Best Cyber Forensic Investigation Course in Delhi
June 12, 2021 2025-03-30 11:58Best Cyber Forensic Investigation Course in Delhi

Best Certified Hacking Forensics Investigation Course in Delhi | CHFI v11
Bestseller
1900+ Student Reviews
Learn the most advanced Eccouncil Certified Hacking Forensics Investigation Course in Delhi, which is constantly updated to reflect the latest advancements in digital devices, through the dedicated learning modules of the CHFI v11 Course in Delhi. The EC-Council CHFI Computer Forensics Investigator Course validates the learner’s skills and expertise that have been acquired through professional work methodologies or sincere CHFI Training. This course specifically addresses the identification of intruders’ footprints while working on a corresponding network within an organization. Take advantage of this exceptional CHFI Certification by enrolling today!
- Course Duration : 40 Hours
- Language : Hindi | English
- Course Delivery : Online | offline
Book a Trial Demo Class
Training Available 24*7 Call at 9513805401
What will you learn in the Best CHFI v11 Course in Delhi?
Regardless of whether you aspire to serve the nation as a Computer Forensics Analyst or Digital Forensics Examiner, you will require the most advanced or the best Cyber Forensics Investigation Course in Delhi to significantly advance your career as a Computer Forensics Specialist.
Enrolling in the Eccouncil Certified Hacking Forensics Investigator Course in Delhi will undoubtedly help students acquire valuable information regarding the premium EC Council Forensics Course. This information will be essential for conducting comprehensive investigations using innovative digital forensics technologies for numerous digital forensics companies in the near future.
In the distinguished field of Digital Forensics and Cyber Investigation, a variety of new instruments are being developed on a daily basis to facilitate the execution of numerous computer hacking investigations. The investigation techniques employed by police, government, and corporate entities worldwide are the subject of the Cyber Forensics Course in Delhi. Upon completion of the Computer Hacking Forensics Investigator Course, there are numerous avenues available for identifying the data that resides within a computer system. It also instructs on the recovery of file information that has been deleted, encrypted, or mutilated.
Book a Trial Demo Class
Training Available 24*7 Call at +91 9513805401

Certified Hacking Forensics Investigation Content
Module 01: Computer Forensics in Today’s World
Module 02: Computer Forensics Investigation Process
Module 03: Understanding Hard Disks and File Systems
Module 04: Data Acquisition and Duplication
Module 05: Defeating Anti-Forensics Techniques
Module 06: Windows Forensics
Module 07: Linux and Mac Forensics
Module 08: Network Forensics
Module 09: Investigating Web Attacks
Module 10: Dark Web Forensics
Module 11: Database Forensics
Module 12: Cloud Forensics
Module 13: Investigating Email Crimes
Module 14: Malware Forensics
Module 15: Mobile Forensics
Module 16: IoT Forensics
Talk to Our Course Advisor
Benefits of Computer Forensics Investigator Course
After the conclusion of the Computer Forensics Course in Delhi, you will be capable of resolving cases or issues that pertain to cybercrimes, including encryption, data recovery, damaged or deleted data, case management, and investigative techniques. To be more precise, the Cyber Forensics Investigation Course in Delhi includes a variety of cyber forensics programs that will assist individuals in conducting a seamless investigation.
The tools and techniques taught in this Best Cyber Forensics Investigation course in Delhi are instrumental in the resolution of a variety of cyber-related offenses, including the theft of trade secrets, the breach of intellectual property rights, and the misuse of confidential data. The Digital Forensics Training introduces a variety of methods and techniques that a potential investigator can employ to quickly resolve real-time cases during the investigation.
Course Highlights
- How to Investigating E-mail Crimes
- Understanding Hard Disks and File Systems
- Data Acquisition and Duplication
- Verification of the copied data
- Deleted files recovery
- Malware Forensics
- Operating System Forensics
- Copying the hard drive of the system under investigation
- Performing keyword search
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class
One can also opt for the prerecorded video sessions available at any point of time from any particular location.

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
EC-Council CHFI v11 Course Description
Upon the successful completion of the genuine CHFI v11 Training in Delhi, you will possess the skills necessary to become a professional Computer Forensics Investigator who can effectively investigate cases using a variety of tools and tactics that were acquired during the EC Council CHFI Training.
Your position may be referred to as a Computer Forensics Examiner, Digital Forensics Investigator, Cyber Forensics Detective, Computer Forensics Analyst, or Computer Forensics Specialist, depending on the organization for which you are employed. These titles are used to refer to Cyber Forensics Investigators in various agencies.
Subsequently, your daily official obligations will remain consistent; only the title of your position may differ. CHFI v11 Syllabus is more authentic and accredited due to the fact that the course curriculum is composed of basic to advanced fundamentals that have been accumulated from industry-experienced experts from a variety of Digital Forensics Companies worldwide.
