Why Need For Cyber Security Now A DAY

Why Need For Cyber Security Now A DAY
Why Need For Cyber Security Now A DAY
Cyber Security is needed to protect ourselves from harmful attacks done by adversaries, which is too common nowadays. The reason behind cybersecurity has always been protecting our data from the person who is unauthorized or who shouldn’t have access to that data in any sense.
To protect those datasets from unauthorized access, there are several techniques and tools are introduced to the professionals. This must not get into the hands of the ordinary public. That’s simply because those who haven’t been elected for the purpose of legally doing such activities shouldn’t have such techniques and tools for practicing publicly on innocent people.
Some of the skilled ones in the industry have a lot in common with the professionals working for the organizations that hire professionals to work for them and protect them against harmful threats. The question – “Why Do We Need Cyber Security Nowadays?” It is still intact. For that, you can read further.
What is Cybersecurity?
Social Media has become more open for the general public to explore knowledge and share their opinions over the platforms next to it. Unknowingly they upload their personal information over the platforms.
Adversaries nowadays are more active than before, so uploading personal information over the platforms won’t be a smart decision. These Cloud-Based platforms are vulnerable to getting hacked by cybercriminals; that’s why organizations need professionals to fight against such attacks.
Hackers are trained well and known to be very professional while doing their work. Cybersecurity is needed to protect your network, systems, and devices from unauthorized access. These people try to get to your systems, find the vulnerabilities, and exploit them, then get the data out of your system to threaten you for breaching it and leaking it to other competitors to get a ransom amount from you for monetary gains.
Cybersecurity involves professional hackers, techniques, and tools to fight against online criminals. These techniques are practiced and used by professionals legally for the benefit and security of organizations.
Hackers are becoming better and using sophisticated tools. We are no longer in a phase where simple antivirus or firewalls could protect against Information breaches. These vulnerabilities are skyrocketing, and therefore, there is a hike in demand for cybersecurity professionals.
Cybersecurity is no longer limited to IT industries; due to the change in nature of business and the shift towards digital, every industry needs information security. It is better to care about your data security than repent later. As they say, “Better safe than sorry.”
Why Do We Need Cybersecurity?
Everyone needs cybersecurity to get protection against online threats that could harm them online, and after getting access to their systems without getting noticed, they will steal that data. Besides that, most of us upload our daily life routine works on the internet. These datasets are saved online on those sites, and as you know, adversaries are available over the internet, so anything could happen to that dataset. To protect yourself from becoming a victim of those attacks, you need to make sure that you have expert support to get over the attacks with ease.
What is Enterprise Cybersecurity?
Organizations are dependent on information and technology to maintain their business very much. Moreover, the online platforms they always use to stay connected to their customers are not secured that much without the help of professional cybersecurity experts. They need professionals to help them secure their devices, networks, and systems from getting hacked/ attacked by cyber criminals with the support of the latest cybersecurity tools and technology.
Why Is Cyber Security Important?
Information, communication, and technology have surpassed their limits while continuing to grow more ‘n’ more. Decades have made an amazing change in the working & socializing structure of the global population. All of them have transferred socializing over the internet and made themselves open to the whole world so everyone could become their audience, and they could connect to their audience any time they want to.
Devices these days have turned too smart for the well-being of the humane society. However, that doesn’t mean it’s healthy for the working environment of the people in any field. The devices save our confidential information, passwords, security contacts, card details, and so much more. Cloud helps most people to save their data in a wide and safe space, where only the person who has access/ key to the database can access the data stored in the account.
Cloud spaces are provided by Google, which is Google Drive and Dropbox. However, these are vulnerable too, so they could get exploited with ease with the support of a professional hacker/ or practitioner. The government also has a part of access to those accounts in case any crime happens.
Hold of that much data could be in responsible hands. Otherwise, national security could get into a problem. Therefore, every nation should focus on cybersecurity to reduce the chances of losing control of the datasets. This much is already enough to secure any organization or an individual.
You can get to the professionals like Craw Security for a perfect solution. They have been offering cybersecurity courses to aspirants of cybersecurity for a long time. With the support of professionals, you will understand the real meaning of cybersecurity, how experts handle the situation, and how the tools are used to offer you the best solutions. Let’s read further about this.
Difference Between Cybersecurity and Information Security
| S.No. | Cybersecurity | S.No. | Information Security |
| 1. | Cybersecurity is needed for the protection of the systems that are working with the data online and are in use to share online information with others through networks.
