What is SQL Injection and How It Works?

What is SQL Injection and How It Works?
What Are SQL Queries?
An SQL injection is a cyber attack on the security posture of an IT infrastructure, which includes the insertion or injection of an SQL query through the varied input data from the customer to the app. In addition, SQLi commands are sincerely inserted into a particular data-plane input that affects the carrying out of predefined SQL regimes. After that, a successful SQL injection abuse can nicely read the crucial and sensitive types of information from the datasets and alter database datasets (like insert, update, or vanish), conduct administrative functions on the database, retrieve the content of a database management system file, and even give orders to the operating system in some models.
In case a web application or website utilizes SQLi databases such as Oracle, SQL Server, or MySQL, it is significantly powerless against an SQL injection attack. In addition, hackers utilize SQL injection invasions to approach sensitive business or personally identifiable information (PII) that eventually enhances sensitive information.
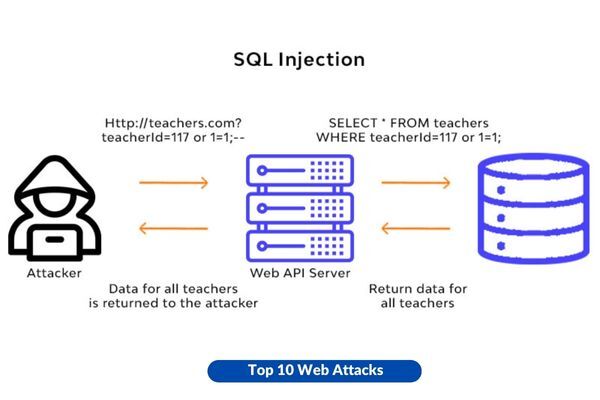
What is an SQL Injection Attack?
As described above and by mainstream cyber security specialists worldwide, SQL Injection Attacks are one of the most widespread among OWASP’s Top 10 Vulnerabilities and one of the ancient application vulnerabilities. In this regard, one latest report lists it as the 3rd most common sensitive vulnerability.
SQL Injection attacks, also known as SQLi attacks, are attacks that modify SQL queries to inject malicious code by exploiting vulnerabilities in applications.
SQL injection attacks that are successful have the capability of modifying database information, gaining access to sensitive data, carrying out administrative actions on the database, and recovering files from the system. At times, attackers can submit commands to the database operating system that lies underneath the database.
Given the severity of the impact that these attacks have, developers must implement techniques that prevent SQL injection. Some examples of these practices include parameterized queries, stored procedures, and stringent input validation.
Types of SQL Injection (SQLi)
SQLi or SQL injection attacks are very common these days to check out the vulnerabilities in an IT infrastructure. In general, there are two types of SQL injection attacks, such as the following:
- Error-based SQL injection
- Blind Based SQL injection
Error Based SQL Injection:
In Error based SQL Injection tactic, an adversary attempts to put some malicious code or query in the input slots and gets a significant error regarding SQL syntax or database.
For instance, SQL syntax errors should be like this:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ‘‘VALUE’’.
This type of particular error message provides info about the database utilized, wherever the syntax error took place in the query. In crisp words, Error based tactic is the most effortless way to find SQL Injection.
Blind SQLI
One can understand that by attempting to attack with the normal SQLi application, a casual error message depicting that the syntax of the SQL query is vastly different or inaccurate. However, Blind SQLi is a general type of SQL injection technique that functions by putting SQLi queries to the datasets blindly and identifying the response based on the modification in the behavior of the response.
In addition, Blind SQLi is generally not familiar with ERROR-based, in which the user puts some SQL queries as opposed to the datasets where the corresponding users get a stated error message. Moreover, the attacker attempts to get info by enquiring about the datasets’ genuine or fake query. Hence, strictly based on the forecasting, we are required to elaborate on the output.
It is further elaborated in 2 types:
- Boolean based SQLI
- Time-based SQLI
How SQL Injection Attacks Work?
SQL injection generally happens when you question a user for input, such as their username/ user ID, and in spite of a name/ ID, the user provides you an SQL statement that you will unawarely run on your datasets.
As a general rule, an SQL Injection attack includes an introduction or injection of an SQL query through the client’s input datasets to the corresponding app. In this regard, SQL injection coding commands are inserted into data-plane input that sincerely affects the execution of pre-described commands of an SQL query. Moreover, this can be answered by several persons asking to know what is SQL injection and how it works.
