What is Session Hijacking and How Does It Works? [2025]

What is Session Hijacking and How Does It Works? [2025]
As the term suggests, Session Hijacking, which is also famous as the name TCP session hijacking, is a process of seizing a web user session by stealthily acquiring the session ID and disguising it as the legitimate one. However, once the user’s session ID gets assessed, the hijacker or the malicious threat actor can disguise oneself as the authentic user and can perform any particular task that the original person was authorized to do.
Moreover, there are many byproducts duly available of this type of attack in the cyber world, such as the capability to obtain access to a server in the absence of authentication. In addition, as soon as the attacker takes over a particular session, the same will not think about establishing a fair connection with the said server as long as the communication period stays online. Hence, the hijacker works with the same server access as the hijacked user because the user had already ascertained the server before the attack happened.
What is a session?
Here, we should also understand the basic explanation of a session. In this statement, HTTP is a stateless protocol, so various app developers could develop a measure to monitor the state of several junctions from the same user, despite asking the user to authorize upon every click in a preferred web application. Moreover, talking about a ‘session’ is a series of communications between two interacting endpoints that are established during the course of a unique connection. In addition, a user logs into an app, and a particular session is established on the server to keep up the condition of additional requests conceiving from the exact user.
Now, we would also like to tell you about the applications that use sessions to stock protocols that are suitable to the user. In addition, the corresponding session is maintained active on the server as long as the user is stayed on as logged in on the particular system. However, the same session goes ends when the same user logs out of the system after a predefined period of time by being inactive, and once the session is destroyed, the corresponding user’s database would also be terminated from the allotted memory space.
In general terms, a session ID is basically an identification string (generally a lengthy, random, alpha-numeric code) that is fully communicated between the client and the server. In addition, Session IDs are typically stocked in cookies, URLs, and secret slots of web pages.
Different ways of session hijacking:
In today’s technological world, there are many dedicated methods by which a person can do Session Hijacking or take over a particular session on a system. Some of the prominent methodologies are described below:
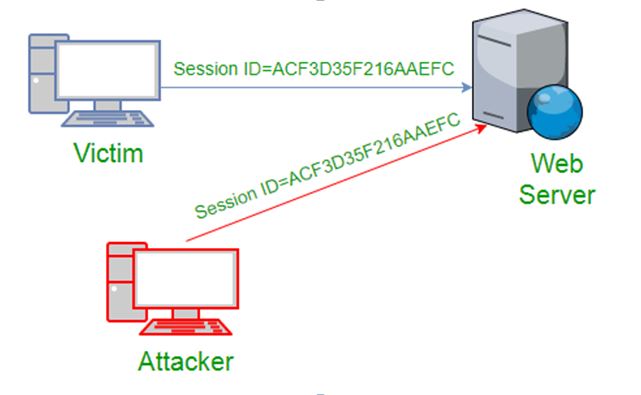
- Using Packet Sniffers
As shown in the above image, the corresponding attack seizes the target’s session ID and password to have access to the server by utilizing some packet sniffers.
- Cross-Site Scripting (XSS Attack)
In this methodology, a particular hijacker can also seize the target’s Session ID with the usage of an XSS attack through javascript commands. In addition, if the same attacker transmits a specialized crafted link to the target with the threat possessing JavaScript commands while the target clicks on a particular link, the JavaScript will certainly execute and accomplish the guidelines made by the corresponding hijacker.
- IP Spoofing
The acronym Spoofing elaborates on a technique of pretending to be somebody else. This technique is just to assess the illicit access to the system with an IP address of a legitimate host that is fully authenticated or trusted by the host server. While employing this particular form of technique, the attacker has to extract the IP address of the target and deploy one’s own packets spoofed with the IP address of the client into the TCP session, just to befool the server that is interacting with the target. I.e. the authorized host.
- Blind Attack
In this process of Blind Attack, if the hijacker is not capable of sniffing packets and is able to predict the right sequence number anticipated by the server, a series of brute force attacks assortments of series number can be attempted.
- Mitigation
Just to safeguard a network from session hijacking, a particular defender has to deploy both security procedures at the application level and network level. In addition, network-level attack seizures can be safeguarded by encrypting the packets so that the attacker cannot decrypt the packet headers to extract any info that will certainly aid in spoofing. Moreover, this ciphering can be offered by utilizing parameters like IPSEC, SSL, SSH, etc.
Particularly in the transport mode, the info transmitted in the packed is ciphered when in Tunnel Mode, where both packet headers and datasets are encrypted; hence, it is more restrictive.
In a nutshell, we can say that session hijacking is a pretty hazardous threat to Networks and Web applications on the web as most systems are highly vulnerable to it.
How does session hijacking work?
The highly famous parameters for executing a session hijacking are:
- Session Sniffing,
- Predictable Session Token ID,
- Man in the Browser,
- Session side jacking, and
- Session Fixation.
