Importance Of Penetration Testing For Today’s Infrastructure
Importance Of Penetration Testing For Today’s Infrastructure
Importance of Penetration Testing for Today’s Infrastructure
Can you explain what the term “penetration testing” means to you? One method for locating vulnerabilities in a computer system, network, or web-based application is to simulate an attack from a hacker or another hostile actor. This is done in order to uncover vulnerabilities. The usage of penetration testing is required for any business that places a high value on the protection of its confidential data and is interested in preventing cyber attacks.
Now that we have established what penetration testing is, why it is necessary, and how it operates, we will discuss the significance of penetration testing for the future of the organization. In addition to helping to clarify a few questions and misunderstandings that are frequently asked, we will also provide some guidance on how to begin conducting penetration testing.
Introduction:
Cyber threats are becoming increasingly complicated and broad in the 21st century, which is a time when technology is evolving at a rate that has never been seen before. To circumvent security measures and gain access to confidential information, hackers are always looking for new potential entry points. Therefore, to make sure that their data and assets are protected, companies need to always remain one step ahead of these threats.
make sure that their data and assets are protected, companies need to always remain one step ahead of these threats.
It is one of the most effective techniques to prevent a cyber assault to conduct penetration testing on a regular basis. Simulating an attempt to hack into a computer system or network is what is known as penetration testing. The goal of this type of testing is to identify vulnerabilities and flaws that could be exploited by an adversary.
What is Penetration Testing?
Penetration testing, also known as pen testing or ethical hacking, is a method that simulates an attack from a hacker or another malicious actor in order to evaluate the security of a computer system, network, or online service. This is done by simulating an attack. The purpose of penetration testing is to identify vulnerabilities and weak points that an attacker could exploit in order to gain access to the system.
The process of penetration testing can be carried out in a number of different methods, such as through social engineering, testing of web applications, and testing of networks. Among the procedures that comprise the process are reconnaissance, scanning, exploitation, and post-exploitation. These are just a few of the processes.
The Importance of Penetration Testing for Today’s Infrastructure
In today’s interconnected world, where the majority of enterprises rely on technology to run their operations, cybersecurity has arisen as a primary worry that needs to be addressed. It is possible for a cyber attack to have severe consequences, such as monetary losses, negative publicity, criminal culpability, and regulatory fines.
When it comes to the fight against threats that can be found online, penetration testing is an important instrument. Prior to hackers being able to take advantage of vulnerabilities in a company’s software and systems, it assists organizations in finding those vulnerabilities. Conducting penetration tests on a regular basis allows organizations to check that their security measures are up to date-and effective in avoiding cyberattacks.
A further benefit of penetration testing is that it supports businesses in meeting the requirements of various legal and regulatory bodies. Numerous sectors, notably the healthcare industry and the financial industry, are subject to stringent data privacy laws and regulations. Through the implementation of penetration testing on a consistent basis, enterprises have the ability to demonstrate to regulatory bodies that they are taking the necessary procedures to safeguard sensitive information.
Why Is Penetration Testing Important?
A survey was administered to 350 companies from 11 different countries that had experienced data breaches as part of a study that was carried out by the Ponemon Institute in 2015. The study focused on the cost of data breaches. When it comes to the breaches in question, over half of them (47%) were the result of hostile attacks, while the remaining breaches were the consequence of system faults and human errors.
- Preparation For An Attack
An organization’s workers may learn how to respond to any kind of break-in from a malicious entity through the use of penetration tests, which is the primary reason why these tests are so important to the organization’s security. A penetration test is a method that can be utilized to determine whether or not the security policies of a company are truly effective. Organizations can use them as a form of fire drill that they can practice.
Penetration tests can also provide solutions that will assist organizations in not only preventing and detecting attackers but also removing unwanted intruders from their systems in an effective manner. These solutions can be provided by penetration testing.
- Risk Identification
In addition, penetration tests provide information about which channels within your business or application are most vulnerable to attack, and as a result, they can help you choose the kinds of new security solutions you should invest in or the protocols you should apply. This procedure has the potential to guide you in identifying a number of significant system flaws that you might not have even considered.
- Decrease Amount Of Errors
This can also help developers make fewer mistakes, which is another benefit of penetration testing reports. This will cause developers to become more committed to learning more about security and will reduce the likelihood that they will make mistakes that are similar in the future. When developers comprehend how exactly an attacker launched an attack on an application, operating system, or other software that they helped design, they will be ready to learn more about security.
It is also vital to remember that conducting penetration testing is of utmost significance if your firm is in the following situations:
- In recent years, significant renovations and other modifications have been made to the company’s information technology infrastructure and applications.
- A new office location was just recently transferred to.
- Has applied any available security fixes, or
- Policies for end-users have been updated.

How Penetration Testing Works?
