Walkthrough of Krypton CTF (Capture The Flag) | Craw security

Walkthrough of Krypton CTF (Capture The Flag) | Craw security
Walkthrough of Krypton
SOURCE:- KRYPTON LEVEL1
We get base64 encrypted password for KRYPTON2
S1JZUFRPTklTR1JFQVQ=
Lets decrypt it. Either we can decrypt it with cyberchef or we can decrypt it with terminal
Let se
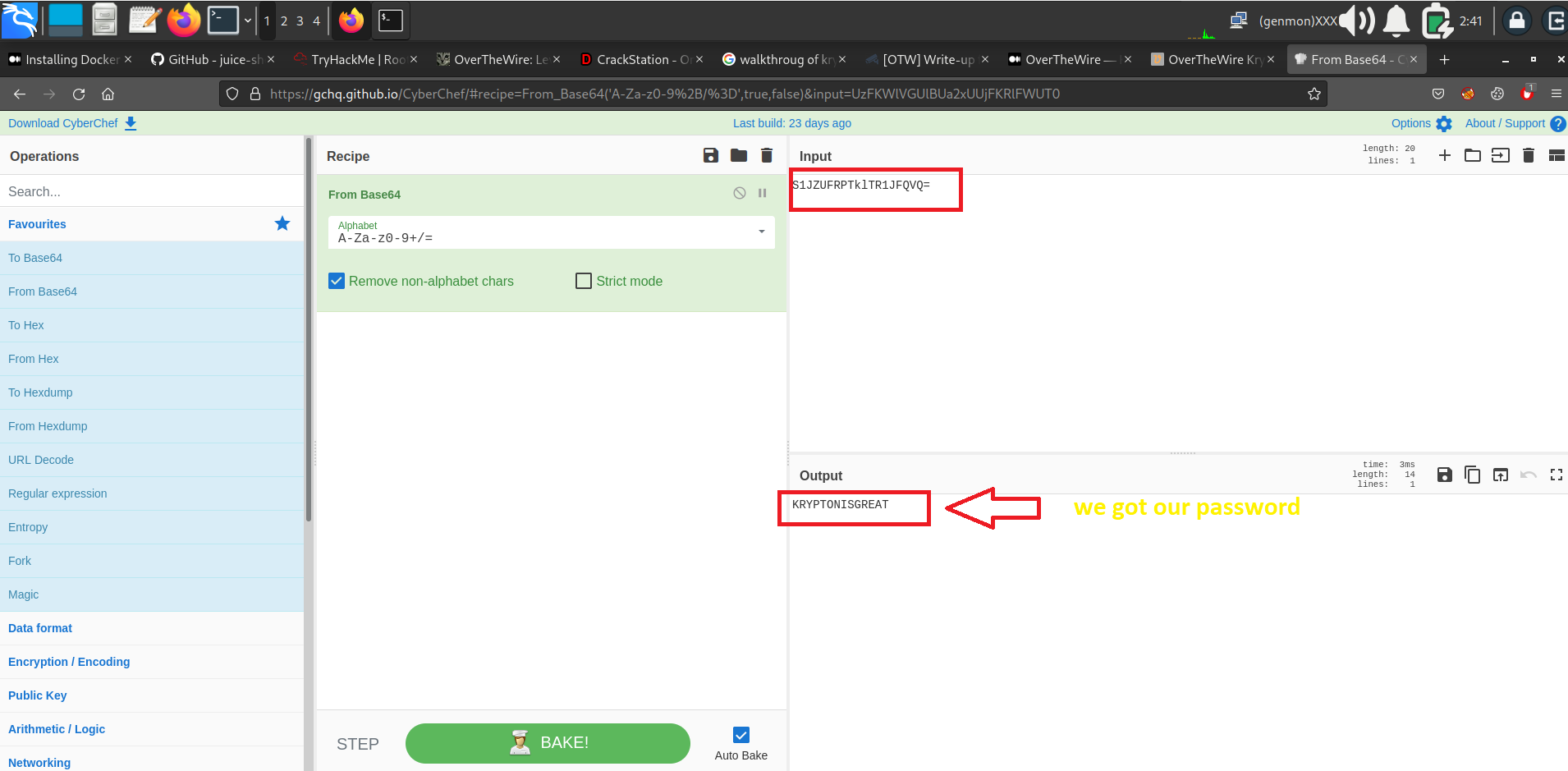
