Understands The Access Control List in Networking
Understands The Access Control List in Networking
What is an access control list (ACL)?
An access control list, often known as an ACL, is a list of rules that specify which people or systems are allowed access to a certain object or system resource and which are not allowed access to that item or resource. Additionally, access control lists can be put in routers or switches, where they perform the function of filters and manage the traffic that is permitted to enter the network environment.
There is a security attribute associated with every system resource that details the access control list for that resource. Each and every user who is able to access the system is represented by an entry on the list. The ability to read a file or all of the files in a directory, the ability to write to the file or files, and the ability to execute the file if it is an executable file or program are the attributes that are most frequently associated with access control lists (ACLs) for file systems. The access control lists (ACLs) are also incorporated into the network interfaces and operating systems (OSes), such as Windows and Linux. Access control lists are utilized on a computer network in order to either prevent or give permission for particular kinds of traffic to enter the network. It is normal practice for them to filter traffic according to its origin and destination.
What are access control lists used for?
Controlling the permissions that are granted to a computer system or computer network is accomplished through the use of access control lists. Traffic coming into and going out of a certain device can be filtered with their help. Those devices may be network devices that perform the function of network gateways or endpoint devices that users reach directly over the network.
Individual users on a computer system are granted varying degrees of privileges, which are determined by the roles that they play. As an illustration, a person who is logged in as the administrator of the network might have the ability to read, write, and edit a sensitive file or other resource at their disposal. An individual who is logged in as a guest, on the other hand, might just have read permissions.
In order to improve the efficiency of a network and to provide administrators with granular control over users on their computer systems and networks, access control lists can be of assistance in organizing traffic. In addition, access control lists (ACLs) can be utilized to enhance network security by suppressing harmful traffic.
How do ACLs work?
The name of a user or group of users is included in one or more access control entries (ACEs) that are contained inside each access control list (ACL). Another possibility is that the user is a role name, such as a tester or a programmer. An access mask is a string of bits that specify the access privileges for each of these users, groups, or roles. These access privileges are indicated in the access mask. A system administrator or the owner of an object is often the one who is responsible for creating the access control list for that object.
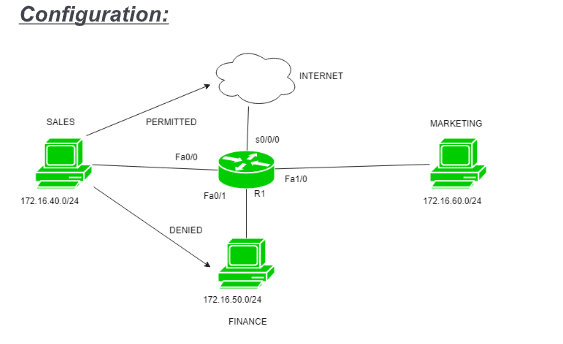
Types of access control lists
There are two basic types of ACLs:
- File system ACLs: ACLs are used to manage access to directories and files within a file system. After the system has been accessed, they provide operating systems with the instructions that define user access rights for the system as well as the privileges that are granted to users.
- Networking ACLs: Administrative control lists (ACLs) in networking are used to govern network access by supplying instructions to network switches and routers. These instructions identify the types of traffic that are permitted to interface with the network. Once a user is within the network, these access control lists (ACLs) also specify user permissions. The rules for the networking access control list are predefined by the network administrator. Thus, they perform a function that is comparable to that of a firewall.
ACLs can also be categorized by the way they identify traffic:
- Standard ACLs: Using source IP addresses, standard access control lists (ACLs) either prohibit or allow a full protocol suite.
- Extended ACLs: Instead of merely blocking or allowing network traffic based on the source address alone, extended access control lists (ACLs) prohibit or allow traffic based on a more distinct collection of attributes that includes source and destination IP addresses as well as port numbers.
Benefits of using an ACL
There are several benefits of using an ACL, including the following:
- Simplified user identification. A user’s identification can be made more straightforward with the use of an access control list. Access control lists (ACLs) ensure that only authorized users and traffic are able to access a system.
- Performance. When compared to alternative technologies that accomplish the same job, access control lists (ACLs) offer performance advantages. Due to the fact that they are configured directly on the forwarding hardware of the routing device, access control lists do not have a detrimental impact on the performance of routing devices. When compared to a stateful inspection firewall, which is a separate piece of software that has the potential to cause performance deterioration, take this into consideration. Controlling the traffic on a network also makes it possible for networks to operate more effectively.
