The Benefits of Implementing the XDR Security Solution | Shield XDR
The Benefits of Implementing the XDR Security Solution | Shield XDR
Are you also searching for XDR Security Solution Provider in India? Then you are at the right place for the services you long for. Now that cyberattacks are rising, one definitely needs to protect their resources against such threats.
Extended Detection and Response Security can help an organization/ individual/ client secure confidential data through various tools and tech. But how does it work for the benefit of the user? For that, you can read this article from beginning to end. Let’s continue!
What is XDR?
XDR’s full form is Extended Detection and Response. It’s a group of security measures to improve company threat detection, response, and prevention facilities.
XDR combines several security measures into a single platform, including
- EDR
- NTA
- SIEM, and
- Threat Intelligence.
By assessing data from various sources, XDR offers a comprehensive overview of a firm’s security posture allowing rapid threat detection and response across the whole IT Infrastructure.
To identify and prioritize potential threats, look into occurrences and plan responses, XDR uses advanced analytics, machine learning, and automation. The XDR Threat Detection and Response can raise the room for improvement in detecting threats beforehand.
Moreover, the XDR Endpoint Protection can secure conversations between the receiver and the sender. The Deep Security XDR can annihilate the ways through which adversaries can trespass into the system and can have unauthorized access. Organizations will be able to work effectively without worrying about data confidentiality. Let’s continue!
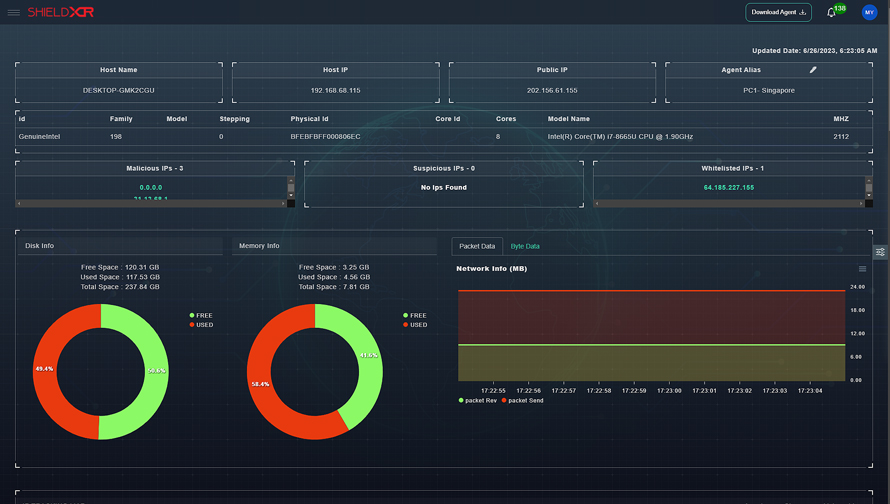
Why Is XDR Important?
- Enhanced Threat Detection
Data from many security sources, including endpoints, networks, and cloud environments, is combined and correlated by XDR. Better identification of complex threats across several access points is made possible by this comprehensive viewpoint.
XDR can identify suspicious behaviors, anomalies, and indicators of compromise more precisely than individual security solutions by analyzing and correlating data in real-time.
- Faster Incident Response
By giving security personnel broad visibility and context, XDR speeds up incident response. The time needed to identify, look into, and respond to security events is decreased by XDR’s automated data collecting, analysis, and investigative processes.
It assists security teams in setting alert priorities, comprehending the extent and impact of an incident, and acting quickly to control and eliminate threats.
- Simplified Security Operations
By combining many security technologies into a single platform, XDR streamlines security operations. Security teams can use a unified interface for monitoring, analysis, and reaction instead of managing and maintaining distinct tools.
This consolidation lessens complexity, boosts operational effectiveness, and lowers the possibility of security breaches brought on by problematic tool integration.
- Proactive Threat Hunting
By enabling security teams to actively look for threats rather than relying just on reactive detection, XDR enables proactive threat hunting. Security analysts can proactively analyze patterns, behaviors, and indicators of compromise that may have gone unreported with access to comprehensive data and advanced analytical tools. Organizations are able to stay ahead of cyber threats with the support of this proactive approach.
- Scalability and Adaptability
In order to scale and respond to changing security concerns, XDR was created. XDR platforms can incorporate extra security elements and technologies to handle new risks as they arise, such as new threat vectors.
With this flexibility, businesses may continuously improve their security capabilities without suffering significant disruptions or exorbitant infrastructure modifications.