Above decryption is done by Cyberchef-
Source:- https://gchg.github.io/cyberchef/
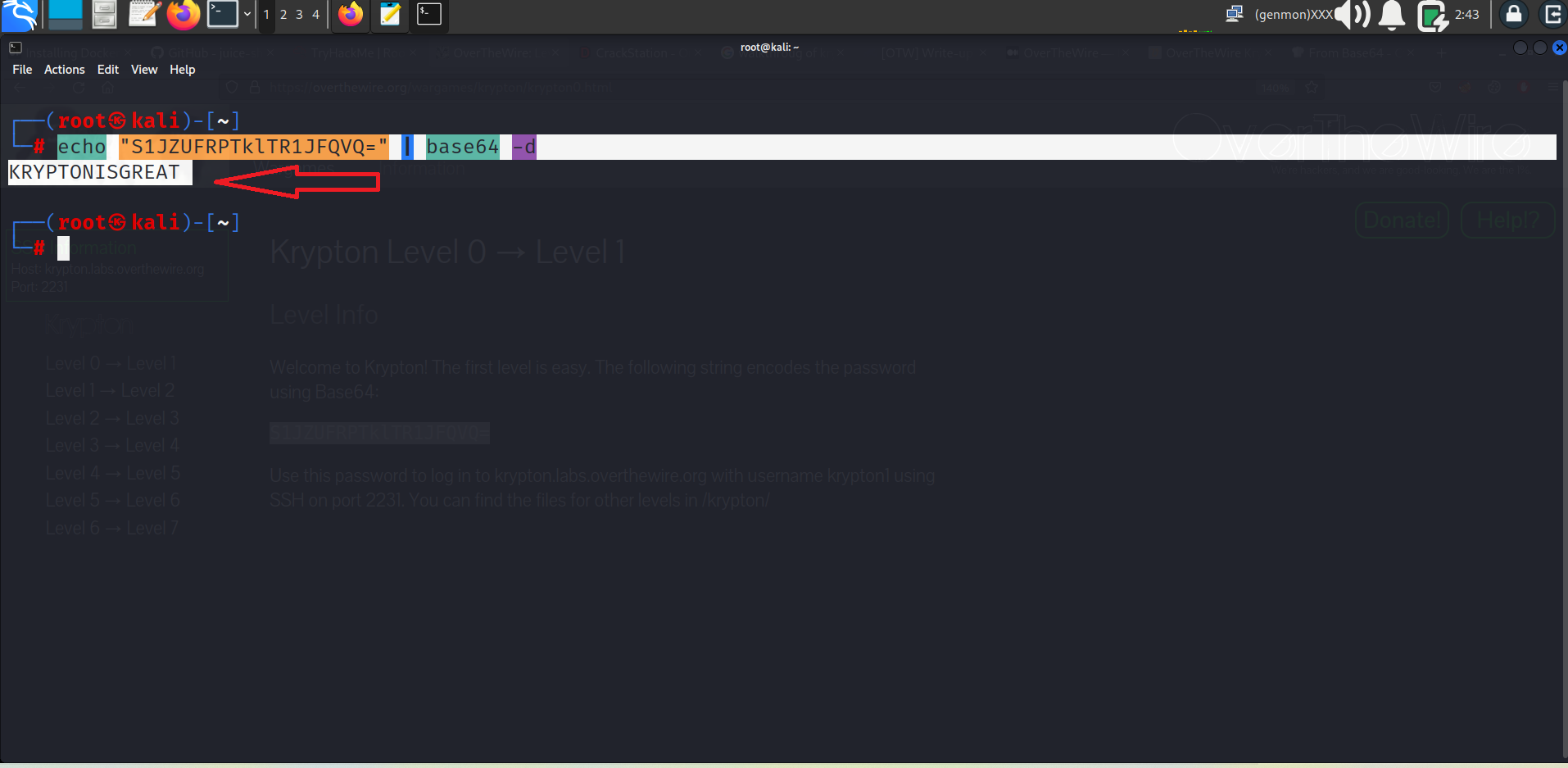
Here is done by Terminal
Command:- echo “(ecrpted_text)” | base64 -d
We got our password- KRYPTONISGREAT
Now lets logged in with ssh and our port is 2231
Command:- ssh krypton1@krypton.labs.overthewire.org -p 2231
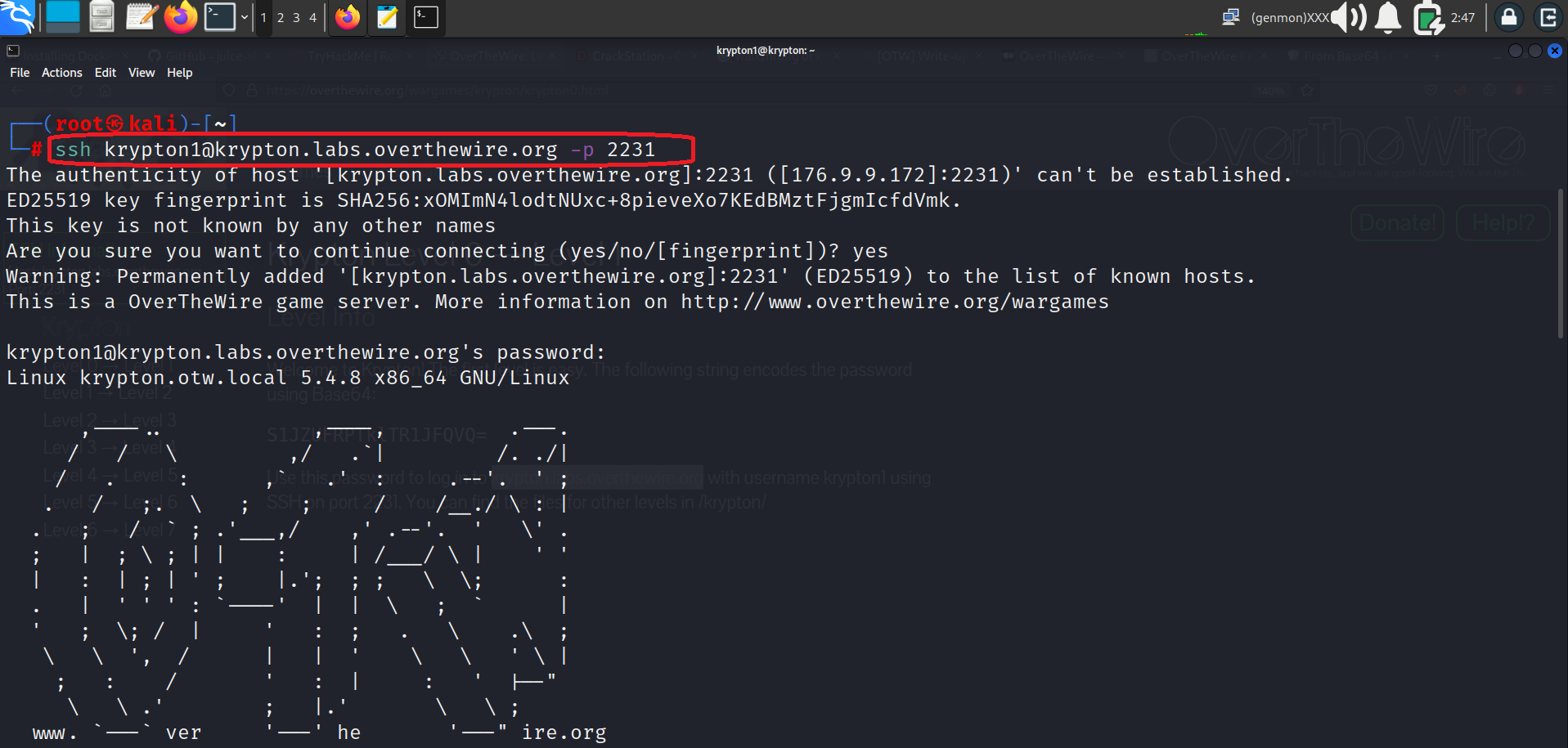
We got the shell
Info for level2
The password for level 2 is in the file ‘krypton2’. It is ‘encrypted’ using a simple rotation. it is also in non- standard ciphertext format. when using alpha characters for cipher text it is normal to group the letters into 5 letter clusters, regardless of word boundaries. this helps obfuscate any patterns. this file has kept the plain text boundaries and carried them to the cipher text. enjoy!
