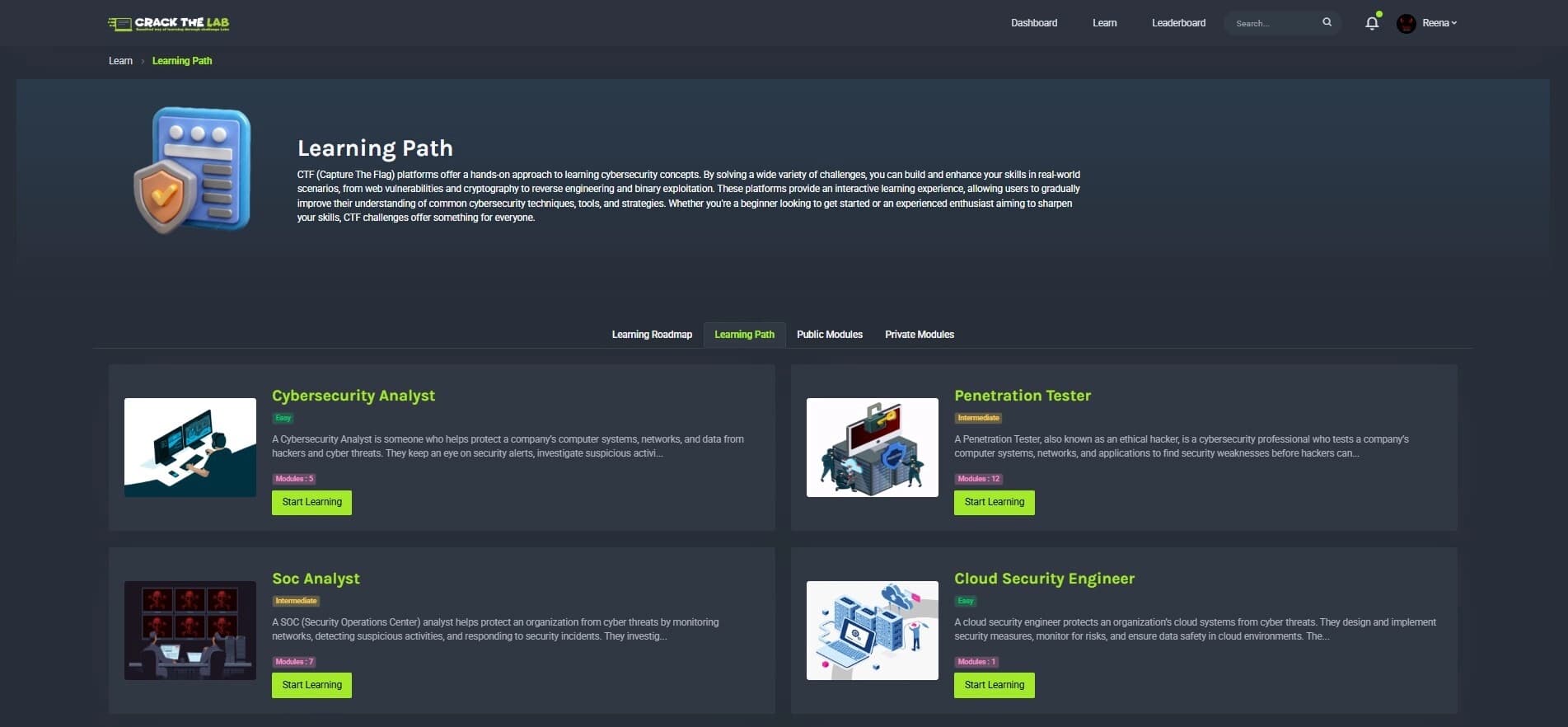
What is CTF?
In the cybersecurity competition format known as CTF (Capture The Flag), teams or individuals must solve a variety of puzzles in order to "capture flags" (secret codes). These warning signs are concealed within purposefully weak networks, systems, or applications.
Like actual attackers, participants use their hacking expertise to find and take advantage of these weaknesses.