- Compliance and Reporting
In order to demonstrate compliance with security rules, laws, and industry standards, XDR solutions frequently offer reporting and compliance tools. XDR solutions can provide thorough reports and audit logs by combining and analyzing security data, streamlining compliance efforts, and assisting with incident investigations.
Who Uses XDR?
Businesses and companies of all sizes and in a variety of industries are the main users of XDR. Any firm that wants to improve its security capabilities and successfully counter contemporary cyber threats should consider it. Among the firms that frequently use XDR are the following ones:
- Enterprises
For the purpose of streamlining incident response procedures and consolidating their security operations, large enterprises and organizations with intricate IT infrastructures frequently implement XDR. A centralized platform that can handle the many security requirements of enterprise-level environments is offered by XDR.
- Government Agencies
Federal, state, and local governments, as well as other levels of government, use XDR to safeguard their vital infrastructure and sensitive data. Targeting government systems, networks, and services, sophisticated cyber threats can be detected and countered with the aid of XDR.
- Financial Institutions
Due to the sensitive data and money they manage, banks, insurance companies, investment businesses, and other financial organizations confront serious security concerns. The use of XDR helps to improve security protocols, spot fraud, and safeguard client data.
- Healthcare Organizations
Hospitals, medical facilities, and healthcare professionals manage enormous volumes of sensitive patient data, which makes them desirable targets for cybercriminals. To protect patient privacy, secure electronic health information, and stop data breaches, healthcare organizations can use XDR.
- E-commerce and Retail
Online merchants and e-commerce platforms depend on XDR to safeguard client payment data, stop fraud, and uphold the reliability of their websites. Attacks aiming at compromising e-commerce websites and collecting client data are easier to spot and address with XDR.
- Critical Infrastructure Operators
Operators of critical infrastructure, such as those in the energy, transportation, and telecommunications sectors, use XDR to protect themselves from cyber threats that can impair vital services. Critical systems can be monitored and protected, network traffic anomalies can be found, and prospective assaults may be quickly countered with the aid of XDR.
- Managed Security Service Providers (MSSPs)
Using XDR by MSSPs allows them to provide clients with cutting-edge security services. Adopting XDR and utilizing its unified platform and sophisticated threat detection capabilities allows MSSPs to manage security operations for a number of organizations efficiently.
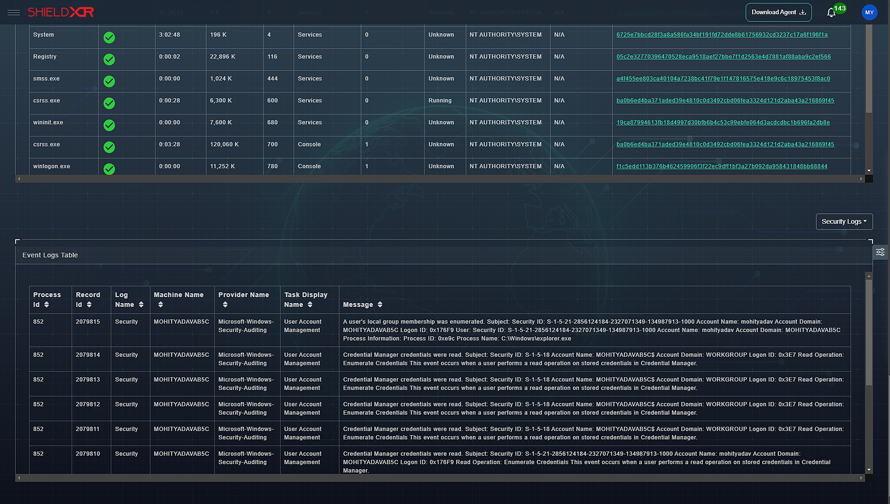
How Does XDR Work?
- Data Collection
In addition to endpoints (workstations, servers, and mobile devices), network hardware (firewalls, switches, etc.), cloud environments, and other security technologies, XDR also gathers security data from these sources.
This information includes logs, events, network activity, endpoint actions, and other things.
- Data Aggregation and Correlation
A central platform, or SIEM system, aggregates and correlates the acquired data. XDR builds a thorough picture of the organization’s security landscape by merging data from many sources, spotting potential risks and suspicious behaviours.
- Advanced Analytics
To analyze the combined data, XDR uses cutting-edge analytics methods, including machine learning and behavioral analysis. It searches for anomalies, signs of compromise, and well-known patterns linked to online threats. On the basis of past data, machine learning models are trained to recognize novel and changing dangers.