Craw Security Delhi’s Saket and Laxmi Nagar institutions offer a world-class teaching faculty and mentorship group, making it possible for anyone with a genuine interest in becoming a Computer Forensics Specialist in a highly reputable and recognized Digital Forensics Company to enroll in this magnificent EC Council CHFI Certification at the earliest.
Initially, Craw Security provides a curriculum of the highest quality that has been verified by a multitude of domain experts from numerous reputable organizations in the field.
The number of cyber-related crimes has resulted in a significant increase in the demand for trained individuals in the field of computer forensics. Since the inception of computers and the internet in the past few decades, digital forensics, also referred to as cyber forensics or computer forensics, has been in high demand.
Craw Cyber Security Institution in Saket and Laxmi Nagar locations in Delhi NCR delivers our learners with comprehensive information on the different methods of gathering, safeguarding, identifying, finding, and submitting evidence digitally during the training of the EC Council CHFI Certified Hacking Forensic Investigator Course.
It is a process that involves the utilization of all the aforementioned techniques as digital evidence that can be employed in the investigation of cybercrime. The Craw Cyber Security Institute is staffed by a team of professional and well-educated CHFI Certification Course instructors who possess the necessary experience, resources, and knowledge to provide comprehensive training in the field of cyber forensics for the Best Cyber Forensics Investigation Course in Delhi. Our instructors possess an abundance of experience, having served in the military, private, and government sectors.
The majority of Digital Forensics and Cyber Investigation aspirants have conducted daily searches on various search engines to ascertain the cost and difficulty of the CHFI Certification, which is a remarkable computer forensics course. More individuals are becoming interested in this course to advance their careers in this remarkable field since the most recent update, or CHFI v11 Release Date, on May 1, 2021.
Consequently, the Craw Cyber Security Institution at Saket and Laxmi Nagar offer this exceptional Cyber Forensics Course Certification and Training at a budget-friendly price. Additionally, individuals may contact us at our toll-free hotline number, +91-9513805401, to apply for financial aid and receive assistance from our counselors.
- How to Investigating E-mail Crimes
- Understanding Hard Disks and File Systems
- Data Acquisition and Duplication
- Verification of the copied data
- Deleted files recovery
- Malware Forensics
- Operating System Forensics
- Copying the hard drive of the system under investigation
- Performing keyword search
Craw Security's Students Awarded











Cyber Forensics Investigation Training Course
- Blended learning delivery model (instructor-led options)
- Teaching style modified according to the student’s issues
- Develops important personality and career-building skills
- Group Discussions
- 24×7 learner assistance and support
- Weekdays / Weekend Classes
Related Cyber Security Course
What People Are Saying About Craw Security
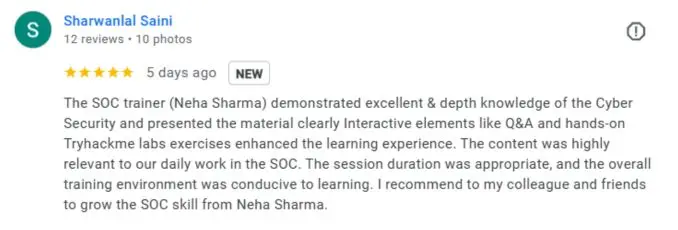
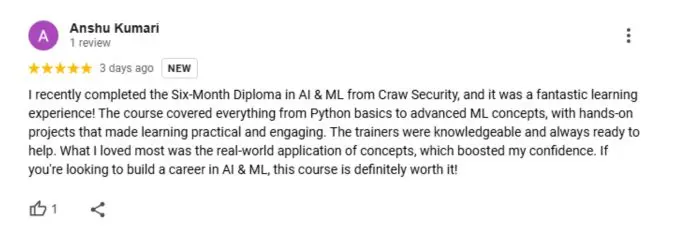
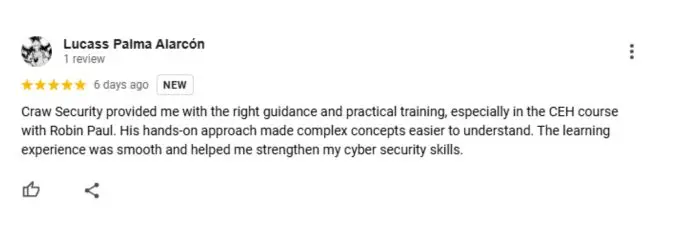
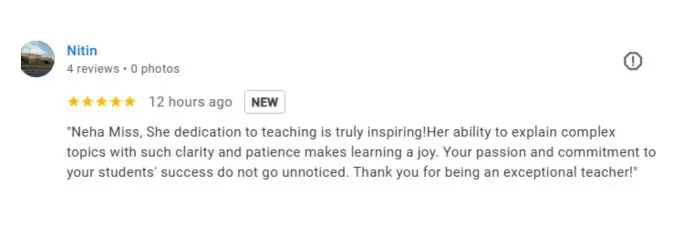
Google Review (1900+) ★★★★★
Frequently Asked Questions
About CHFI – Cyber Forensics Investigation course in Delhi
A skillset of procedures known as cyber forensics is employed to conduct a variety of investigations involving encrypted, damaged, or tampered IoT devices, as well as e-copies of prestigious data files. In the present day, the majority of data is stored on servers. Consequently, cyber forensics would be employed to acquire the relevant data to serve as actual evidence in a court of law.