In instruction for level2 it is clear that have krypton 2 file in which there is encrypted password for krypton2 but if we navigate we don’t find any text file of krypton2, so for finding we will run find command
Command:- find/-name krypton2 2>/dev/null filter ther permission denied result
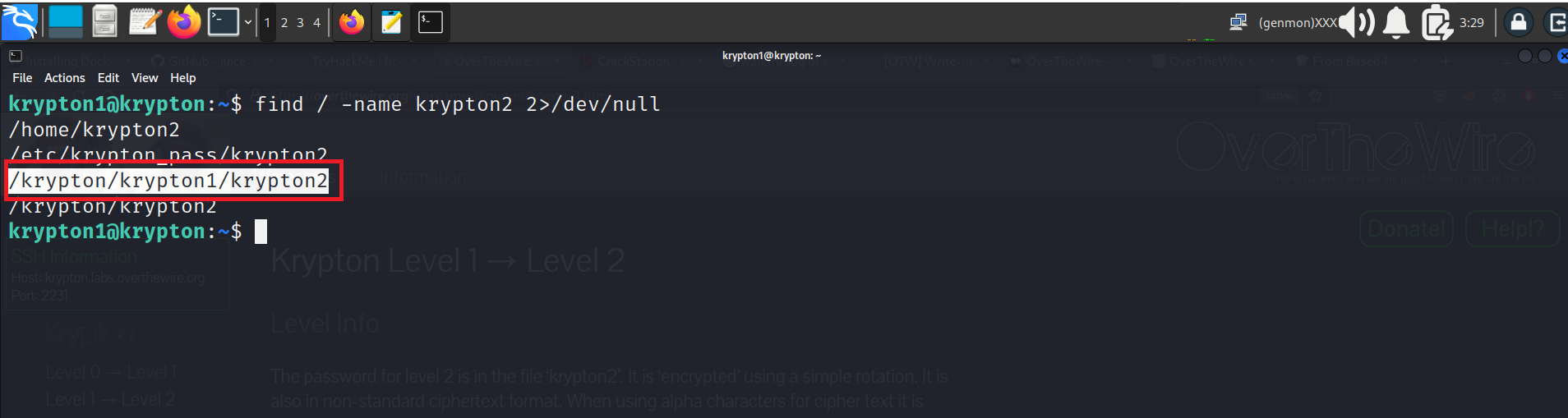
We can see the Krypton2 file
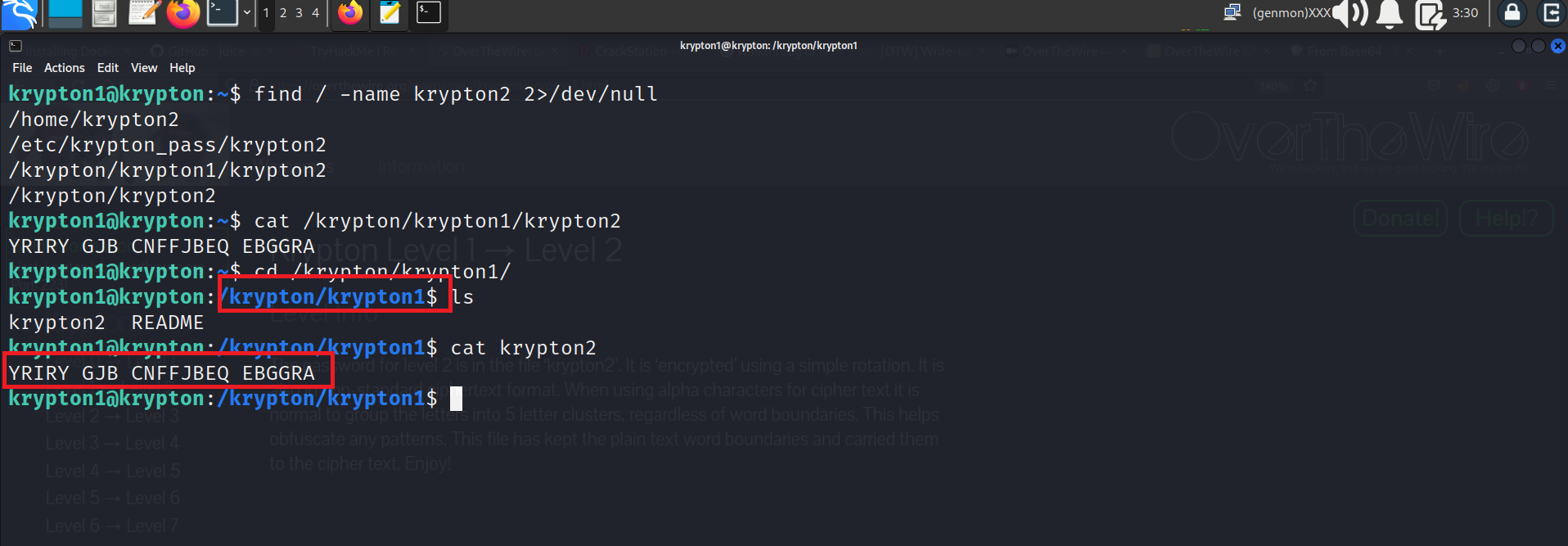
Here is the ecrypted password “YRIRY GJB CNFFJBEQ EBGGRA”
Same decrypt it with with cyberchef or terminal
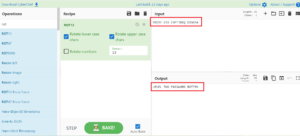
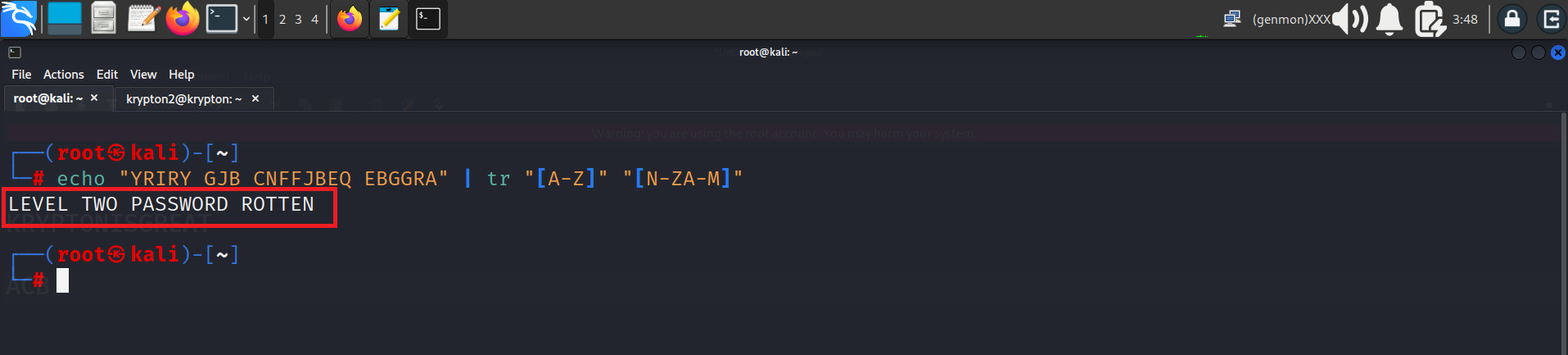
Both method are there in above pic
Logged in krypton2