These networks are vulnerable and can be hijacked by any adversary who wants to steal the data used by the organization to make records. These records include confidential data related to the company, clients, owners, businesses, and many more. Also, if this information gets leaked in any way, it can become the reason for the organization’s downfall. It can leave a damn scar over the brand’s face and make the company lose face in front of the clients/ customers. |
2. | Information could be offline and online. However, if we talk about information security, then it is necessary to understand that anybody who doesn’t got the knowledge of how to protect their information should learn it from professionals, and it can be based on offline data protection or online data protection.
For this, an individual must seek professionals with experience in information security. They use several methods and ask some groups who can provide a better remedy for the protection of your information offline. It could be related to your hardware, which stores the data offline, and the chipsets that you use to store that data over the system. |
How is Cyber Risk Measured?
After following the below steps, you can get the results you wanted in the first place. These steps are specially designed to assess how Cyber Risk is Measured.
- Identify and prioritize assets.
- Identify vulnerabilities
- Assess the probability of a security incident
- Calculate threat impact
- Calculate risk.
- Create a risk matrix for remediation planning.
- Risk = Likelihood x Impact.
How is AI Used in Cybersecurity?
AI is human intelligence calculated and got turned into a virtual brain that learns, researches, stores records, and learns from past experiences. That’s so that the devices in which they’re implanted could learn about the attacks and react ASAP.
AI is nowadays available on every other device. Also, some devices already have access to AI, so they can react to the threat on time and can stop it from becoming worse for the device. In the meantime, the practitioners follow the pattern and learn how to make stronger security measures to stop those who are coming to interpret the work of the device itself. So, AI is better for the organization and is helpful in increasing security for the clients connected to it.
Effects of Cybercrime
There could be less than we think and more than we thought, so you can’t be that one who ignores the signs of alert from past incidents that have happened to your organization because of the low-security measures. Some of the effects that cybercrime can leave on the victims are as follows:
Monetary Issues: you know we spent so much on the assets that are useful in the maintenance of the organizational operations. However, due to the damage that was caused by cybercrime, we lose so much more than we could ever think. Some of those things are – Trade Secrets, Intellectual Property, and Damage Control Costs against data breaches.
Clients Data Loss: Customers or clients that are related to you could probably lose the data, and in return, this can destroy the belief of the people in the company. Clients can lose their faith in your firm after such incidents.
Legal Notice from Security Boards: lack of installation of cybersecurity tools can lead the organizations towards fines and legal notices from Regulatory bodies.
Organizations need to understand the importance of cybersecurity and should invest in it. Otherwise, anything could become a risk for the firm. Employees should be aware of the potential risks and be prepared for the training.
Defense-in-Depth (DiD) Cybersecurity
- Antivirus software.
- Network security controls
- Data integrity solutions.
- Behavioral analysis.
- Policies and procedures
Top 4 Cybersecurity Practices
Employees are one of the most important resources responsible for the security and regularity of work. That’s why they should be aware of information security, with the ways of protecting the data with the tools needed. Sensitive information, if leaked, could take a very disastrous form, affecting many people.
The company’s Security Administrators appoint a whole IT group to keep the firm’s data safe. However, that’s not the only thing a company should think about. Predicting the threats and intentions after malicious attacks can’t be believed each time, so at least one should be prepared for the outrun.
Human errors are one of the reasons for breaches in an organization’s system. Security Professionals try to secure the networks and systems from getting hacked if there are any human errors. Moreover, even if you have the best security application, you won’t be able to secure your firm’s full
Here are 4 best practices to ensure cybersecurity in the workplace:
- Cyber Security training for employees
Training employees regarding how the threats work and what could be the common possible ways they can fall into the traps of hackers. Awareness training should include Phishing, Ransomware, Vishing, etc. Email phishing has become very common.
Employees should be aware of checking the authenticity of the sender’s email ID. Sharing confidential information without confirming it can be detrimental. The training should also include some basic measures to avoid human error.
- How to Setup Email Authentication Protocol
This is essential to ensure email deliverability by preventing spam. Phishing and other social engineering attacks, mainly by forging the sender’s name and other details, can be prevented.