This type of attack is known as SQL Injection, and it involves putting or “injecting” an SQL query into the program through input data from the client. When an attack is successful, the attacker is able to alter the SQL queries that an application sends to its database.
The following tasks are typically involved in the process:
| Identification of vulnerable inputs | In order to launch an attack, attackers first locate inputs inside the web application that are potential targets for SQL injection. Text fields on a form, parameters in a URL, or any other type of input mechanism could be considered examples of these inputs. |
| Crafting the malicious SQL query | An SQL statement is crafted by the attackers after they have found a susceptible input. This statement is intended to be inserted into the query that is being executed by the application. The purpose of this statement is to modify the initial SQL query in order to carry out operations that the application developers initially did not intend to carry out. |
| Bypassing application security measures | Attackers frequently have to circumvent security features such as input validation or escape special characters in order to complete their attacks. They are able to accomplish this through the utilization of methods such as string concatenation or the utilization of SQL syntax to comment out portions of the initial query. |
| Executing the malicious query | The malicious input provided by the attacker is incorporated into the SQL query that is executed by the program. The modified query has the capability to carry out operations such as the illegal access of data, the deletion of data, and even the modification of the database structure. |
| Extracting or manipulating data | The result of the assault could be the extraction of sensitive information (such as user passwords), the modification of current data, the addition of new data, or even the deletion of substantial chunks of the database. This decision is dependent on the nature of the attack. |
| Exploiting database server vulnerabilities | SQL injections that are more advanced have the potential to exploit vulnerabilities in the database server, which would extend the attack beyond the database and to the server level. Executing commands on the operating system or accessing other areas of the server’s file system are examples of what this can entail. |
This procedure makes use of the dynamic execution of SQL in applications in which user inputs are immediately inserted in SQL statements without the appropriate validation or escaping being performed. It does this by taking advantage of the way SQL queries are designed, frequently in a manner that the creators did not initially foresee.
Impact of a Successful SQL Injection Attack
A successful SQL injection attack can have a number of consequences, including the following:
- Stolen credentials — The SQL injection technique allows attackers to get credentials, after which they can imitate users and use their privileges.
- Unauthorized access to databases — The sensitive information stored on database servers is vulnerable to being accessed by intruders.
- Data alteration — Data that has been accessed can be altered or new information can be added by attackers.
- Data deletion — Attackers have the ability to erase records from databases or drop entire tables.
- Lateral movement — Through the use of operating system rights, attackers are able to get access to database servers. They can then utilize these privileges to gain access to other critical systems.
Real-Life SQL Injection Attack Examples
Over the past 20 years, many SQL injection attacks have targeted large websites, businesses, and social media platforms. Some of these attacks led to serious data breaches. A few notable examples are listed below.
Breaches Enabled by SQL Injection
- GhostShell attack — Using SQL injection, hackers from the Advanced Persistent Threat group Team GhostShell attacked 53 universities, stole and released 36,000 private data associated with students, faculty, and staff, and then published those records.
- Turkish government — SQL injection was utilized by another advanced persistent threat organization known as RedHack collective to break into the Turkish government’s website and erase debt owed to government entities.
- 7-Eleven breach — The SQL injection technique was utilized by a group of cybercriminals in order to gain access to the corporate systems of multiple businesses, most notably the 7-Eleven retail chain, and steal 130 million credit card details.
- HBGary breach — SQL Injection was the method that hackers affiliated with the Anonymous activist organization utilized in order to bring down the website of the IT security company. An attack was carried out as a reaction to the CEO of HBGary making public the fact that he possessed the names of members of the Anonymous organization.
Notable SQL Injection Vulnerabilities
Some notable SQL injection vulnerabilities that have come across the world so far are as follows:
| Tesla vulnerability | The fact that security researchers were able to break into the Tesla website using SQL injection, gain administrative access, and steal customer data was made public in the year 2014. |
| Cisco vulnerability | A vulnerability that allowed for SQL injection was discovered in Cisco Prime License Manager in the year 2018. Attackers were able to get shell access to systems on which the licensing management was implemented as a result of the vulnerability. Cisco System has addressed the security flaw. |
| Fortnite vulnerability | Fortnite is a game that is played online and has more than 350 million users. The year 2019 saw the discovery of an SQL injection vulnerability that could allow malicious actors to gain access to user accounts. A fix was applied to fix the vulnerability. |
SQL Injection Cheat Sheet
This SQL injection cheat sheet includes many primetime examples of helpful syntaxes, which one can sincerely utilize to carry out a bulk of operations that usually arise when executing SQL injection attacks.
