A Comprehensive Threat Protection Solution
Companies now have to deal with increasingly complicated attacks that could jeopardize their data, systems, and reputation in the rapidly evolving field of cybersecurity. To protect their assets from a range of dangers, firms must employ cutting-edge security solutions.
As a result, Craw Security ShieldXDR is a unique product from the company, which is a top supplier of cybersecurity services and training that offers complete threat protection to companies of all sizes.
What is Shield XDR?— With Artificial Intelligence, Machine Learning and Analytics
ShieldXDR, which comes from the House of Craw Security, is a powerful security solution that quickly detects and gets rid of complex threats by utilizing state-of-the-art technologies like artificial intelligence (AI), machine learning (ML), and behavioral analytics.
By combining cloud, network, and endpoint security into one platform, it offers a comprehensive approach to threat identification and reaction. Businesses can respond quickly to any security event that may occur at any time from any remote hacker sitting anywhere in the world, since Shield XDR provides monitoring and notifications 24X7.
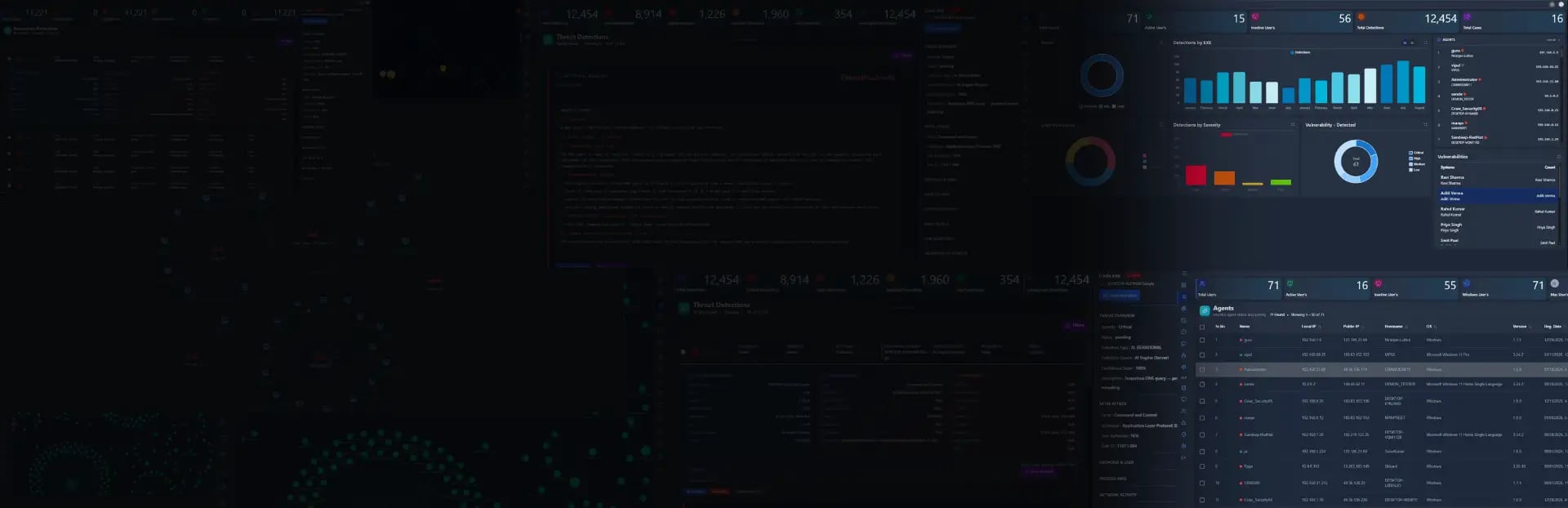
Shield XDR simplifies security operations with a unified dashboard that correlates data from multiple sources, enabling faster threat investigation and informed decision-making.
Its automated threat hunting capabilities and intelligent orchestration reduce manual workload, allowing security teams to focus on critical incidents while maintaining complete visibility across their entire infrastructure.
Malicious Activity Detection
Real-time Threat Identification
Shield XDR's advanced detection system identifies and analyzes malicious activities in real-time across your entire network infrastructure.
Key Features:
- Real-time malware detection and analysis
- Behavioral pattern recognition for suspicious activities
- Automated threat classification and severity assessment
- Instant alert generation with detailed forensic data
- Machine learning-powered threat intelligence
Performance Metrics:

