What is Ethical hacking? | Career opportunities | Roles and Responsibilities
What is Ethical hacking? | Career opportunities | Roles and Responsibilities
What is Ethical Hacking?
What is ethical hacking? Many of you may know about it and many don’t. So, we can just keep learning step by step. The digital world is expanding day by day, and you ain’t going to be left behind. So, be ready for everything.
And if we’re talking about digital things then the online data can’t be left behind too. Where these things revolve, online threats stay too. In the digital world, one of the words which circle the most is “hacking”.
The skillful people with these kinds of skills can be good or bad in the way they do things. Some people do things in the right way by choosing to provide benefits to the digital world. And some of them are just greedy, and out of greed choose the path of deceiving. But whatsoever! We’ll unclog things step by step. Let’s start with hacking!
Hacking! What’s that?
Hacking means optimizing data, websites, or using someone else’s personal account without their consent. For ex- you’re a person who’s hacking someone else’s website, or database, and trying to steal their data for your cause. Next, we should get to the main keyword “Ethical hacking”.
What is Ethical Hacking?
Ethical hacking is done by a skillful professional for providing security against an online threat. Many people who are skilled in hacking skills try to deceive innocent people with their data. And to save themselves, businessmen contact ethical hackers. They check the vulnerability, bugs, loopholes, and many things that can put the data in danger.
Many people choose the profession of ethical hacking or penetration testing. And they think about these things as the best career options for life & growth. Why? There can be many reasons. That’s because many website owners and bank representatives lose their hope after a loss of data is hacked by a hacker. You can take ethical hackers as “antivenom to venom”.
Penetration testing is one of the important parts of cyber security. This can help to know the vulnerabilities in computer systems, websites, networks, and applications. After penetration, ethical hackers can solve the issues much faster. And resolving matters related to data will be solved with pace too.
Cyber Security Threats
Everyone is aware of online threats and cyber crimes happening worldwide. And these cases are increasing day by day. To stop them digitally you’ll have to take precautions and at the same time “remedy”. The remedy to this issue is to contact a cyber expert.
These kinds of crimes can be done by sitting on a lousy couch and from a single screen. And anonymously 100s of systems can be jacked by a single system. How’s that?
Types of ethical hacking
There are 5 types of Ethical Hacking. here we will talk all about them.

Types of ethical hacking
You’ll See 5 kinds of ethical hacking which are written down below.
| Types | Definition |
| Web Application Hacking | This is the process of interfering with the URI by using the visual chrome Browser over HTTP. Or collusion with HTTP aspects not stored in URL. |
| System Hacking | Simply, we can say that system hacking is a process of getting control of a personal computer over a network via system hacking. Some types are – (i) password busting, (ii) phishing, (iii) malicious software construction, and (iv) packet sniffing. |
| Web server hacking | An Application Web Server Generates data in real-time on its system server. So attackers use their techniques to grab credentials, Passcodes, and company data right from the webserver. |
| Hacking wireless networks | Wireless networks use radio waves to transmit signals. So hackers can easily access the system from a nearby location. To discover, identify and bodge a wireless network these individuals use network snorting. |
| Social Engineering | Social Engineering is the art of manipulating people so they can give some confidential data. This data can be used in any cybercrime activity by cybercriminals. |
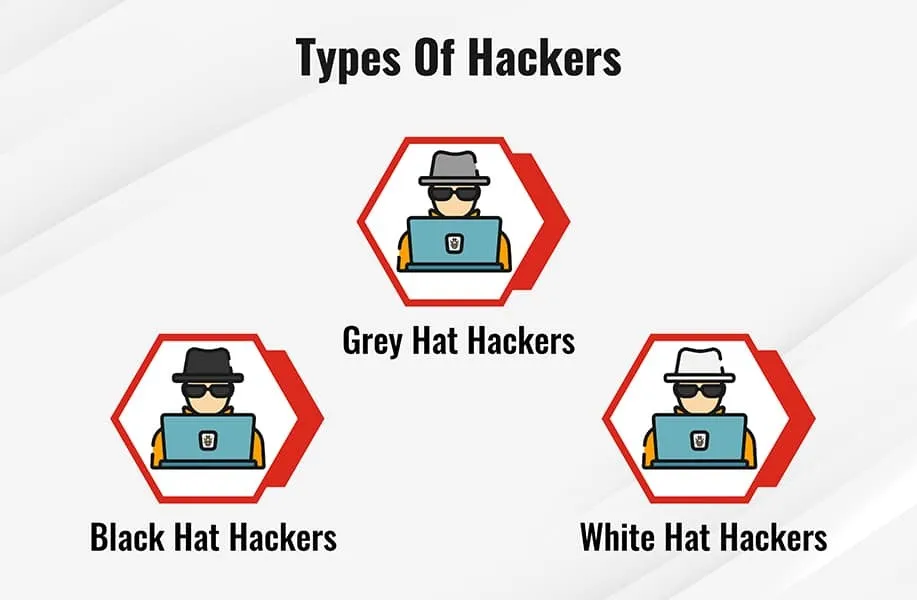
How many types of Hackers are there?