One can understand how to apply varied functions on several interfaces like Oracle, Microsoft, PostgreSQL, MySQL, etc. In addition, some of the main functions that a person can perform using SQL injection commands are as follows:
- String concatenation
- Substring
- Comments
- Database version
- Database contents
- Conditional errors
- Batched (or stacked) queries
- Time delays
- Conditional time delays
- DNS lookup
- DNS lookup with data exfiltration
SQL Injection or 1=1
As a general rule, SQL Injection Based on 1=1 is forever genuine.
Look at the example beneath once.
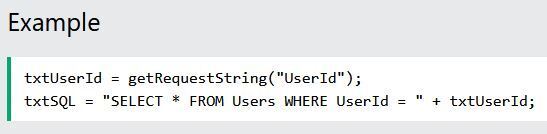
The prime objective of the given code is to establish an SQL query to choose a user with a given user id.
However, if there is none to secure a user from going “wrong” input, then the same user can go in some “smart” input like this:
UserId: 105 or 1 = 1
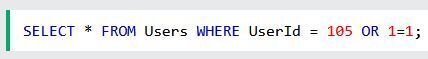
Ahead, the SQL statement would be something like the following:
In this regard, the SQL query above is truly legitimate and would definitely give back ALL rows from the corresponding “Users” table since OR 1 = 1 is forever genuine.
Now, let’s come to this verdict and ask a couple of questions!
Does the example above seem threatening? What would be done if the “Users” table possessed names and passwords?
As a result, the SQL query above would be something like the following:
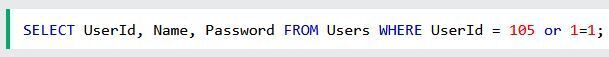
In a nutshell, an adversary might be able to possess some decent access to all the user names and passwords in datasets by merely inputting 105 OR 1=1 into the given slot.
Frequently Asked Questions
1: What is SQL Injection OWASP?
In general, an SQL injection attack is the sub-part of “Injection,” which is a vulnerability from the OWASP Top 10 Vulnerabilities system, as described on its official website.
2: What are the 3 major SQL operations?
The 3 major SQL Operations or commands are described as follows:
- DDL (Data Definition Language),
- DML (Data Manipulation Language), and
- TCL (Transaction Control Language).
3: What are 5 types of SQL injection?
The main types of SQL injections are as follows:
- Error Based SQL injection
- Blind Based SQL injection
- Boolean based SQLI
- Time-based SQLI
4: What is an example of SQL injection?
The prime examples of SQL injection conclude calls to the operating system via a system call, the utilization of external programs through shell commands, or calls to the backend datasets utilizing SQL (i.e., SQL injection).
5: What does SQL injection means?
SQL injection is basically a string of code injection technique that is sincerely constructed to delete your databases. In this regard, SQL injection is one of the most common web hacking tactics. Moreover, SQL injection is the prime placement of malicious code in SQL queries through web page input.
6: Why do hackers use SQL injection?
SQLi or SQL injection attacks allow the working adversaries to spoof identity, interfere with the current datasets, causing rejection concerns, like eliminating transactions or altering balances, permitting the entire revelation of all data on the system, vanishing the entire data, or making it otherwise inaccessible, and become managers of the database server.
7: What are 3 methods SQL injection can be done by?
The SQL injections generally come under the purview of 3 methods, such as the following:
- In-band SQLi (Classic),
- Inferential SQLi (Blind), and
- Out-of-band SQLi.
8: What are the 3 types of SQL commands?
The main 3 types of SQL Commands are as follows:
- DDL (Data Definition Language) commands,
- DML (Data Manipulation Language) commands, and
- DCL (Data Control Language) commands.
9: What are the 4 parts of SQL?
The prime 4 parts of SQL query comprise the following:
- Data Query,
- Data Manipulation (insert, update, and delete),
- Data Definition (schema creation and modification), and
- Data Access Control.
Conclusion
To wrap up, we tried to provide the best knowledge we have related to SQL Injections by every means. In this regard, if anyone wishes to know more about the same topic, then the same person can opt for the world-class 1 Year Diploma in Cyber Security Course by Craw Security, the Best Cyber Security Institute in India, remarkably present in the NCT of Delhi from the past 10+ years offering international standard cyber security education to the interested candidates.
In addition to this, Craw Security’s courses are highly accredited to FutureSkills Prime, a MeitY — NASSCOM, Digital Skilling Initiative.
















