What is DLP and Why It Matters?
Data, from financial records and consumer information to internal plans and intellectual property, is an organization's most important asset in the digital age. A crucial cybersecurity tactic called Data Loss Prevention (DLP) is intended to identify, track, and stop unwanted access, exchange, or leakage of private information throughout an organization's infrastructure.
Our DLP services, which are tailored to help businesses stay compliant, prevent breaches, and preserve confidence, are offered by India's top VAPT (Vulnerability Assessment and Penetration Testing) service provider.
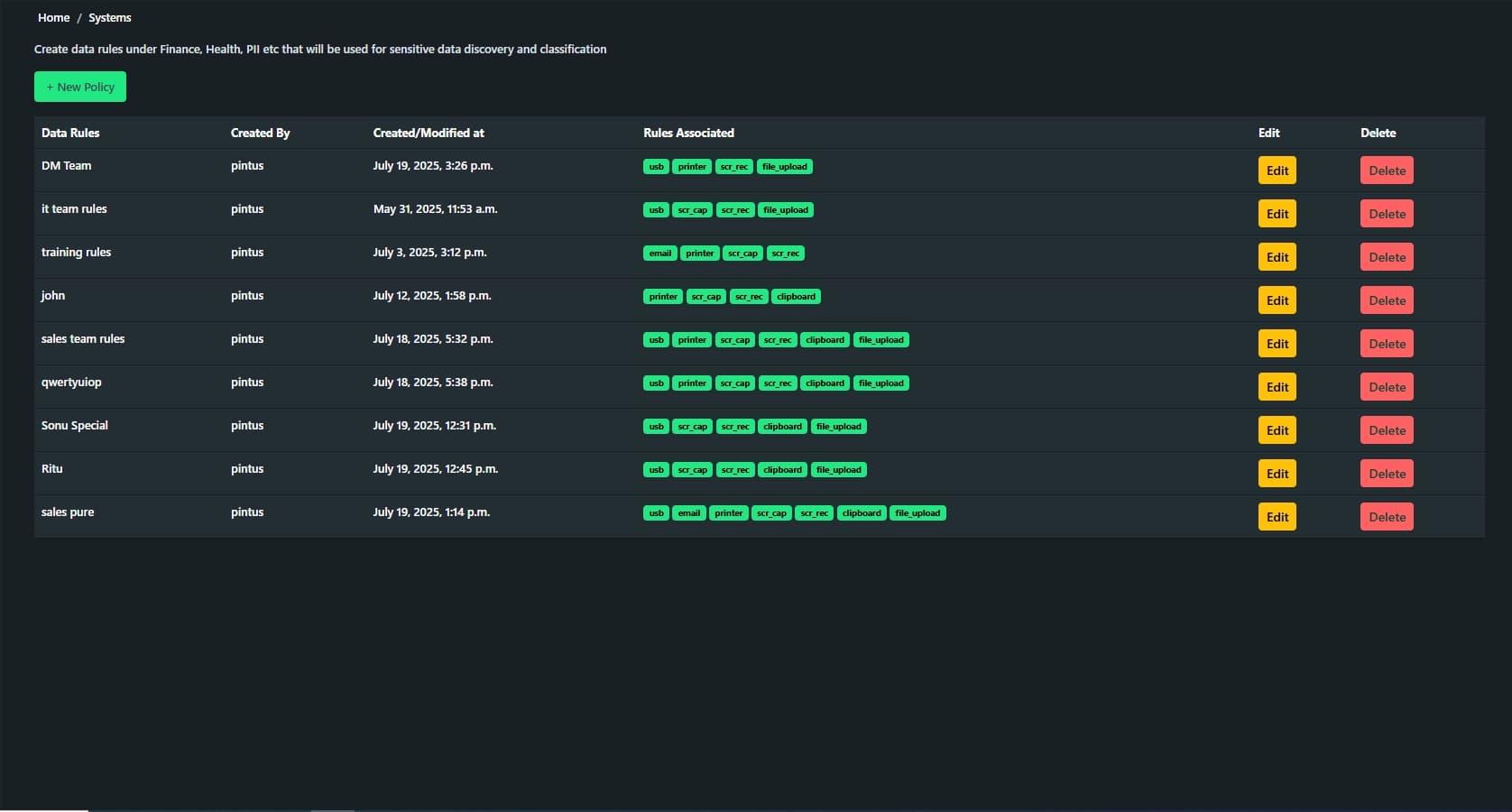
Key Features of Craw Security DLP Services
Some of the key features of Craw Security world-class DLP Services are mentioned below:
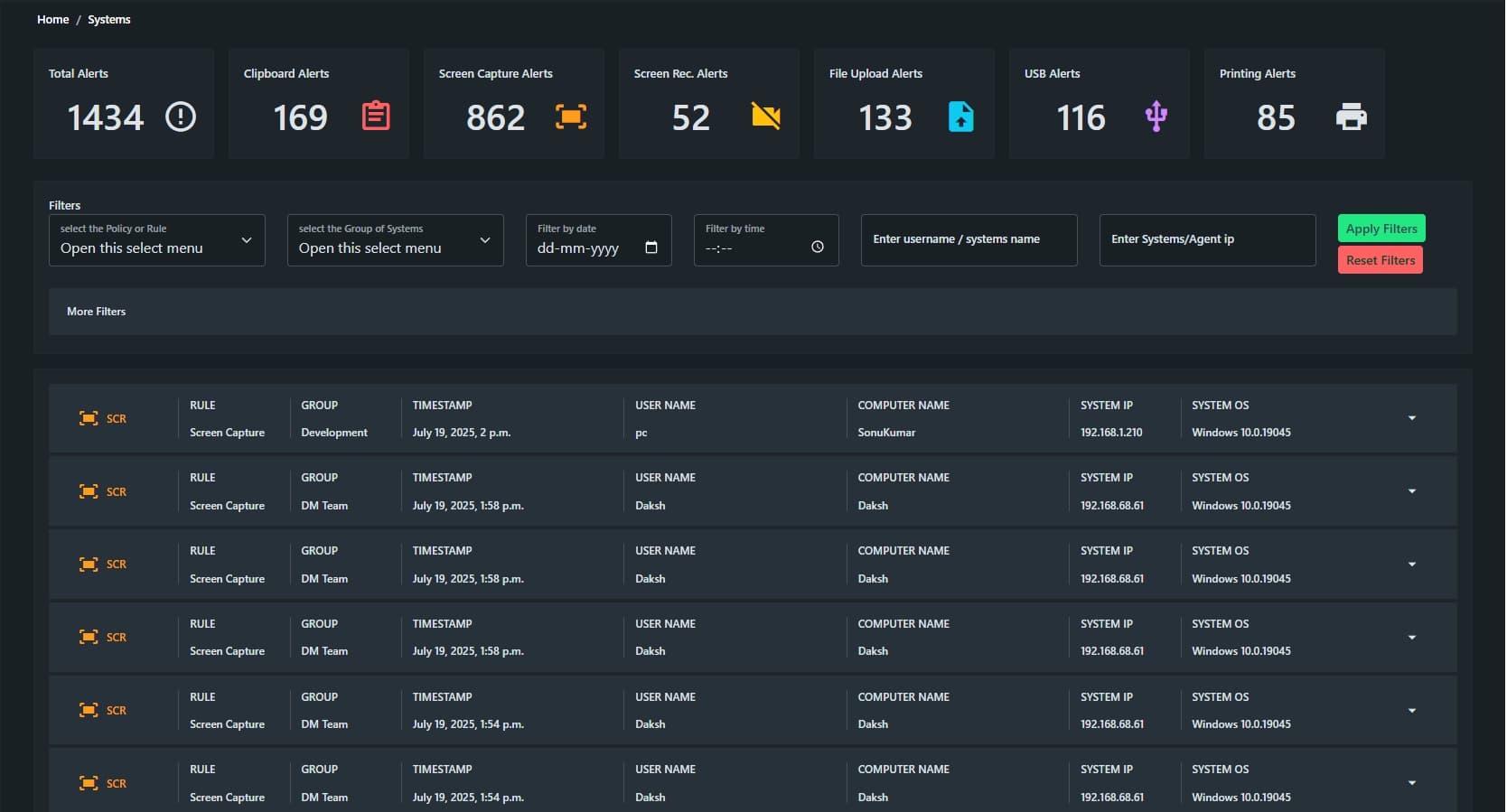
Real-Time Data Monitoring
- Continuously observes file movements, email content, and endpoint activities to detect any unusual data behavior instantly.
