Methods & Techniques of Cyber Forensics [Updated 2025]
Methods & Techniques of Cyber Forensics [Updated 2025]
Digital Forensics or Computer Forensics is a prime technique for finding pieces of evidence from digital assets containing sources. The investigator who does all the processing is widely termed a Cyber Forensics Investigator. In addition, these varied techniques of investigation and analysis collect and retain evidence from an individual computing device in such a manner that is duly appropriate for admissible in a court of law.
The primary target of computer forensics is to execute well-established research and hold a documented series of evidence to obtain the exact chronological order of what happened on a computing device and who was accountable for a particular cybercrime. In short & crisp words, cyber forensics, which is also known as cyber forensic science, is technically a data recovery process from digital info possessing resources in compliance with legal authorities and strict guidelines to maintain the integrity of the original resource of the evidence.
Types of Cyber Forensics
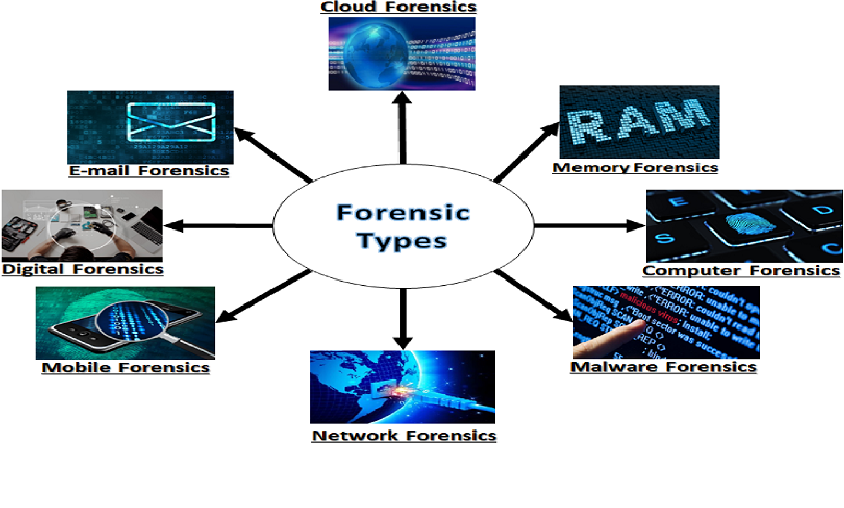
There are numerous types of cyber forensics techniques are there that are widely employed by several forensics experts all over the world that employs them for obtaining sensitive pieces of information from digital resources. Some of the famous types of cyber forensics are mentioned below:
- Network Forensics
- Email Forensics
- Malware Forensics
- Memory Forensics
- Mobile Phone Forensics
- Database Forensics
- Disk Forensics
Moreover, we have elaborated on the above-mentioned Methods and Techniques of Cyber Forensics in the following points one by one:
- Network Forensics: It is a widely used technique to monitor network traffic to extract pieces of information from distinguished networks using some dedicated tools like a firewall or intrusion detection system.
- Email Forensics: The genuine process of analyzing and recovering emails and other crucial attachments is comprised of the email platforms like contacts and schedules.
- Malware Forensics: In this methodology, forensics experts sift through code to check for potentially malicious programs and scrutinize their payload. In addition, these particular sorts of programs might comprise Trojan horses, ransomware, or several viruses.
- Memory Forensics: This particular form of forensics ranges from Memory Forensics to collecting data kept in a computer’s RAM (Random Access Memory) and cache files.
- Mobile Phone Forensics: In this type of forensics, the team of forensic scientists or experts examine the mobile devices to retrieve and scrutinize the datasets they possess, including contacts, geolocations, SMSs, images, audio & video files, and third-party apps databases such as WhatsApp, Facebook, Twitter, etc.
- Database Forensics: The process of examining the info comprised in the databases, such as data and the adjoining metadata, is widely known as Database Forensics.
- Disk Forensics: In this particular case, forensic experts try to obtain crucial pieces of information from digital data storage media like Hard disks, USB devices, Firewire devices, CDs, DVDs, Flash Drives, Floppies, etc.
What Are Digital Forensics Tools?
Nowadays, where forensics science is at its optimum level, and forensics experts are literally helping the police and investigation agencies to obtain crucial pieces of evidence, it is a high need that we understand the usage of some dedicated Digital Forensics Tools massively employed for extracting the info containing databases as evidence duly admissible in the court of law. In addition, some of the prominent Digital Forensics Tools are mentioned below that are described later ahead:
- The Sleuth Kit
- FTK Imager
- Xplico
The Sleuth Kit®
This software is basically a gathering of command line tools and a C library that permits one to scrutinize disk photos and retrieve files from them. In addition, it is highly utilized behind the scenes in Autopsy and numerous other open-source and commercial forensics tools.
FTK Imager®
This tool is generally a data preview option and imaging software that genuinely lets you quickly evaluate electronic proof to decide if additional analysis with a forensic tool such as FTK® is authenticated.
Xplico
In general terms, Xplico is a Network Forensics Analysis Tool (NFAT) that is used to rebuild the contents of investments functioned with a packet sniffer (e.g. Wireshark, tcpdump, Netsniff-ng).

Techniques Used in Cyber Forensics
Digital Investigators or Computer Forensics Experts utilize a series of tactics and techniques with a genuine usage of forensic tools to verify the copy of evidence document they have seized from a compromised computer or device. In addition, they go for a search for hidden or encrypted folders and unallocated disk spaces for traces of deleted, encrypted, overwritten, or tampered files, and all the shreds of digital copies are nicely documented in a proper manner for filing a report duly admissible in the court of law without being harming the original source of the evidence and maintaining its integrity.