- Threat Detection and Prioritization
The analysis is used by XDR to produce alerts and rank potential hazards. It helps security staff feel less alert since it can tell the difference between real security occurrences and false positives.
Each warning is given a risk score or severity level by XDR to aid in organising and prioritising inquiries and action plans.
- Incident Investigation and Response
XDR gives security professionals the resources and tools to look into security occurrences. To assist in the investigation, it provides contextual information about the affected systems, the attack chain, and pertinent log data.
Security analysts have the ability to delve deeper into certain alerts, examine linked incidents, and comprehend the size and impact of an occurrence.
- Automated Response and Remediation
Either human or automated reaction actions are supported by XDR. It may launch predefined reaction procedures, such as the isolation of compromised endpoints, the blocking of erroneous network traffic, or the quarantining of malicious files.
Response times are sped up by automation, which also lessens the effect of security events.
- Threat Hunting and Proactive Defense
Security teams may actively look for threats by examining previous and current data, thanks to XDR. It enables analysts to carry out thorough investigations, spots unseen dangers, and find signs of compromise that may have escaped notice at first.
This proactive strategy enhances overall security posture by exposing sneaky assaults.
- Reporting and Compliance
Reporting and compliance tools are frequently included in XDR platforms. To satisfy the needs of regulatory compliance, they produce thorough reports, audit logs, and metrics.
These reports shed light on security-related incidents, actions taken in reaction to them, and overall security efficiency.
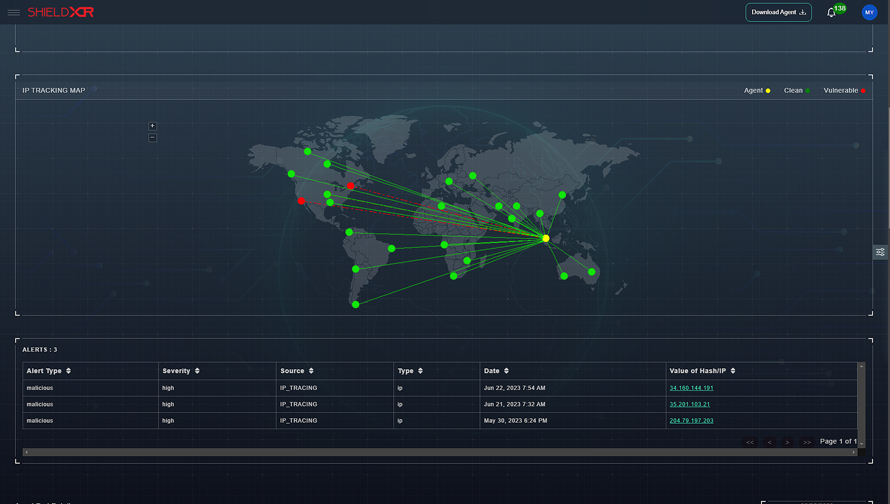
XDR Security Solutions
Some of the XDR Security Platforms are available in the industry to offer security solutions against online threats that can secure the data from being breached. After this, the adversaries won’t be able to trespass into the system.
Some of the Best XDR Platforms are offered by popular best XDR Solutions 2023, such as follows.
- Trend Micro XDR
Trend Micro XDR blends endpoint detection and response (EDR), email security, network security, and cloud workload protection to provide complete threat detection and response capabilities.
To assist organizations in defending against sophisticated threats, it provides centralized visibility, automated detection, and response workflows.
- Palo Alto Networks Cortex XDR
Network, endpoint, and cloud data are all combined by Palo Alto Networks to create Cortex XDR, which offers unified threat detection and response. To find advanced threats, it uses behavioral analytics, machine learning, and AI-driven detection.
An automated incident response, investigation tools, and threat-hunting capabilities are all provided by Cortex XDR.
- Shield XDR
If you contact Craw Security, you will get the Best XDR in Cyber Security in India. Craw Security is one of the Best XDR Service Providers that offer Shield XDR the best detection and response services for better protection against online threats. It’s one of the reputed Cyber Security Services providers.
- McAfee MVISION XDR
McAfee’s MVISION XDR unifies endpoint security, network security, and cloud security to identify threats across various attack vectors and take appropriate action. To give real-time visibility and automate threat-hunting and response tasks, it uses advanced analytics, machine learning, and AI algorithms.
- Fortinet FortiXDR
User and entity behavior analytics (UEBA), network security, and endpoint security are all included in FortiXDR, Fortinet’s XDR solution. To assist organizations in recognizing and countering sophisticated attacks, it provides automated incident response, threat intelligence, and integrated threat-hunting capabilities.
