android device from proper password/ pin protection. One may also use the Iris scanner or voice scanner in order to confirm the identity of the intended user.
A mobile application, or an app, is some kind of software application dedicatedly designed by an organization to run on mobile devices (whether Android or iOS), computer, or tablet devices. The main purpose of mobile applications is to quickly resolve the users’ intended problems and serve with the conclusions in the shortest possible time.
Mobile Application Security Testing is commonly known as Mobile AST or Mobile Application Pentesting. It is defined as the process in which a security analyst performs a series of events that evaluates the corresponding vulnerabilities, threats, and loopholes in a targeted mobile application used with distinguished mobile platforms or devices such as iOS, Android, and Windows Mobile in-process or post-development.
To know more about the upcoming batches and other crucial info regarding the same course or any other course mentioned on the official website of Craw Security, kindly give us a call at our hotline mobile number at +91-9513805401 and have a chat with our superb educational consultants.
Mobile application security encompasses the range of actions implemented to safeguard mobile applications from potential risks and weaknesses that may jeopardize the privacy, reliability, and accessibility of both the application itself and its associated data. Monitoring the security of mobile devices and applications is of utmost importance due to their extensive usage and the sensitive data they frequently handle.
Enrolling in a course on mobile application security in Delhi or any other prominent urban center might be deemed a strategic choice for various compelling rationales. There are several strong justifications pertaining to the security of mobile applications and their geographical positioning.
- Increasing Demand for Mobile Apps,
- Tech Hub,
- Practical Skills,
- Career Opportunities,
- Competitive Edge,
- Local Relevance,
- Networking Opportunities,
- Rising Cyber Threats,
- Higher Pay,
- Future-Proofing, etc.
While there are no specialized prerequisites required to join this highly credible Mobile Application Security Course in Delhi by Craw Security, you may fulfill the following desirable requirements to seek admission in this course:
- Basic Understanding of Mobile Platforms,
- Programming Knowledge,
- Understanding of Basic Cybersecurity Concepts,
- Networking Concepts,
- Web Technologies,
- Previous IT or Tech Experience,
- Hands-on Experience,
- Willingness to Learn, etc.
At Craw Security, the Mobile Application Security Course in Delhi tends to possess a 60-hour long duration.
Yes, this prominent Mobile Application Security Course by Craw Security offers both hands-on lab exercises and practical sessions under the prime supervision of world-class training mentors.
The fee structure for the Mobile Application Security Course in Delhi by Craw Security is highly dependent on the market conditions as we do provide this corresponding course at a very competitive price range that is harder for you to find anywhere else.
Call at +91-9513805401 for more details.
No, there will be no specialized tools or software needed to participate in this Mobile Application Security Course.