The Best Cyber Forensics Investigation Course in Delhi can be sincerely pursued at the Saket and Laxmi Nagar locations of Craw Cyber Security Institutions in Delhi.
The EC Council Certified Hacker Forensics Investigator Certification, also known as CHFI Certification, is a CHFI v11 Certification course that describes the industry insights of the Computer Forensics Course. This course is used to fulfill a variety of cyber investigation purposes in real-time forensics cases crackdown.
In this context, Craw Security, which is the Best Cyber Forensics Investigation Training Institute in India, provides you with the Best CHFI v11 Certification Training in Delhi NCR. To know more about the same or anything else, give us a call at our hotline mobile number +91-9513805401.
A typical Cyber Forensics Analyst typically extracts the dataset that is concealed in an encrypted format within a variety of platforms, including SMS messages, social media chats, customer details, banking credentials (such as user IDs and passwords), and other helpful details kept on IoT devices and additional vital software. In general, a Digital Forensics Examiner conducts investigations into criminal activities and acquires critical cyber evidence.
In certain instances, these Cyber Security Specialists assist in the research and investigation of crimes by recovering information that has been concealed, encrypted, or deleted. They also ensure the integrity of data by adhering to a chain of custody that guarantees its admissibility in court.
The CHFI Certification and Training course is classified as a mid-level course in the demanding courses index, as it is less challenging than the medical and engineering course streams but more difficult than the numerous course streams related to Arts and Humanities.
One can genuinely enroll in the Best Cyber Forensics Investigation Course in Delhi at Craw Security’s duly accredited institutions in Saket and Laxmi Nagar. The highly experienced group of teachers and mentors at these institutions can provide user-friendly training that will enable anyone to pass the challenging CHFI Exam with flying colors.
A critical component of network security is the utilization of cyber forensics to safeguard an organization’s database. This feature ensures the network infrastructure of an enterprise maintains its integrity and longevity. For instance, understanding the legal and technical aspects of computer forensics in order to ensure information security can help you capture critical data in the event of a network compromise and will provide you with the necessary concrete evidence to prosecute your case if the intruder responsible is apprehended.
In general, a cybercrime investigator investigates a variety of crimes, including the recovery of a file system on a computer that may have been compromised or damaged by an individual or organization, as well as the investigation of them for various unlawful activities. In essence, they serve as the cyber assistance of a variety of investigative agencies, including government and private organizations, that conduct forensics work to recover data that may have been concealed, tampered with, destroyed, or deleted. This information is intended to provide concrete evidence that can be used in court.
The primary operation of forensic investigation in cyber security is the extraction of deleted, hidden, tampered, or damaged files from a variety of IoT devices or AI protocols to create a genuine piece of proof that may be admissible in a criminal investigation in a court of law.
Upon completion of the Best Cyber Forensics Investigation Course in Delhi, there are numerous lucrative forensic positions available in the field. The following is a list of some of the most renowned and lucrative forensic positions:
- Forensic Medical Examiner
- Forensic Engineer
- Forensic Accountant
- Crime Scene Investigator
- Crime Laboratory Analyst, and etc.
Certainly, it is a beneficial course and a pleasant genre to begin your career in, as few individuals have a particular interest in this field and fewer candidates are interested in pursuing it to this extent, as it requires a significant amount of cerebral strain to complete daily official tasks.
It is a critical aspect of law enforcement agencies in the current era of internet-based devices and can be a lucrative and rewarding career path for those who aspire to it.
It is essentially a Digital Forensics and Cyber Investigation Training program that is provided by numerous reputable institutions worldwide. This program is specifically designed to cultivate a greater number of Cyber Forensics Specialists for law enforcement agencies in both the public and private sectors of numerous countries worldwide.
This course provides an aspirant with a comprehensive understanding of the cracking procedures associated with cybercrimes, as well as an in-depth understanding of the renowned software and techniques that are outlined in the curriculum of the Best Cyber Forensics Investigation Course in Delhi, which is conducted by Craw Cyber Security Institutes at the Saket and Laxmi Nagar locations.








