Top 10 Network Attacks | Craw Security

Top 10 Network Attacks | Craw Security
Top 10 Network Attacks
Introduction:
Network attacks or assaults continue to pose a persistent and ongoing threat to both businesses and individuals. These attacks are designed to exploit weaknesses in communication protocols, setups, or devices.
In this article, we provide an overview of the 10 most significant network attacks that have garnered attention from cybersecurity experts worldwide with their massive impact on various stakes.
1. Denial of Service (DoS) & Distributed Denial of Service (DDoS)
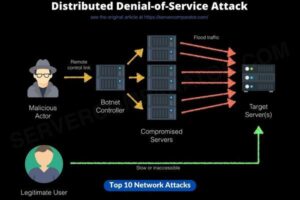
Denial-of-Service (DoS) attacks include inundating a network or system with an excessive amount of traffic, hence causing it to become inaccessible. DDoS attacks leverage the utilization of numerous infected machines to amplify their impact.
2. Man-in-the-Middle (MitM) Attacks
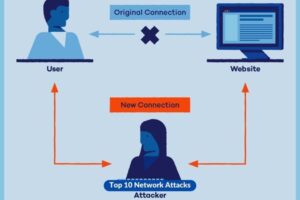
As implied by its nomenclature, attackers engage in the interception of communication between two entities, hence possibly engaging in activities like eavesdropping or modifying the said communication without the awareness or consent of the original participants.
3. ARP Spoofing
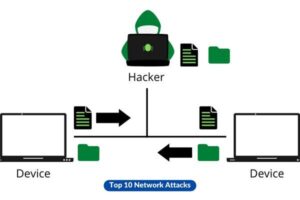
In the context of local area networks, it has been observed that malicious actors employ deceptive Address Resolution Protocol (ARP) signals with the intention of associating their own Media Access Control (MAC) address with the IP address of a bona fide network participant. This deceptive tactic effectively diverts network traffic towards the attacker.
4. Ping of Death
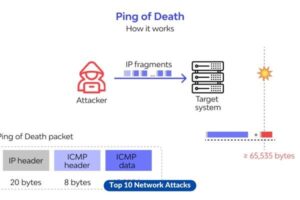
Attackers have the ability to disrupt systems that are incapable of processing packets greater than the maximum allowable size by deliberately delivering enormous packets.
5. Port Scanning
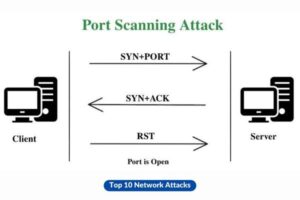
The process entails conducting a scan on a networked device to identify accessible ports, thereby enabling potential exploitation. This phenomenon frequently serves as a forerunner to other forms of attacks.
6. Smurf Attack
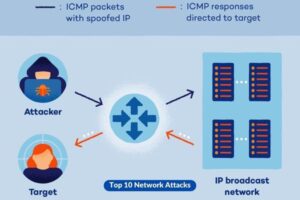
The perpetrator engages in the dissemination of a significant quantity of ICMP (Internet Control Message Protocol) echo request packets, employing a falsified source IP address, hence leading to an escalation of network traffic directed towards the target.
7. SYN Flood
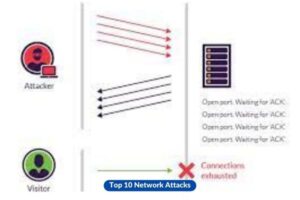
The act of inundating a target system with a substantial volume of TCP SYN (synchronize) packets, utilizing fabricated source IP addresses, can result in the depletion of resources and render the system unresponsive.
8. DNS Spoofing (or Cache Poisoning)
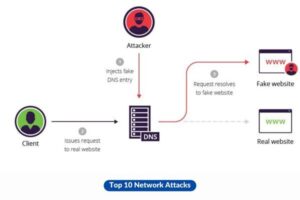
The act of introducing corrupt DNS data into the cache of a DNS resolver is perpetrated by attackers, leading to the redirection of users towards IP addresses that are erroneous and potentially exposing them to websites that may contain dangerous content.
9. Rogue DHCP Server Attack
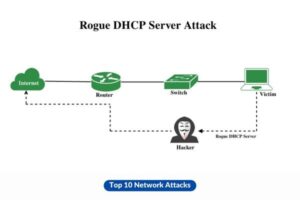
In the context of network security, an individual with malicious intent deploys a rogue Dynamic Host Configuration Protocol (DHCP) server within a network infrastructure, thereby distributing inaccurate IP addresses and redirecting network traffic.
10. MAC Flooding
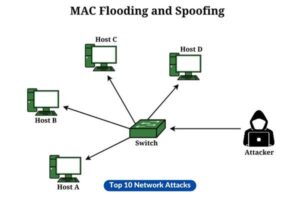
The assailant inundates a switch with a multitude of frames originating from diverse source MAC addresses, potentially inducing the switch to operate in a manner akin to a hub, disseminating network traffic to all connected devices. This compromise of network security is a consequence of the aforementioned actions.
Wrapping Up
In the bottom line, we would like to say that the mitigation of these network assaults necessitates the implementation of a comprehensive strategy involving multiple measures. Firewalls, intrusion detection systems, regular system and software updates, strong authentication techniques, and constant network monitoring are essential components of a comprehensive network defense plan. In response to the changing nature of dangers, it is imperative for both individuals and organizations to adapt their protective measures accordingly.
