Hash Analysis & Verification
File Integrity and Threat Intelligence
Comprehensive hash analysis system that verifies file integrity and cross-references with global threat intelligence databases.
Key Features:
- MD5, SHA-1, and SHA-256 hash verification
- Integration with multiple threat intelligence feeds
- Automatic malware family identification
- File reputation scoring and analysis
- Historical hash database for forensic analysis
Performance Metrics:

Detection Activity Monitoring
Continuous Security Surveillance
Monitor all detection activities across your network with detailed logs and real-time activity feeds.
Key Features:
- Live activity monitoring dashboard
- Detailed detection event logging
- Historical activity analysis and trends
- Customizable alert thresholds
- Activity correlation and pattern analysis
Performance Metrics:

Network Detection Analysis
Network Traffic and Threat Analysis
Advanced network detection capabilities that analyze traffic patterns and identify network-based threats.
Key Features:
- Deep packet inspection and analysis
- Network anomaly detection
- Traffic pattern analysis and baseline establishment
- Intrusion detection and prevention
- Network forensics and investigation tools
Performance Metrics:

Shield XDR Key Features
Shield XDR's cutting-edge endpoint security technology guards against malware, ransomware, and other contemporary threats that could compromise endpoints. The use of AI and ML algorithms enables real-time detection and reaction to zero-day attacks.

Advanced Threat Detection
- AI-powered analysis for real-time threat recognition
- Detects malware, ransomware, and zero-day exploits
- Adapts continuously to evolving threat landscapes

Real-Time Monitoring
- 24/7 monitoring of endpoints and traffic
- Instant alerts for any suspicious activity
- Cloud-based dashboard for centralized visibility

Incident Reporting & Analytics
- Detailed post-incident analysis reports
- Trend analytics for threat pattern recognition
- Customizable dashboards for executive summaries
Global Threat Activity View
In Shield XDR (Extended Detection and Response), the globe visualization provides a real-time interactive map of global network activity. Each connection arc illustrates live traffic flow or potential threats between geographic regions.
Real-time visualization of global network activity and threats.
Each arc represents live data flow between source and destination.
Helps detect suspicious IP connections and threat origin points.
Current View:
India Network Map - Real-time threat connections across Indian cities

Advanced Security Capabilities
Increased Visibility and Efficiency
XDR systems provide a single view of security data across servers, networks, endpoints, and cloud environments. This improved visibility allows security professionals to detect threats faster, eliminate blind spots, and respond more skillfully by connecting events from several sources.
Alert Management
Effective alert management in XDR systems helps security analysts avoid being overwhelmed with false positives and instead warns them of actual risks. Advanced filtering, prioritization, and aggregation tools expedite the alert review process.
Automated Tasks
Automation in XDR simplifies repetitive security tasks like threat hunting, alert triage, and early incident response. This reduces the manual workload, expedites response times, and ensures consistency in security operations.
An integrated response across multiple security tools
XDR systems coordinate activities across several security products (firewalls, EDRs, SIEMs, cloud security solutions, etc.) to ensure a coordinated response. This integration streamlines workflows and allows for rapid containment.
AI-Based Detection
Artificial intelligence and machine learning in XDR systems enhance threat detection by identifying advanced persistent threats (APTs), aberrant patterns, and zero-day attacks that traditional signature-based methods may miss.
Dark Web Monitoring
XDR solutions monitor discussions on dark web sites on targeted attacks, compromised credentials, and leaked data. By identifying such activity early on, organizations can take preventive action before a breach impacts them.
IP Tracking Details
The "IP Traffic " interface of an XDR (Extended Detection and Response) architecture shows network traffic patterns according to IP addresses. It provides information on the global distribution of connections on the network and illuminates the initial sources and destinations of network traffic.
Geographic Visualization
An illustration of a world map showing the locations of the nations or territories that are crucial to network traffic. The distribution of IP addresses used in network connections worldwide can be seen with this visualization.
Traffic Volume
The amount of network traffic between IP addresses is shown by the map's links thickness or magnitude. Thinner lines indicate lower traffic levels, whereas thicker lines indicate higher traffic levels.
IP Address Connections
Lines or arrows are used to visually represent links between several IP addresses. In addition to other network-related operations, these connections may entail server-to-server and client-server communications.