- Provides proactive alerts for suspicious access or sharing attempts before they escalate into breaches.
- Helps security teams respond faster by offering detailed logs of user interactions with sensitive data in real-time.
- Ensures ongoing visibility into cloud storage operations, including uploads, downloads, and third-party sharing.
Context-Aware Policies
- Applies adaptive DLP rules that automatically adjust based on the user's role, department, or access level within the organization.
- Detects the context behind data usage, such as whether a file is being moved internally or sent to an external recipient, and reacts accordingly.
- Recognizes patterns in user behavior to distinguish between regular operations and potential insider threats or misuse.
- Allows granular control over policy enforcement, ensuring precision without affecting workflow efficiency.
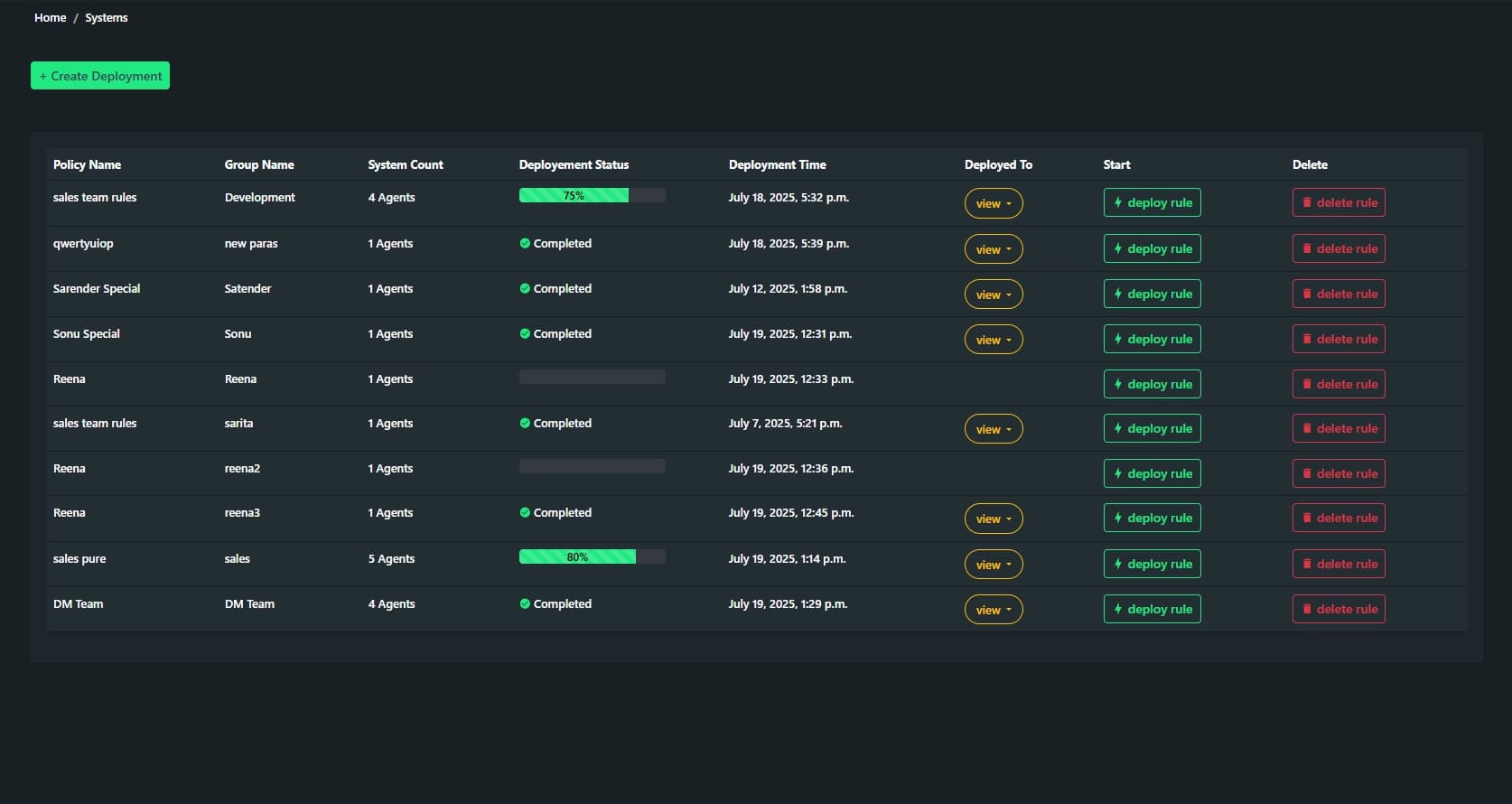
Data-in-Motion Protection
- Monitors and controls the transfer of sensitive information over external channels such as USB devices, instant messengers, and personal email accounts.
- Implements encryption and blocking mechanisms to prevent the accidental or intentional leak of confidential data during transmission.
- Supports advanced filtering to analyze file content in transit and determine whether sharing is compliant with organizational policies.
- Seamlessly integrates with existing communication tools to ensure smooth yet secure workflows.
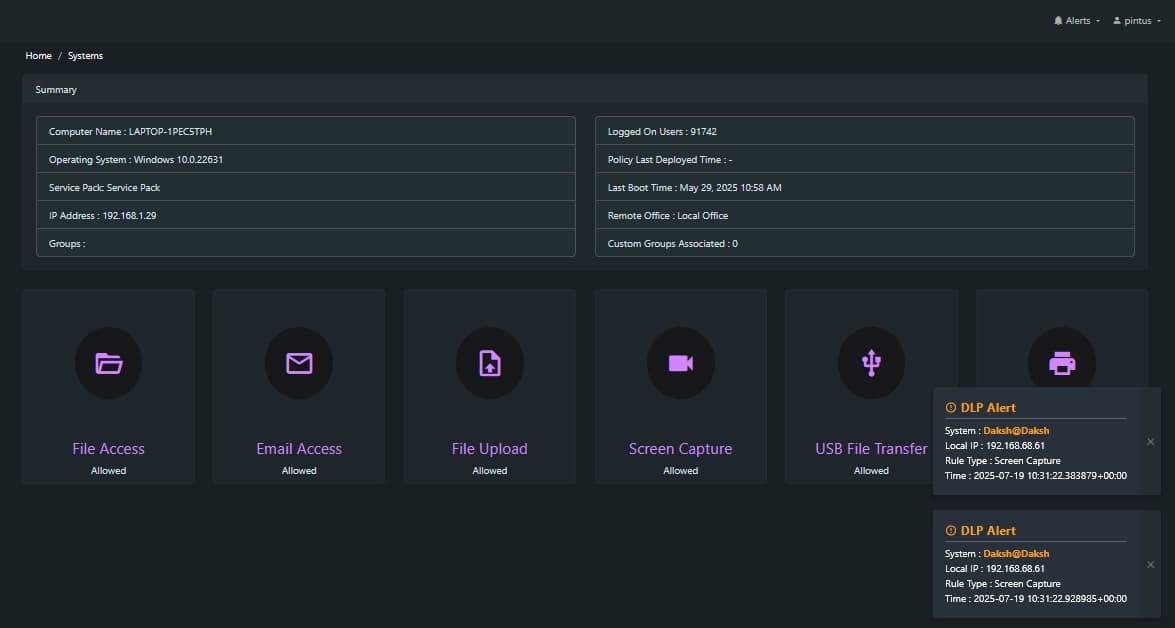
Centralized Endpoint Monitoring Dashboard
- Provides a real-time overview of system-level permissions and user activity across endpoints.