Now, we will elaborate on the above-mentioned technologies one by one in the following lines:
- Session Sniffing
It is the most famous technique among all utilized alongside application-layer session seizure. In addition, the corresponding hijacker utilizes a sniffer like Wireshark, or a proxy, like OWASP Zed, to seize network traffic comprising the session ID between a website and a client. However, once the hijackers seize this particular value, they could nicely utilize this valid toke to extract unauthorized access.
- Predictable Sessions Token ID
Several web servers utilize a customized algorithm or some preset pattern to develop session IDs. In addition, the more the predictability of a session token, the more fragile it will be, and the chances of assumption will be feasible. However, if the corresponding hijacker can seize numerous IDs and study the pattern, one might be capable of assuming a proper session ID.
- Man-in-the-Browser Attack
This particular form of attack is pretty similar to a man-in-the-middle attack, however, the hijacker must contaminate the target’s system with Trojan malware. Once the target is compelled into installing the Trojan malware onto one’s system by using various techniques, the malware longs for the target to surf a malicious site as a mission. Meanwhile, the man-in-the-browser malware can make primary alterations in the transaction info secretly, which can also lead to the creation of some additional transactions out of the knowledge of the target.
- Session Side Jacking
The famous to famous cyber criminals can utilize packet sniffing techniques to control a target’s network traffic and block session cookies following the user has confirmed on the server. However, if the TLS ciphering is only utilized for login pages and not for the complete session, cybercriminals can nicely seize the session as worse as act as the user within the targeted web application.
- Session Fixation Attacks
This particular tactic pockets a proper session ID that has yet to be authorized. Further, the hijacker attempts to puzzle the user into authenticating with this ID in order to get proper access to the victim’s system. In addition, the session fixation examines a drawback in the manner the web app controls a session ID. Moreover, the 3 common variations that exist are as follows:
- Session tokens are hidden in a URL argument,
- Session tokens are hidden in a form field, and
- Session tokens are hidden in a session cookie.
Subsequently, session seizure attacks are generally waged against busy networks with a great number of active communication sessions. In addition, the high network usage not only offers the hijacker a vast number of sessions to expose, but it could also offer the hijacker a cloak of security due to a vast number of online sessions on the server.
What Do Attackers Gain from Session Hijacking?
It is a sure-shot fact, as the name suggests, that when a malicious threat actor hijacks a session, the one is virtually able to do anything on the compromised system that a legitimate user is allowed to access during the active session till it is not get terminated. Moreover, the most severe examples comprise transferring money from the user’s bank account using the already stored banking on the banking sites, purchasing multiple cheap or costly products from web stores like Amazon, and Flipkart, accessing personally identifiable information (PII) for identity theft, and even robbing datasets from organizational systems for personal illicit usage.
How to prevent session hijacking attacks?
It is of utmost importance to stop such heinous attacks from taking place as the attacker can genuinely steal and reuse stolen session datasets such as identifiers or some other sensitive cookie values whenever they are stocked or sent openly or insecurely. However, when offering about 100% security can be a greater challenge, encryption is the main defense that we could employ.
In addition, when a user authenticates, SSL and a protected cookie should be made compulsory. Further, when authorized users surf one or more protected pages, they should be educated to use HTTPS websites in spite of HTTP.
In the same vein, IDS (Intrusion Detection Systems) and IPS (Intrusion Prevention Systems) technologies can also be employed to intercept such heinous session hijacking attacks to safeguard your networks.
Frequently Asked Questions
About Session Hijacking
1: What is a session hijacking attack?
The particular types of attacks utilized by many malicious threat actors to steal the database on the victim’s computer system or do some illegal activities on the compromised system with the personal interest that directly or indirectly cost something to the original user. E.g. Session Sniffing, Cross Site Scripting, etc.
2: What are the side effects of session hijacking?
If a person is victimized by session hijacking, the same person can face monetary losses, some identity theft issues, any other personal database loss, or any other losses as per the personal interest of the hijacker. Hence, it is highly recommended to avoid clicking on any suspicious link in a doubtful email unless you can verify the user as a legitimate one.
3: How does application-layer Session Hijacking work?
A connection has been established between the client and the attacker, and another connection is established between the attacker & server. When the attacker becomes the man-in-the-middle, all the traffic will be going under his commands. Therefore, he would be able to get the session IDs with ease.
4: What is session side-jacking and session sniffing?
Under a session side-jacking, an adversary would be on the attack while the victim is trying to log in to the system. There, in session sniffing, the cybercriminal will directly log in to the victim’s a/c via stolen credentials while the victim is logged off.
Wrapping Up
So far, we have tried to elaborate on every single possible aspect by which a malicious threat actor can overtake your system credentials and hijack the corresponding system to one’s own malicious intent till the system is online. In addition, this could be very hazardous for the original user as one will certainly be unaware of the compromise of one’s system by a malicious threat actor or system hijacker.
