There are kindly 3 types of hackers that are listed below
| Types of hackers |
| White Hat | Gray Hat | Black Hat |
| White hat hackers are also known as ethical hackers and are cyber security experts.
They support the Government and businesses by performing penetration testing. That is just to identify the security flaws. These hackers always use techniques to protest against black hat hackers and cybercriminals. |
Gray hat hackers stand in the middle of white hat hackers and black hat hackers.
They can be partial or generous. Nobody ever saw them using their skills for personal means. |
Black hat hackers are the main Delinquent of cybercrimes.
They look for loopholes in computers, businesses, and banking systems. These people can hack your networks and intrude on your business data gallery. Sometimes your personal information. |
The best thing about Ethical Hackers
- They test the security level in a network
- Professionals in creating penetration testing reports
- They perform penetration testing on the systems
- Once the issue is found out, they search for the best security solutions for troubleshooting.
- Also, they verify the organization’s system and network, while finding vulnerable entry points of the system.
- Documenting the security flaws and vulnerabilities is their priority.
Career and jobs in Ethical hacking
Oh! Do you want to become an ethical hacker? To know “What is Ethical Hacking” you must find a certified ethical hacking institute. And after the clearance of your course, you don’t need to worry about placements. There is no shortage of ethical hacking jobs in the world. This is the most growing industry also in the international business field.
In India, there is high demand for Cyber security analysts, consultants, and engineers for filling in reputed IT companies.
The Initial salary of an entry-level certified hacker in India for a fresher is approx 5 to 7 Lakhs/annum. In rupees that would be 41k to 58k per month
Work as a Freelancer
There are various opportunities for freelancing. First, complete the ethical hacking course from a verified cyber security training institute. Then you can try doing some work for others. That would be a great approach for a better future.
Who can pursue this course?
Those who think that there is anybody who can’t pursue based on their stream can be relieved. That’s because there’s no law, or any written legal thing that says you as a student of science/commerce/arts can’t pursue this.
These courses are available for everybody who’s seeking knowledge in this field. So, everybody can be relieved. Whether you’re a 10th, standard student, or 12th, or maybe in college/job, you can pursue your dream.
Q&A Related to ethical hacking
- Can we pursue ethical hacking after the 12th?
Yes, you can pursue ethical hacking after the 12th. There’s no legal restriction or obligation that stops an individual from pursuing such courses.
2. Is job placement guaranteed after taking an ethical hacking course?
Yes, you can pursue ethical hacking after the 12th. There’s no legal restriction or obligation that stops an individual from pursuing such courses.
3. Can I get training in Delhi for ethical hacking?
Definitely! Every year 100s of 1000s of placements vote out for ethical hackers who have done this course. There is a genuine reason behind this. You know that every company has been digitalized for years. So, the fear of online threats has increased. That’s why the demand for such cyber experts has also increased. Yes! You can pursue ethical hacking in Delhi. And there are three top institutes available in Delhi that are providing an “ethical hacking course”.
- Crawsecurity
- Bytec0de
- Udemy
For experts and professionals’ coaching, you can trust Crawsecurity. They have more than 15+ years in the field of cyber security.
Conclusion
After all the discussion at the top, we can say there’s a lot to learn about ethical hacking. And you can give it a go if you like. Whether it is hacking or security performances, you need to go to the best people. So, now, craw security is giving you the chance to get the best tutors to work for you, and train you to be the best performer in the cyber field. Contact us via mail.
