Background Processes
The dashboard offers insights into key system processes that support secure and efficient operation.
- Process Status: View which background processes are active or facing issues.
- Process Logs: Access logs showing actions, timestamps, and error traces.
- Performance Metrics: Monitor CPU, memory, and task efficiency.
Agent Port Details
Many port files can provide useful information for monitoring and enhancing cybersecurity. Ports are used as communication endpoints in many network protocols. Potential security flaws, hostile behavior, and unauthorized access attempts can all be identified by security experts.
SMTP Logs
For email security, SMTP (Simple Mail Transfer Protocol) logs are essential. They might assist in spotting questionable email activity that might point to a compromised account, such as spam and phishing efforts.
HTTP/ HTTPS Logs
Web traffic can be examined using HTTP (Hypertext Transfer Protocol) and HTTPS (HTTP Secure) records. These log files may expose serious security flaws like SQL injection, web application attacks, cross-site scripting, and odd file uploads.
TCP and UDP Logs
Logs used to identify anomalous network activity, such as port scanning, brute-force attacks, and unauthorized service access, contain two crucial transportation layer systems: Transmission Control Protocol and User Datagram Protocol connection data.

Additional Key Features
Real-Time Threat Intelligence Feeds
XDR systems ingest live threat intelligence feeds to deliver up-to-date information on malicious IPs, domains, indicators of compromise (IOCs), and new threats. This enables proactive defense and faster identification of potential threats.
Asset Management
XDR helps companies manage vulnerabilities, monitor assets, and respond quickly to events that affect specific resources by maintaining an up-to-date inventory of all endpoints, servers, and devices.
Local Data Breach Monitoring
By identifying and reporting any unauthorized access or exfiltration of sensitive data within the organization, the system enables a prompt response to manage and address breaches at the earliest stage.
Incidence Response
XDR's end-to-end incident management capabilities, including playbook-driven reaction, automated investigation, evidence collection, and comprehensive reporting, enable quick and well-organized handling of security incidents.
Built-in DLP Protection
XDR solutions usually include DLP features to detect and stop unauthorized transmission of sensitive data via email, web uploads, portable media, or cloud services in order to protect private information.
USB/ Pen Drive Monitoring
Built-in device control features assist in preventing virus introduction, undesired data transfers, and data leakage through detachable devices by monitoring and restricting USB and other external media.
Screenshot Monitoring
XDR platforms can identify or prevent unauthorized screenshots, safeguard confidential on-screen information, and prevent accidental or intentional data exfiltration.
Full Assistance in Compliance
ISO Certifications
XDR platforms can help businesses establish and maintain the rules required for ISO certification by centralizing security monitoring, reporting, and incident response capabilities.
GDPR Compliance
With capabilities like data access monitoring, breach detection, and thorough audit logs, XDR solutions meet GDPR requirements for protecting personal data and disclosing breaches within the allotted period.
NIST Framework Compliance
XDR solutions assist businesses in adhering to NIST cybersecurity rules by offering capabilities for continuous monitoring, threat detection, incident response, and evidence gathering.
Event Logs Table
You can take a number of useful steps with the help of this incredibly helpful Shield XDR software that will greatly increase the security of every device in your company's IT infrastructure.
Correlate Events
XDR systems employ enhanced correlation techniques to find patterns and connections among various events. This makes it simpler to identify possible dangers or questionable behavior, such as various systems or network elements.
Collect Data
XDR systems gather and aggregate data from your network's endpoints, servers, cloud infrastructure, and network hardware. Examples of this data include network traffic, events, logs, and endpoint telemetry.
Normalize Data
The collected data is then standardized to preserve a consistent format inside an organization. Because different sources may have different log structures and data representations, this step is crucial.
Why Choose Shield XDR from Craw Security?
Businesses should adopt Shield XDR as their primary security solution for several reasons. First off, ShieldXDR offers comprehensive attack prevention by combining network security, cloud security, and endpoint high security into a single system.
This makes understanding easier and provides a thorough overview of the company's safety position. Furthermore, Shield XDR uses state-of-the-art technologies like artificial intelligence (AI), machine learning (ML), and behavioral data analysis to swiftly identify and eradicate complicated threats.
Businesses ensure security from the latest threats by doing this. Finally, Shield XDR provides 24X7 monitoring and alerting so that companies can respond quickly to any security incident. In this case, it minimizes the impact of a security breach while allowing businesses to continue operating.
See Shield XDR in action with a personalized demo
threat detection and response platform can protect your business from cyber threats.
What's included:
Our team will get back to you within 24 hours