- Displays access status for key functionalities like file access, uploads, email, screen capture, and USB transfer.
- Shows detailed system attributes such as hostname, IP address, OS version, and login info to aid auditing.
- Includes live DLP alerts with timestamped logs to highlight policy violations like screen captures or data leaks.
Highlights of Implementing DLP from CrackTheLab
A few of the prime advantages of implementing DLP Services from CrackTheLab from the House of Craw Security are mentioned below:
Prevents Costly Data Breaches
Ensures Regulatory Compliance (ISO 27001, HIPAA, GDPR, etc.)
Strengthens Enterprise-Wide Security Posture
Reduces Insider Threats and Accidental Data Exposure
Improves Visibility and Control Over Critical Information
Enables Safe Remote Work and BYOD Environments
Why DLP Implementation?
One of an organization's most important assets is data, and its exposure or loss can have serious repercussions, including financial losses and legal and regulatory consequences. DLP solutions address possible hazards related to sensitive data misuse by offering a multi-layered approach to data protection.
This is one of the main reasons to use DLP:
Prevent Data Leakage
DLP solutions assist in keeping an eye on and managing the flow of private data to prevent leaks through web uploads, email, and other unapproved means.
Compliance with Regulations
DLP assists companies in adhering to legal and industry standards such as GDPR, HIPAA, PCI-DSS, and SOX, which require the safeguarding of sensitive data and personally identifiable information (PII).
Reduce Insider Threats
DLP can assist in identifying and reducing possible hazards brought on by malevolent insiders or inadvertent data leaks by keeping an eye on internal communications and data access.
Protect Intellectual Property
DLP systems stop important trade secrets and intellectual property (IP) from being exposed or shared without authorization.
Enhance Endpoint Protection
To ensure that sensitive data stays within safe bounds, DLP systems can be installed on endpoints to regulate its transfer to external devices.
Prevent Data Loss Incidents
DLP solutions provide real-time monitoring and automated response capabilities to prevent accidental or intentional data loss incidents before they occur.
Our DLP Implementation Services
Our DLP implementation services at Craw Security Pvt Ltd. offer a customized strategy for protecting the vital information of your company across endpoints, networks, cloud environments, and other access points.
Benefits of Taking DLP Services from CrackTheLab
Selecting CrackTheLab from Craw Security for your Data Loss Prevention (DLP) requirements entails working with one of the most reputable cybersecurity brands in India. Here's why businesses from all sectors depend on us:
Comprehensive Data Protection
We make sure that every vulnerability is fixed to safeguard your private information across endpoints, networks, cloud platforms, emails, USB devices, and mobile settings.
Expert-Led Implementation
Highly skilled cybersecurity specialists and certified professionals with extensive industry expertise and compliance framework understanding create and implement our DLP services.
Customizable Policies & Controls
Craw Security offers customized DLP solutions that are in line with industry standards, data sensitivity thresholds, and your unique business strategy.
Seamless Integration with Existing Systems
Our DLP solutions eliminate the need for significant adjustments or interruptions by seamlessly integrating with your current IT tools and infrastructure.
Real-Time Threat Detection & Response
We implement incident response and real-time monitoring systems, enabling your security team to respond promptly to possible leaks or unauthorized data movement.
Regular Audits & Compliance Reporting
Through automated policy enforcement and reporting, Craw Security keeps your company audit-ready and in compliance with ISO 27001, PCI-DSS, GDPR, HIPAA, and more.
Cloud and Endpoint Integration
Smooth interaction with endpoint systems, mobile devices, and cloud platforms for all-around security.
Detailed Incident Reporting
For incident analysis and legal requirements, detailed audit trails and compliance reports are required.
End-to-End Consulting & Support
Craw Security provides full DLP lifecycle management under one roof, from initial risk assessment to post-deployment training and continuing support.
Training + Services Under One Roof
Our in-house DLP certification programs give you a twofold edge by equipping your employees with the necessary skills and safeguarding the environment.
Scalable & Adaptable Solutions
Our DLP solutions are highly adaptable, scalable, and made to change as the data environment of your company becomes more complicated.