- Control. Using access control lists (ACLs), administrators can have more granular control over the permissions granted to users and traffic on a network at a variety of different points throughout the network. The access to network endpoints and the traffic that flows between internal networks can be controlled with their assistance.
Where can you place an access control list?
It is possible to install access control lists on practically any security or routing device, and it might be advantageous to have numerous ACLs installed in various different portions of the network environment.
In the case of network endpoints, such as apps or servers, that demand high speed and performance in addition to security, access control lists (ACLs) are an excellent choice.
Depending on the architecture of the network, administrators may decide to position an access control list at a variety of connections throughout the network. Because edge routers are located on the edge of a network, access control lists (ACLs) are frequently installed on these routers. Because of this, the Access Control List (ACL) is able to filter traffic before it is transmitted to the rest of the network.
To create a demilitarized zone (DMZ) between the public internet and the rest of the network, edge routers that are equipped with access control lists (ACLs) can be installed. A demilitarized zone (DMZ) is a buffer zone that is equipped with an outward-facing router and offers widespread protection against all external networks. Additionally, it has an internal router that creates a barrier between the secured network and the demilitarized zone.
Application servers, web servers, domain name servers, and virtual private networks are some examples of the types of network resources that may be contained within DMZs respectively. When it comes to the routing device, the configuration of the access control list (ACL) can vary depending on the devices that are located behind it as well as the categories of users who require access to those devices.
Components of an access control list
Entries in the Access Control List (ACL) are made up of a number of distinct components that indicate how the ACL handles various kinds of traffic. The following are some examples of components that are commonly seen in ACL assemblies:
- Sequence number. The identity of the object that is within the ACL entry can be determined by the sequence number.
- ACL name. To identify an Access Control List (ACL), this uses a name rather than a number. There are certain ACLs that permit both letters and numbers.
- Comments. Users are able to add comments to certain access control lists (ACLs), which are further descriptions of the ACL entry.
- Network protocol. Administrators are able to permit or disallow traffic based on a network protocol, such as Internet Protocol (IP), Internet Control Message Protocol (ICP), Transmission Control Protocol (TCP), User Datagram Protocol (UDP), or NetBIOS, for example.
- Source and destination. In accordance with Classless Inter-Domain Routing, this specifies a particular IP address that can be blocked or allowed, as well as a range of IP addresses.
- Log. A few of the ACL devices maintain a log of the items that are recognized by the ACL.
More complex Access Control List (ACL) entries provide the capability to identify traffic based on certain IP packet header data, such as Differentiated Services Code Point, Type of Service, or IP precedence.
How to implement an ACL?
For the purpose of implementing an access control list (ACL), network managers need to have a comprehensive understanding of the many forms of traffic that enter and exit the network, as well as the resources that they are attempting to safeguard. Administrators should organize and manage information technology assets in a hierarchical structure, dividing them into distinct categories, and assigning varying privileges to users.
It is common practice to deploy a standard access control list (ACL) in close proximity to the destination that it is attempting to protect. The implementation of extended access control lists typically takes place in close proximity to the source. By using access list names rather than access list numbers, it is possible to configure extended access control lists (ACLs).
Following is an example of the fundamental syntax that is utilized in the process of creating a standard numbered access control list on a Cisco router:
| Router (config)# access-list (1300-1999) (permit | deny) source-addr (source-wildcard) |
The various parts mean the following:
- (1300-1999) specifies the ACL IP number range. This names the ACL and defines the type of ACL. 1300-1999 makes this a standard ACL.
- (permit | deny) specifies the packet to permit or reject.
- Source-addr specifies the source IP address.
- Source-wildcard specifies the wildcard mask.
A router is able to detect which bits of an IP address are accessible to a network device so that it can analyze those bits and determine whether or not they match the access list by using a wildcard mask.
The configuration code that was presented earlier can be entered by users into the command line in order to generate the access control list. In addition, cloud platforms from vendors such as Oracle and IBM often provide users with the opportunity to build an access control list within their user login page.
Enroll in A Detailed Basic Networking Course
Rather than wondering here and there, all the interested candidates with a wish to start a superb career in basic networking can start their study in the trajectory of networking by enrolling in the Best Basic Networking Course in Delhi NCR by Craw Security, the Best Networking Training Institute in India. To gather more info on the same and other relevant stuff, kindly call the hotline mobile number +91-9513805401 or visit the Official Website of Craw Security.