- Cisco SecureX
Security technologies such as endpoint security, network security, and cloud security are all integrated into a single platform by Cisco’s XDR solution, SecureX.
It offers a centralized view of security events, workflows for automatically detecting and responding to threats, and threat-hunting skills.
- SentinelOne XDR
Advanced threat detection and response are provided by SentinelOne’s XDR system, which integrates endpoint security, network visibility, and cloud workload protection.
It uses behavioral AI models, machine learning, and automation to find hazards throughout the entire IT system and remove them.
Benefits of XDR
| S.No. | Facilities | Details |
| 1. | Comprehensive Threat Detection | Through the integration of data from several sources, including endpoints, networks, and cloud environments, it offers a comprehensive perspective of the security landscape within an organization.
Better threat detection, including the recognition of sophisticated, multi-stage attacks that may use many access points, is made possible by this thorough visibility. |
| 2. | Faster Incident Response | Automating data gathering, analysis, and investigation, simplifies incident response procedures. It shortens the time needed to identify, look into, and address security incidents.
With real-time alerting, correlation tools, and automated reaction actions, XDR enables businesses to quickly and efficiently mitigate threats and lessen the effects of security breaches. |
| 3. | Improved Security Operations Efficiency | It unifies security tools and technologies onto a single platform, which reduces complexity and boosts operational effectiveness.
By managing and keeping track of security events, warnings, and investigations using a single interface, security teams can avoid spending time and energy switching between many consoles or interfaces. The risk of oversight or incorrect setups is decreased by this centralized approach to security operations. |
| 4. | Proactive Threat Hunting | By giving them access to extensive security data, powerful analytics, and behavioral analysis, it enables security teams to look for dangers actively.
Analysts can carry out exhaustive research, examine past and current data, and spot potential dangers or signs of compromise that conventional security solutions would have overlooked. Organizations can stay ahead of new risks with the help of this proactive approach. |
| 5. | Scalability and Adaptability | It solutions are made to grow with changing security challenges. As their needs change, businesses can include more security tools and technologies without materially altering their infrastructure.
This adaptability makes sure the security system is efficient and keeps up with shifting threat environments. |
| 6. | Centralized Visibility and Reporting | Centralized visibility into security events, incidents, and trends across the whole IT environment is provided via XDR solutions.
This visibility helps organizations provide thorough reports for compliance audits and regulatory needs, offers insights for risk management, and promotes improved security decision-making. |
| 7. | Enhanced Collaboration and Communication | By offering a centralized platform for exchanging and analyzing security data, XDR fosters cooperation and communication across security teams.
It enhances knowledge sharing, enabling cross-functional teams to collaborate more successfully, and aids in coordinating security activities with overarching organizational objectives. |
Frequently Asked Question
About the benefits of implementing the XDR Security Solution
1. What is XDR?
Extended Detection and Response is referred to as XDR. The goal of this all-encompassing security strategy is to improve threat detection, response, and remediation capabilities throughout an organization’s IT environment by fusing a variety of security technologies and tools into a single platform.
2. Why Is XDR Important?
XDR is important for several reasons:
- Enhanced Threat Detection,
- Faster Incident Response,
- Simplified Security Operations,
- Proactive Threat Hunting,
- Scalability & Adaptability, and
- Compliance & Reporting
3. Who Uses XDR?
The following entities are among those who commonly use XDR:
- Enterprises,
- Government Agencies,
- Financial Institutions,
- Healthcare Organizations,
- E-commerce & Retail,
- Critical Infrastructure Operators, and
- Managed Security Service Providers (MSSPs)
4. How Does XDR Work?
Here is a high-level overview of how XDR typically operates:
- Data Collection,
- Data Aggregation & Correlation,
- Advanced Analytics,
- Threat Detection & Prioritization,
- Incident Investigation & Response,
- Automated Response & Remediation,
- Threat Hunting & Proactive Defense, and
- Reporting & Compliance.
5. When Is the Best Time to Use XDR?
Here are some scenarios where implementing XDR can be particularly beneficial:
- Increasing Cybersecurity Risks,
- Complex IT Environments,
- Limited Security Resources,
- Regulatory Compliance Requirements,
- Proactive Threat Hunting, and
- Integration & Scalability Needs
6. Where Does XDR Come From?
As a result of the changing threat landscape and the demand for better detection and response capabilities, the security concept known as XDR has emerged. Although XDR doesn’t have a single clear source or genesis, it can be seen as an advancement and extension of current security technology and procedures.
