In order to assess the safety of networks and systems, the process of penetration testing entails carrying out a series of stages, some of which are listed below:
- Reconnaissance
When doing a penetration test, the first step is to conduct reconnaissance. In order to accomplish this, it is necessary to gather information regarding the target network or system, including the domain names, IP address range, and server architecture. There are a number of methods available to obtain this information, such as social engineering and network mapping approaches.
- Scanning
This is followed by the procedure of scanning. In order to accomplish this, automated tools are utilized to locate vulnerabilities in the system or network that is being attacked. These vulnerabilities include open ports, servers that are wrongly configured, and software that is not up to date. Furthermore, scanning can be of use in detecting potential entry points that could be exploited by attackers.
- Exploitation
After vulnerabilities have been identified, the next step is to exploit the vulnerability. This necessitates making an effort to exploit the vulnerabilities in order to get access to the system or network that is the target. This can be accomplished through the utilization of a variety of methods, such as SQL injection, cross-site scripting, and buffer overflow attacks.
- Post-Exploitation
The final part of a penetration test is called the post-exploitation phase. Maintaining access to the system or network that is the objective of the acquisition is required in order to acquire private data in this manner. The significance of this step lies in the fact that it illustrates the potential damage that may be caused by a hacker if they were to successfully hack into the system without authorization.
In order to conduct penetration testing, it is possible to make use of both human and automated technologies. In the vast majority of cases, manual penetration testing is more comprehensive and has the ability to discover vulnerabilities that automated tools could miss. However, it not only takes more time but also costs more money.
On the other hand, automated penetration testing is more efficient and less expensive than manual testing, but it falls short of being as comprehensive as manual testing. False positives can also be generated by automated systems, which results in a waste of both time and money.
Common Misconceptions About Penetration Testing
There is a large number of people who have beliefs that are not consistent with what the listeners have heard.
- Penetration testing is only necessary for large organizations
A significant number of companies, regardless of their size, believe that they are not susceptible to cyberattacks and, hence, do not require penetration testing. However, this is a potentially dangerous misconception. Little businesses are typically the target of cybercriminals since it is commonly believed that they have a lower level of security compared to larger corporations.
- Penetration testing is a one-time event.
Ongoing risk assessments ought to be carried out. Discoveries of new vulnerabilities are made on a regular basis, and the dangers that exist online are always evolving. By conducting penetration tests on a regular basis, individuals and organizations may protect themselves against such dangers and make certain that their security measures are correct and up to date.
- Penetration testing is too expensive.
The chance exists that penetration testing will be expensive, particularly when it is performed manually. However, the cost of a cyber attack can be significantly larger than the cost of a physical attack. This cost can include everything from legal liability to administrative penalties, financial losses, and poor PR publicity. In the long run, penetration testing is an investment that is well worth doing.
Tips for Getting Started with Penetration Testing
Learn how to do a penetration test by following the instructions that are provided here.
- Define your scope
A thorough understanding of the scope of your penetration test is required before you get started. To accomplish this, it is necessary to select the applications and systems that will be evaluated, as well as the specific goals of the test.
- Choose the right testing methodology.
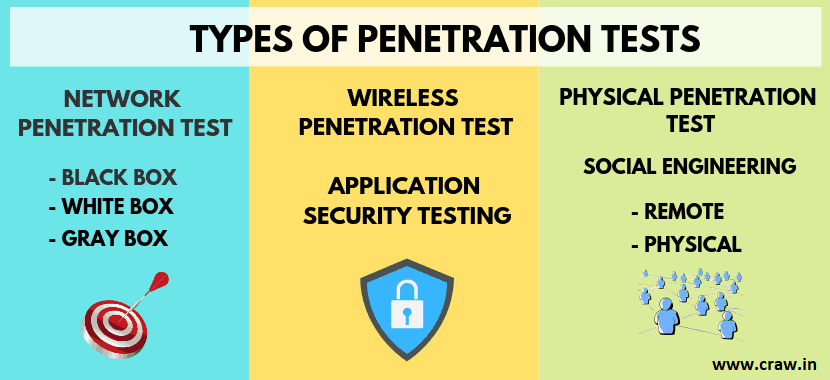
There are a few different testing methodologies that can be utilized, including black-box testing, white-box testing, and gray-box testing examples. Because every method has its own set of advantages and disadvantages, the decision will be made depending on the specific test objectives.
- Hire a reputable testing provider.
Working with a trustworthy testing company is necessary if you do not possess the necessary competence to carry out penetration testing on your own. You should go with a service provider who has previous experience in your industry and who can provide references and testimonials from satisfied clients.
- Take action on the results.
In the process of a penetration test, taking action based on the findings is a vital component. Among these are the implementation of measures to prevent the problems that were discovered from being used in the future and the resolution of the problems that were discovered.