Key Features of CTF Sessions from CrackTheLab
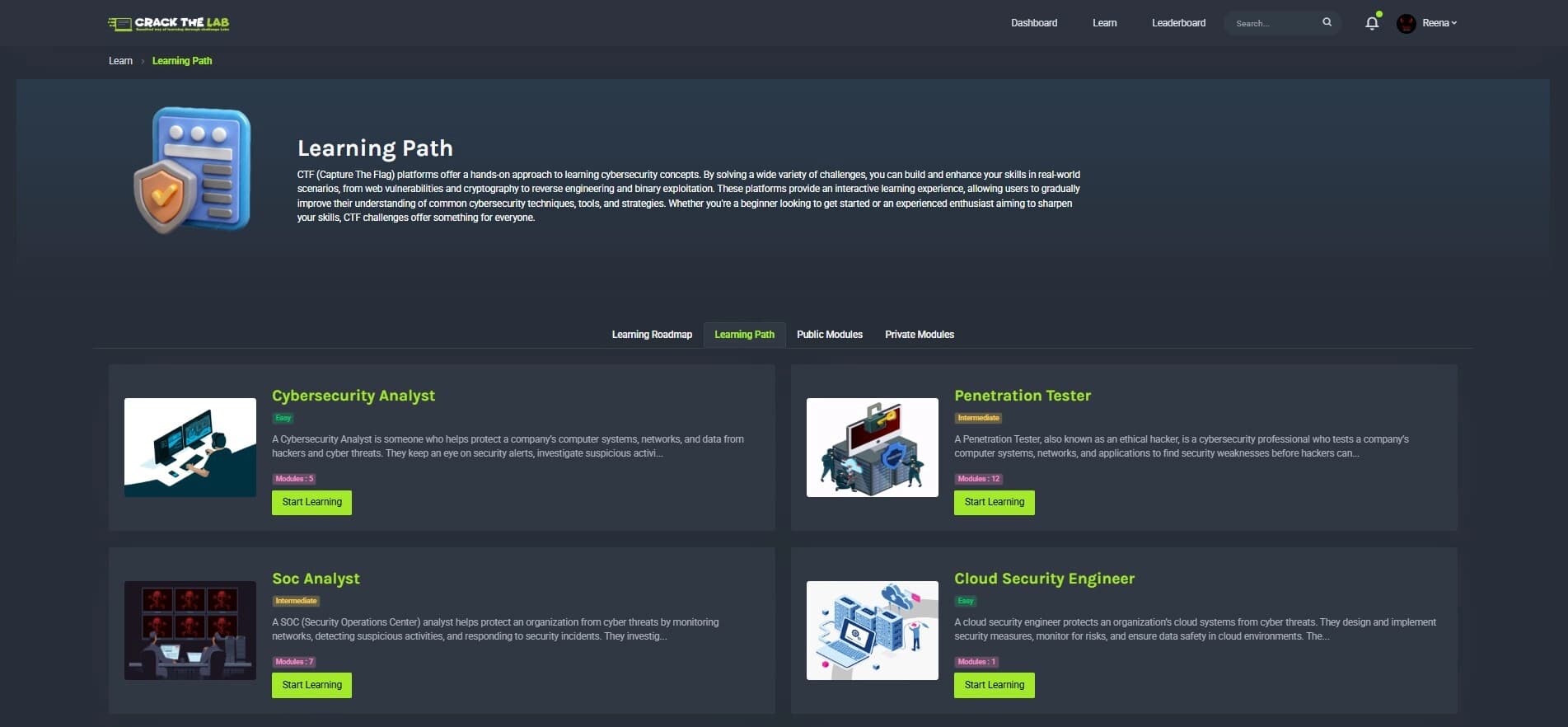
Real-World Challenges
Expert pentesters create each challenge, which replicates vulnerabilities found in actual VAPT engagements.
Challenges designed by certified ethical hackers and penetration testers
Scenarios based on actual vulnerabilities found in enterprise environments
Regular updates with latest attack vectors and defense techniques
Multi-industry challenge scenarios including finance, healthcare, and government
Multi-Level Complexity
Go at your own speed as you go through problems ranging from easy to difficult penetration testing scenarios.
