Shield XDR: Best Solutions & Vendors in New Delhi, India
June 21, 2023 2023-07-24 18:25Shield XDR: Best Solutions & Vendors in New Delhi, India

A Comprehensive Threat Protection Solution

What is Shield XDR ?
With Artificial Intelligence, Machine Learning and Analytics
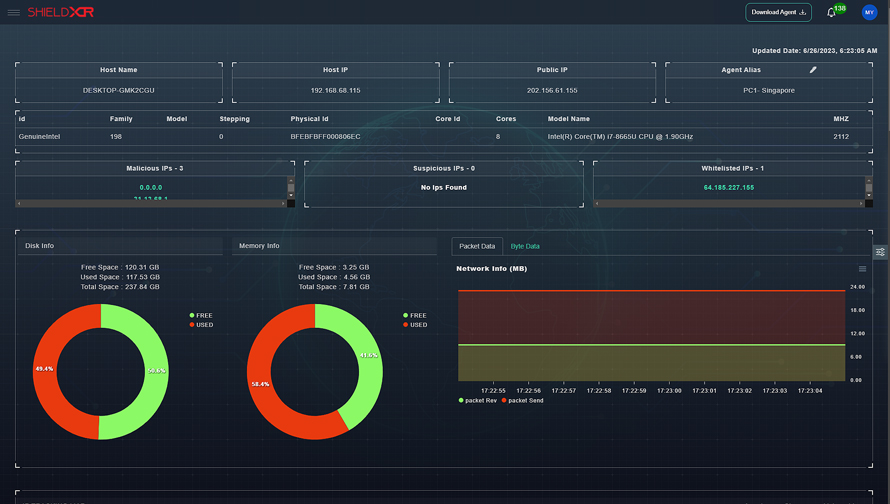
With the use of cutting-edge innovations like artificial intelligence (AI), machine learning (ML), and behavioral analytics, Shield XDR is an effective security solution that can quickly identify and address sophisticated threats. Through the integration of endpoint security, network security, and cloud security into a single platform, it provides a holistic approach to threat detection and response. Shield XDR offers round-the-clock surveillance and alerts, enabling businesses to react promptly to any security event.

Key Features of Shield XDR ?
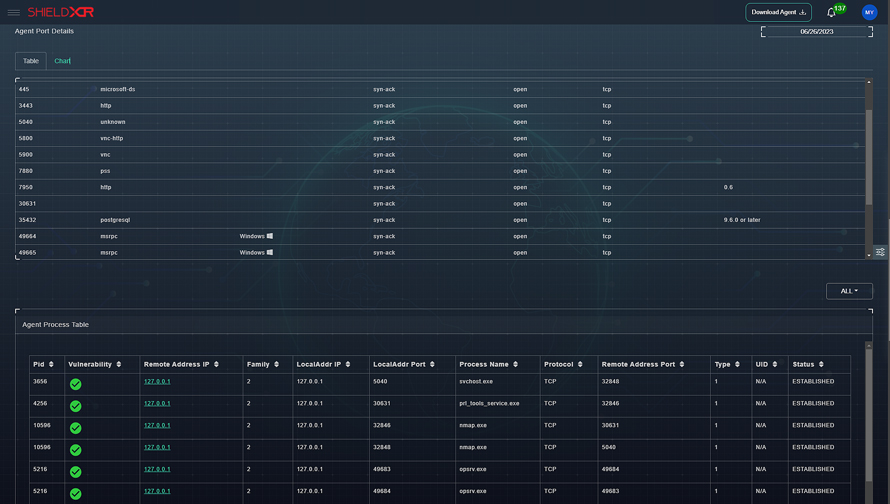
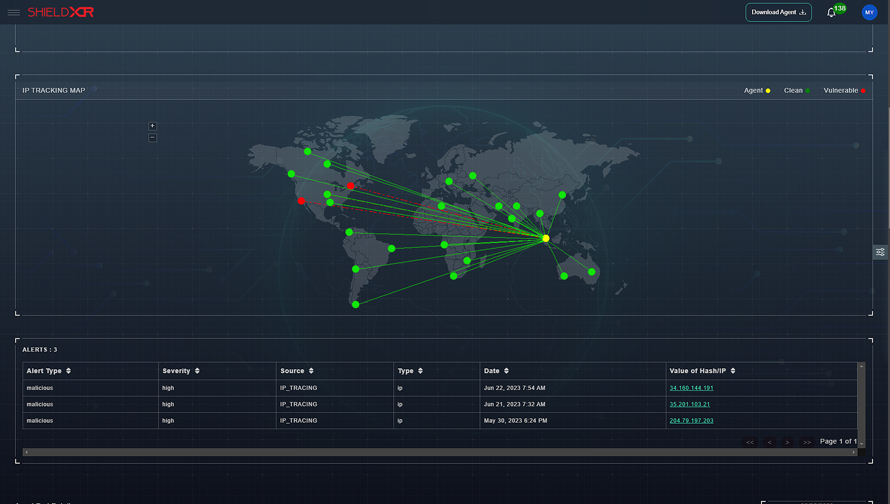
Shield XDR offers complete network security by keeping track of all network activity and spotting potential dangers. To identify unusual network activity and stop unwanted traffic prior to it reaching its target, it employs behavioral analytics.
Threat Hunting
We offers rapid response capabilities that let businesses act rapidly in the event of a security problem. To lessen the effects of a security issue, it might automatically isolate compromised endpoints, restrict malicious traffic, implement additional steps
Call Us For Quote
Shield XDR Features
Why Choose Shield XDR ?

Secure Yourself With Rapid Cyber Security Solutions!
Cloud-based platform, Installed in Seconds for Ultimate Protection!
450 Reviews
Get Started
Training Available 24*7 Call at +91 9513805401