Prevention of surpassing such forged mail into the system can make it easier for the IT department to ensure more safety. Desired tools that enable Complete Email Channel Monitoring along with Dynamic SPF (Sender Policy Framework), Dynamic DMARC (Domain-based Message Authentication, Reporting & Conformance), and automatic detection of SPF IP and DNS update. Deploying such tools and making employees aware of them can be very helpful.
- Email authenticity Verification
Phishing emails are difficult to recognize as cyber criminals use sophisticated tools and techniques by spoofing known email addresses, names, etc. Providing personal or professional information to such emails can corrupt the entire system.
These cybercriminals use financial incentives to lure employees or sometimes forge the identities of the bosses to get the receiver of the mail to respond immediately and share information.
It is pivotal for any organization to implement an email authenticity verification solution in an organization to report suspicious-looking emails instantly, and after reporting, such emails should be deleted from all other inboxes of the employees.
- Continuous Brand Monitoring
The brand is the face of any organization, and that represents the value of that organization. Some fraudulent practices can affect how the brand treats its customers, their complaints, etc. Proactive brand monitoring makes it easier to detect and resolve such issues happening on domains, websites, or mobile applications of the organization.
Cyber-attacks have become more common and sophisticated in the past decade, and therefore, it is essential that the above-mentioned practices are deployed in the organization to ensure the smooth functioning of the organization and the safety of the data.
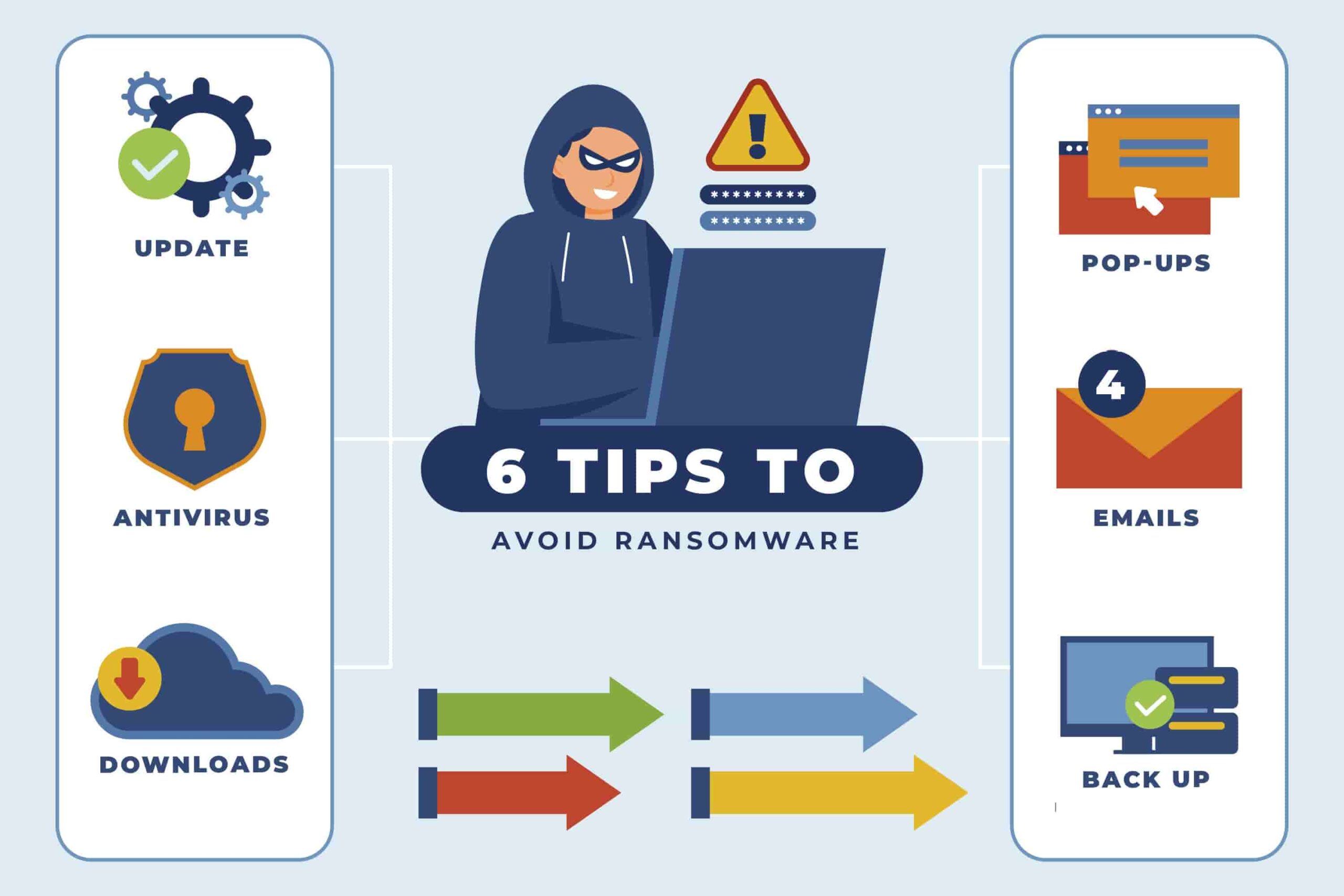
How to Implement Cybersecurity?