However, these Methods and Techniques of Cyber Forensics utilized by digital investigators are a combo of tricks, tactics, and techniques with a piece of expert knowledge. Some of the prominent techniques are as follows:
Cross-Drive Analysis
This particular technique associates and counterparts datasets found on several computer drives to look for scrutinizing and maintain info regarding a forensic analysis. Moreover, events that enhance the hunch are dedicatedly compared with data on another drive to watch for likeness and offer context.
Live Analysis:
In this particular tactic, a system is scrutinized from inside the operating system while the system or equipment is functioning, utilizing system tools on the computer. In addition, the corresponding analysis of volatile data is generally stored in cache memory or RAM. Several tools were utilized to obtain the volatile data need the computer in to be in a particular state within a forensic lab to keep up the integrity of the original source of the evidence.
Deleted Files Recovery:
As the name suggests, in this technique, forensics experts will be able to retrieve the database of the deleted files that were partially deleted in one place but left some traces elsewhere on the particular system while searching for a computer or any other corresponding device and even the memory for fragments of files. Moreover, this individual technique is widely known as file carving or data carving.
Stochastic Forensics:-
In this technique, forensic experts scrutinize and rebuild the digital process without the usage of digital artifacts. Furthermore, the artifacts are clues regarding a digital crime, like alterations to file characteristics during a data heist. Moreover, stochastic forensics is continually utilized in data breach examinations where the hacker pretends to be an insider who might not leave any digital artifacts behind.
Steganography:-
It is a basic technique utilized to conceal data within any sort of digital file, context, or data stream. In addition, computer forensic experts reverse a steganography effort by understanding the data hashing of a particular file to map its data of any corresponding size to a fixed length. If, in case, any cyber criminal encrypts any confidential data inside an image, video, or any other digital file, it might be able to look exactly the same prior or after to the common perception; however, by the usage of the hash or string of data that portrays the image will transform.
Skills Required to Become a Cyber Forensic Investigator
There are numerous designations or positions where a person can dedicatedly work as a proven Digital Forensics Investigator in various organizations hailing from several different niches in the global market, such as the following:
- Forensic Engineer: These particular professionals deal with the gathering phase of the computer forensic methodology, collecting data, and getting it ready for scrutinization. In addition, they assist in establishing how a piece of equipment failed.
- Forensic Accountant: In this position, an expert deals with cyber crimes comprising money laundering and other transactions made to hide illicit operations.
- Cybersecurity Analyst: This particular position deals with scrutinizing the datasets once they have been gathered and withdrawing intels that can further be utilized to enhance an enterprise’s cybersecurity strategy.
Moreover, one can grab many courses in Graduation, Post-Graduation, Diploma, and Certification levels to complete their sincere knowledge related to Cyber Forensics Experts deeply enhance their knowledge related to Methods and Techniques of Cyber Forensics. In the same vein, if you wish to become a prominent Digital Forensics Investigator, then you may sincerely join the Govt. of India-approved Cyber Forensics Investigation Course in Delhi by Craw Security – the best cyber security institution in India.
Requirements to Become a Forensic Expert
In the varied cyber forensics institutes in the wild, there are certain requirements that you should have in order to get enrollment in the particular course curriculum, such as the following:
- Good knowledge of Networking Administration.
- A fine understanding of Linux Essentials.
- Hands-on practice in Python Programming Language.
- A keen understanding of Ethical Hacking fundamentals.
Frequently Asked Questions
About Methods and Techniques of Cyber Forensics
- Is Digital Forensics a Good Career?
Yes, it is a booming industry as maximum crimes crucial pieces of evidence are available on digital assets or in electronic form, and to extract these particular shreds of datasets, an investigation agency dedicatedly requires experienced Digital Investigators.
2: What are the different types of cyber forensics?
There are many types of cyber forensics nicely available in the market that one can employ in the following:
- Database forensics
- Email forensics.
- Malware forensics.
- Memory forensics.
- Mobile forensics.
- Network forensics, etc.
3. Who uses cyber forensics?
Cyber Forensics is dedicatedly used by Digital Forensics Investigators for extracting crucial info in digital assets possessing resources or information in electronic soft copies. These investigators might hail from state-owned organizations, govt. Approved agencies or private law enforcement bodies.
4. What is meant by cyber forensics?
The process is widely employed by digital forensics investigators to obtain information that is being stored from the seized digital assets possessing resources from the crime scenes by police or forensics investigators. In addition, this can be very fruitful in cases of intellectual property heists, deceits, employment arguments, bankruptcy investigations, and fraud compliance.
5. What are the 3 main branches of digital forensics?
There are many branches of digital forensics, and we are mentioning the three main branches of digital forensics as follows:
- Mobile Phone Forensics
- Network Forensics
- Computer Forensics
Conclusion
In a nutshell, we want to state that there are various methods and techniques of cyber forensics that professional digital investigators employ to extract the crucial shreds of evidence from various resources such as mobile phones, computers, laptops, floppies, flash drives, etc. However, through Craw Security’s authentic cyber forensics institution, one can certainly have the best knowledge related to digital forensics under the premier observation of excelled cyber forensics investigators as training instructors with more than 7 years of quality industry experience.
