Seeking More Information About Penetration Testing
Chat with the knowledgeable cybersecurity experts at Craw Security, Saket, and Laxmi Nagar to acquire additional information regarding the advantages of penetration testing and/or to make arrangements for the provision of such a service. Craw Security is a one-stop solution that offers top-notch solutions for risk management and cybersecurity to both commercial and federal clients.
This is made possible by the company’s highly technical knowledge and specialized training. To identify any potential flaws before they can be exploited, the pen testing branch of Craw Security employs strategic hacker tactics in a controlled environment. This technique is used to reveal any potential weaknesses. Craw will also provide guidance on matters about compliance.
FAQs
About the Importance of Penetration Testing for Today’s Infrastructure
1: What are the Benefits of Penetration Testing?
The following are the benefits of Penetration Testing.
- Identify Security Flaws,
- Assess Security Controls,
- Enhance Security Measures,
- Compliance, and
- Peace of Mind.
2: Is penetration testing a legal requirement?
In most cases, the law does not mandate the presence of penetration testing. Nevertheless, it is commonly recommended against industry recommendations and standards such as PCI-DSS, HIPAA, and ISO 27001, among others. The implementation of these standards requires enterprises to conduct security tests and assessments on a regular basis to ensure the continued safety of their systems and protect themselves from the possibility of data breaches.
3: How often should penetration testing be conducted?
A number of factors, including the size and complexity of the company’s information technology environment, the confidentiality of the data that is being secured, and the risk profile of the organization, are taken into consideration when determining the frequency with which penetration tests are performed. It is typically recommended that enterprises conduct penetration testing at least once a year and more frequently for high-risk systems and applications. Penetration testing is a critical security measure.
4: Can penetration testing cause damage to my systems or applications?
Penetration testing is a technique that simulates a real-world cyberattack to identify vulnerabilities in a system’s security mechanisms. Even though it is conceivable for penetration testing to result in temporary disruptions or downtime, a competent and experienced penetration testing organization will take precautions to prevent the chance of causing damage to your systems and applications. This is the case even if penetration testing is possible to cause damage.
5: Why penetration testing is important in today’s context for an organization?
When it comes to a comprehensive cybersecurity plan, penetration testing is an essential component. This provides a proactive approach to discovering and mitigating security vulnerabilities, which in turn protects sensitive data and maintains the integrity of an organization’s information technology infrastructure.
6: What is the importance of a penetration test?
The purpose of a penetration test is to locate potential vulnerabilities that could be exploited by a user with malevolent intent. The purpose of a test known as a pentest is to identify vulnerabilities that could be exploited by a hostile person rather than by a system administrator. Testing for penetration is not a one-time event that can be completed.
7: What is infrastructure penetration testing?
An infrastructure penetration test is a procedure that detects and evaluates security vulnerabilities in an organization’s information technology infrastructure. This includes the identification and evaluation of vulnerabilities in servers, networks, and crucial components.
8: Why is penetration testing important in business?
An organization’s workers may learn how to respond to any kind of break-in from a malicious entity through the use of penetration tests, which is the primary reason why these tests are so important to the organization’s security. A penetration test is a method that can be utilized to determine whether or not the security policies of a company are truly effective.
9: Why is the standard penetration test important?
The standard penetration test also referred to as the “SPT,” was established to provide geotechnical engineering properties for the purpose of foundation design. Within the confines of a borehole, the examination is run. The findings can be utilized to ascertain the relative density of granular soil, as well as its bearing capacity and settling.
10: What is the main goal of penetration testing?
Penetration testing, often known as pen testing, is a type of security exercise in which a cyber-security specialist makes an effort to locate and exploit flaws already present in a computer system. This simulated attack is being carried out with the intention of locating any vulnerabilities in the defences of a system that could be exploited by attackers.
Conclusion
In a nutshell, we would like to say that the importance of penetration testing for today’s digital infrastructure is increasing with each passing day as the number and intensity of cyber attacks are surging, and so is the knowledge of black hat hackers. Hence, to surpass the knowledge parameters of black hat hackers, we need to update ourselves to abreast ourselves in the trajectory of ethical hacking. Thus, with these tactics of enhancing our current knowledge with ethical hacking courses and advanced penetration testing courses, no black hat hacking professional would be able to penetrate into the digital infrastructure and compromise our hard-earned datasets.
All in all, you can join these above-mentioned highlighted courses at the world-class premises of Craw Security, the Best Cybersecurity Training Institute in India, or sign up for a VILT (Virtual Instructor-Led Training) session from a highly experienced and well-qualified training professional with more than 10 years of quality experience. To learn more about the same or anything else, kindly give us a call at our 24X7 hotline number +91-9513805401 to speak with our superb study consultants.