- Analyze and manage risks.
- Inventory and manage assets.
- Identify and address vulnerabilities.
- Deploy identity and access management.
- Data security.
- Incident management.
- Supply chain security.
- Employee training
Frequently Asked Questions
About Why Need For Cyber Security Now A Day
- Should Cybersecurity be Part of Your Business Continuity Plan?
Yes, of course. If you could make it a part of your business continuity plan, you can continue to serve your customers with the utmost secure platform and services. With the help of cybersecurity, they’ll feel safer and be moderate while using your services. So, when will you make changes in your organizational plan, including cybersecurity?
- Why is safety so important?
Safety is more important everywhere than anything else you do, whether it is offline or online. That’s because when you find yourself in a place where your data is in the hands of someone unreliable, you’ll feel insecure.
Most times, that could be someone who wants to threaten you for money in exchange for releasing your data’s access. This could be uncomfortable for you. For that, you need safety, whether offline or online.
Moreover, for online data, you can contact a cybersecurity expert such as Craw Security. For more info, contact us now!
- What is network security?
A network is a wide connection that connects several users with one platform, and their data is get saved on that platform until the access holder of that data deletes that data from its database. This continues until the application or website comes to an end.
The network holds those people’s data security and ensures that the data don’t get leaked by the access holder’s hand. Network transfers data in small packets from one place to another so that the transferable speed won’t get disturbed.
Data Snatchers snatch those data packets to sniff them and use them against the victim to make monetary gains.
- Why is physical security important?
It is important for any business to put a cap on certain things to make them secure from unauthorized access. Just like that, businessmen want to protect their personal belongings, properties they own, and hardware from unauthorized access.
Sometimes, it could be physical actions that could damage or cause a serious loss to the victim. There, physical security secures data from getting breached and protects your physical office environment. So, now you might have understood why physical security is important.
- Why is it important to give training to all people?
That’s because everyone is on the internet nowadays and needs protection against certain unidentified online threats. These are none other than the adversaries. An adversary would try to get to your database via a specially customized link that could get control of the victim’s system in no seconds.
After that, they would gradually get the data from the database of the victims and make monetary benefits from it by unleashing that data for those who want to pay for that confidential information to use against the victim.
After getting trained on how to observe, find, and stop the unknown operations happening over the system, victims will be able to protect their system from unauthorized access.
- How many layers of security are there?
The seven Cyber security layers are as follows:
- Information Security Policies
- Physical Security
- Secure Networks and Systems
- Vulnerability Programs
- Strong Access Control Measures
- Protect and Backup Data
- Monitor and Test Your Systems
- Do companies have to pay a heavy price to recover lost information?
It depends on how much data has been lost or breached. Moreover, the charges won’t be low. The simplest answer for that would be – information about someone is very important for them, cuz that data could be used in favor of the person or against the person.
Anything is possible. So, in this case, that data becomes confidential and sensitive information, which needs protection from a protective layer to secure it against cybercriminals who could use it for mean purposes.
For that, organizations/ individuals need professional security experts who could help them increase their security and to protect themselves against the bad elements of society online. If you’re searching for a training institute, you can contact Craw Security to get professionals to work for you. What are you waiting for? Contact, Now!
- Is online shopping a threat?
Well, not each time that could be a threat. However, every time we start shopping online, we should consider looking for the website’s legitimacy cuz several malicious developers could create a similar-looking website to deceive innocent people.
These websites are linked to a backdoor where they could get your cards tapped and move the money in without getting noticed. So, learn about cybersecurity to get aware of such activities.


















