Best Operating Systems for Hacking | Craw Security

Best Operating Systems for Hacking | Craw Security
Best Operating Systems for Hacking: A Deep Dive
The operating system you select can have a big impact on your hacking skills and productivity. An effective platform with pre-installed tools, safety precautions, and a helpful community can be obtained with the correct operating system. Hence, individuals who have a keen wish to work on highly secure and safe operating systems can be a bigger task as hacking professionals have made up their minds to hijack all the datasets in the form of digital assets that common people have.
In this article, we have jotted down all the mainstream and best operating systems for hacking that are utilized by hacking professionals to hack down the diverse IT infrastructures of common people as their potential targets.
Here are a few of the leading OSs:
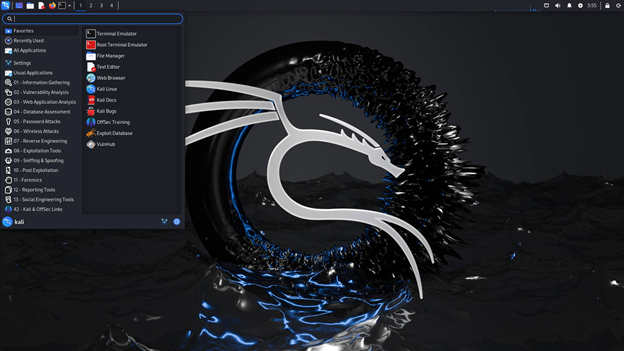
1. Kali Linux
-
- Why it’s popular: As Kali comes with a large number of pre-installed penetration testing tools, it is the operating system that many hackers choose. Kali has everything covered, including vulnerability assessment and network scanning.
- Key features:
-
- More than 1,200 installed tools
- Adaptable desktop setting
- Ability to test without installing via live boot
- strong backing from the community
-
- Ideal for: Kali is an extensive toolkit for a wide range of hacking operations, suitable for both novice and expert hackers.
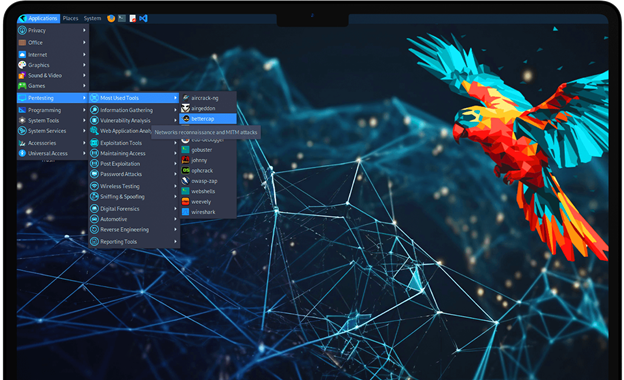
2. Parrot Security OS
-
- Why it’s unique: Parrot is a fantastic option for anyone who is worried about their digital footprint because of its emphasis on security and privacy.
- Key features:
-
- Tools that prioritize anonymity
- Integrated VPN
- Choices for secure boot
- Adaptable desktop settings
-
- Ideal for: Hackers who put anonymity and privacy first when working on their projects.
3. BlackArch Linux
-
- Why it’s powerful: A large collection of hacking tools is available in BlackArch, a distribution that is lightweight and easily customizable.
- Key features:
- More than 2,600 packages for vulnerability assessment
- Continuous updates using the rolling release framework
- Highly customizable
- Ideal for: Sophisticated users that need a strong, versatile platform with a wide range of capabilities.

4. BackBox Linux
-
- Why it’s user-friendly: Because of its user-friendly design, BackBox is appropriate for both novice and seasoned hackers.
- Key features:
- Intuitive interface
- Pre-configured tools
- Live boot option
- Ideal for: Those who desire a user-friendly interface without compromising usefulness.

5. Pentoo Linux
-
- Why it’s fast: Pentoo is a performance- and speed-focused lightweight distribution.
- Key features:
- Minimal footprint
- Fast boot times
- Extensive toolset
- Ideal for: Hackers who put efficiency and quickness first in their work.

6. Fedora Linux
-
- Why it’s versatile: A multipurpose release that can be tailored for hacking purposes is Fedora.
- Key features:
- Large community support
- Regular updates
- Can be customized with hacking tools
- Ideal for: Those who wish to create their own hacking environment from scratch and who like a more flexible operating system.

A Note To Remember:
Although these operating systems offer great hacking platforms, it’s important to use them sensibly and ethically. Before engaging in any hacking activity, make sure you have the appropriate authorization.
Learn Ethical Hacking and Cybersecurity From Scratch
If you have a tendency to learn cybersecurity from scratch to seek a career in this magnificent field, you can start afresh by enrolling in the 1 Year Diploma in Cybersecurity Course by Craw Security, the Best Cybersecurity Training Institute in India. For more information, you can give us a call at our hotline mobile number +91-9513805401 and have a word with our superb educational counselors having many years of quality experience in giving their best piece of advice to the needy students willing to start their educational journey in this trajectory of information security.
In addition to that, Craw Security has the country’s best training experts as instructors with more than 12 years of qualitative work experience in shaping the lives of many students. Moreover, you will even find the best study material to study here at Craw Security which is duly scrutinized by several cybersecurity experts working fine worldwide at diverse levels in distinguished organizations.

