Then we got the encryption and key
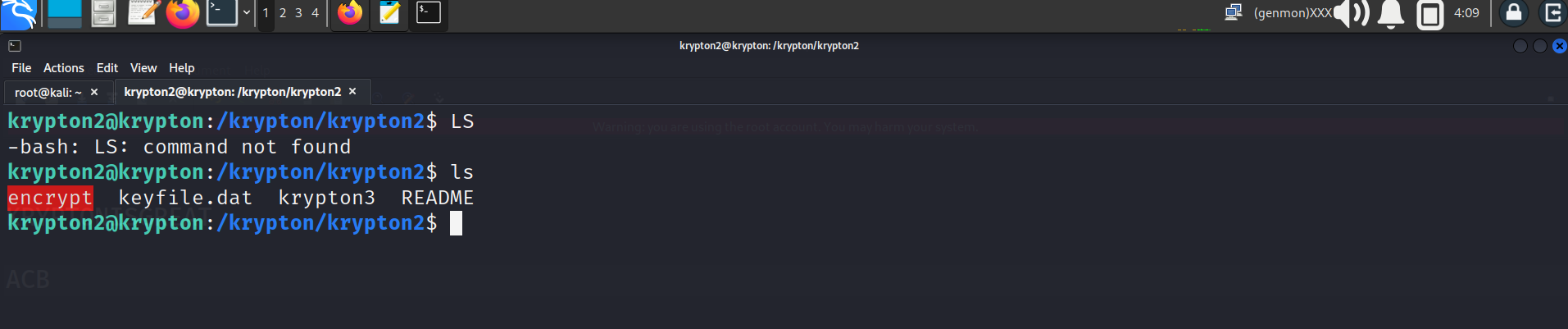
First, we need to check which type of encryption is used so we need to create a temp file as instruction is given In level3 web page.
krypton2@melinda:~$ mktemp -d
/tmp/tmp.Wf2OnCpCDQ
krypton2@melinda:~$ cd /tmp/tmp.Wf2OnCpCDQ
krypton2@melinda:/tmp/tmp.Wf2OnCpCDQ$ ln -s /krypton/krypton2/keyfile.dat
krypton2@melinda:/tmp/tmp.Wf2OnCpCDQ$ ls
keyfile.dat
krypton2@krypton: nano plain
create a text file and encrypt it so that we can know that which encryp
krypton2@melinda:/tmp/tmp.Wf2OnCpCDQ$ chmod 777 .
krypton2@melinda:/tmp/tmp.Wf2OnCpCDQ$ /krypton/krypton2/encrypt /etc/issue