Which Organizations Can Benefit from DLP Solutions?
Our DLP services are made to cater to the particular requirements of numerous sectors, such as:
Healthcare Institutions
In order to safeguard patient health information (PHI).
Government Agencies
For the integrity of sensitive data and national security.
Financial Institutions
To protect consumer, transaction, and banking data.
IT & Software Companies
For R&D data, client information, and source code.
Educational Institutions
For protecting research and student data.
E-Commerce & Retail
To safeguard user credentials and payment details.
Universal Need for DLP
Apart from the above-mentioned sectors, any firm handling sensitive data, regardless of size or industry, needs to have a strong DLP plan in place to secure against any unwanted data compromization.
Our Approach: A Holistic & Tailored DLP Implementation Methodology
We take a thorough, multi-phase approach to DLP implementation, making sure the solution is tailored to your unique risk profile, business demands, and regulatory compliance specifications.
Initial Consultation & Assessment
Understanding the Data
We start by recognizing and categorizing the many kinds of data that your company manages, such as regulated, sensitive, and intellectual property data.
Risk Assessment
We conduct a comprehensive risk assessment to find out where your data is stored, who can access it, and what risks and weaknesses can arise from its use.
Defining Objectives
We collaborate closely with your security and compliance teams to establish clear goals for DLP implementation.
Current Security Posture
We evaluate your existing data security posture and identify areas where DLP can provide the most value.
DLP Solution Selection
Tool Evaluation
We recommend the best DLP solution based on your company's size, sector, and data protection requirements.
Custom Solution Design
We create a DLP architecture that seamlessly integrates with your current workflows and IT infrastructure.
Scalability & Performance
We guarantee that the DLP solution can grow with your company's requirements, regardless of size.
DLP Policy Definition & Customization
Policy Creation
We assist in creating precise DLP policies based on risk assessment and data classification.
Policy Granularity
We create policies with varying degrees of granularity to accommodate diverse data types and users.
Incident Response Policies
We set up automated incident response procedures including warnings, blocking, quarantining, or encrypting data.
Custom Actions
Automated actions to encrypt sensitive data, stop transfers, or issue user warnings when policies are violated.
Deployment & Integration
Endpoint Deployment
Install DLP agents on all endpoints for real-time monitoring of data access and transfer.
Network Integration
Integrate DLP with your network architecture to track and shield private information.
Email & Cloud Protection
Ensure DLP policies are followed for email and cloud platforms like Office 365 and Google Workspace.
Data Flow Monitoring
Track sensitive information movement across internal and external networks.
Monitoring & Reporting
Real-Time Alerts
Continuous monitoring with instant alerts for policy violations across all environments.
Incident Reporting
Comprehensive reports on data loss events with detailed context and response information.
User Activity Auditing
Monitor user behavior with private information to identify potential internal threats.
Compliance Reporting
Customizable reports for GDPR, HIPAA, and PCI-DSS compliance audits and reviews.
Incident Response & Forensics
Incident Handling
Practical measures to control and address data loss incidents, including investigation and system quarantine.
Forensics Investigation
Comprehensive forensics investigation to determine breach origin, impact, and prevention strategies.
Policy Refinement
Continuous improvement of DLP policies based on incident outcomes and emerging threats.
Ongoing Support & Optimization
Continuous Tuning
Ongoing optimization to reduce false positives and adapt to changing threats and requirements.
Training & Awareness
Comprehensive training for employees to understand DLP regulations and prevent violations.
Periodic Audits
Routine security audits to evaluate DLP effectiveness and ensure regulatory compliance.
Ready to Implement Comprehensive DLP Protection?
Our proven 7-phase methodology ensures your organization's sensitive data is protected with enterprise-grade DLP solutions tailored to your specific needs.
Ready to Secure Your Data with DLP Solutions?
Partner with India's top VAPT solutions provider and protect your organization's most valuable asset - your data.
Find detailed info related to Data Loss Prevention with the help of this informative webpage by Craw Security, the Best VAPT Solutions Provider in India.