krypton2@melinda:/tmp/tmp.Wf2OnCpCDQ$ ls
ciphertext keyfile.dat
know we will analyze the ciphertext file so that we can know which rot is used here
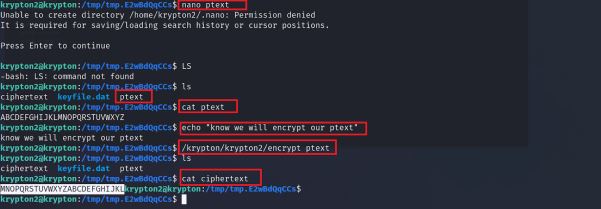
As we above image we created ptext as a plain text and than I encrypt it with the help of given encryption.
we found that A is converted into M so for this process, we are clear that encryption is used ROT12 we can decypt it from real key. let’s decrypt it.
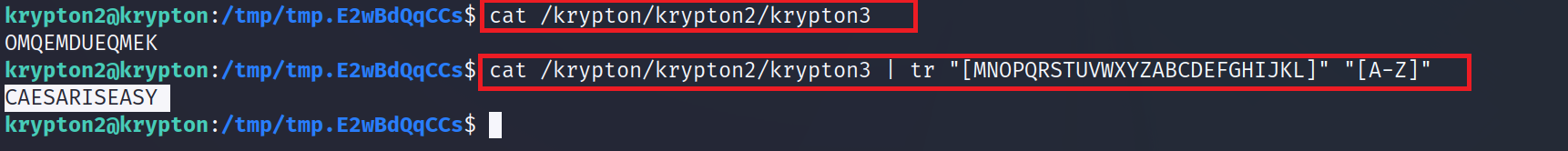
we got krypton3 password
lets logged in:- ssh krypton3@krypton.labs.overthewire.org -p 2231
Password:- CAESARISEAS