Beginner-friendly challenges to build foundational security knowledge
Intermediate scenarios focusing on common attack methodologies
Advanced challenges requiring deep technical expertise
Expert-level scenarios simulating sophisticated APT attacks
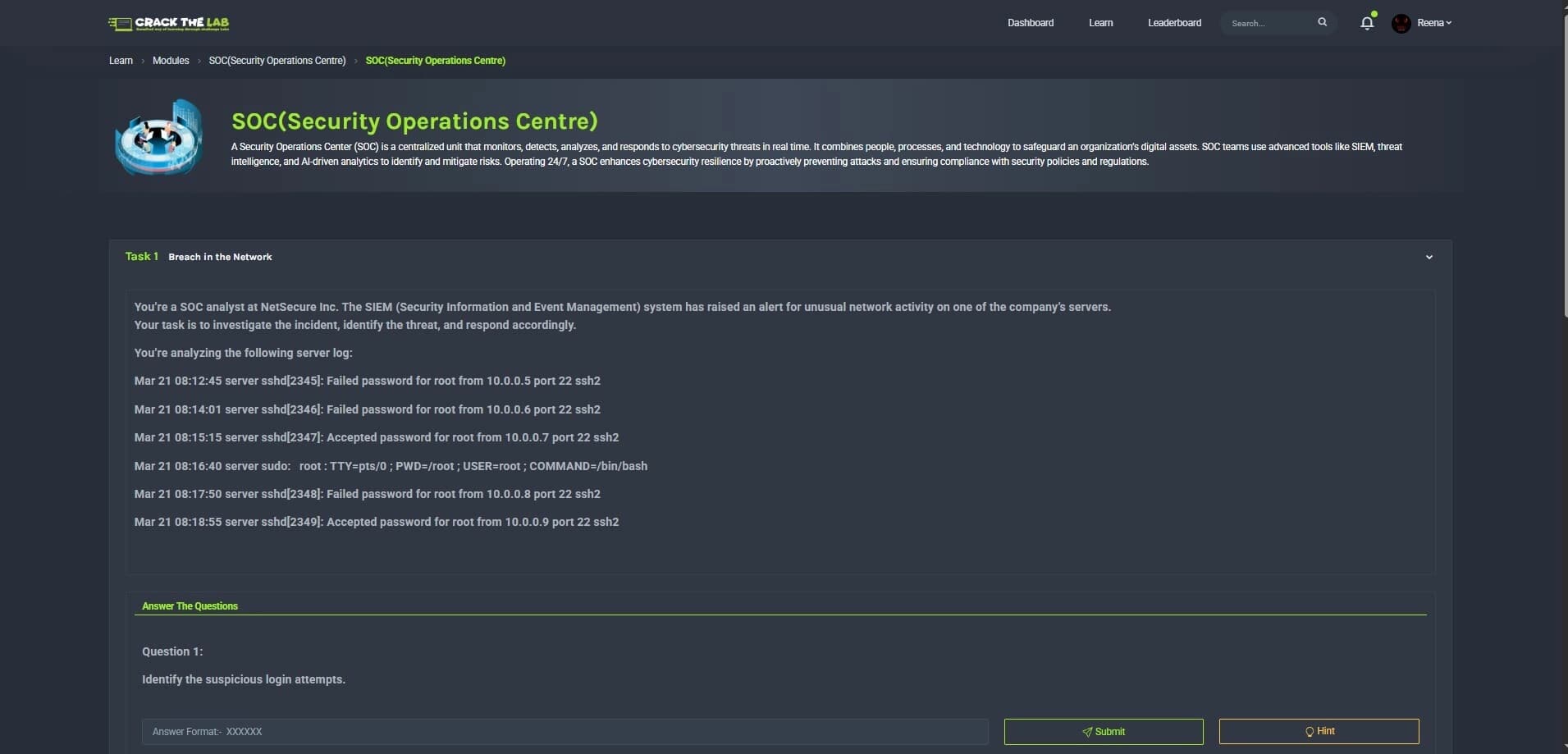
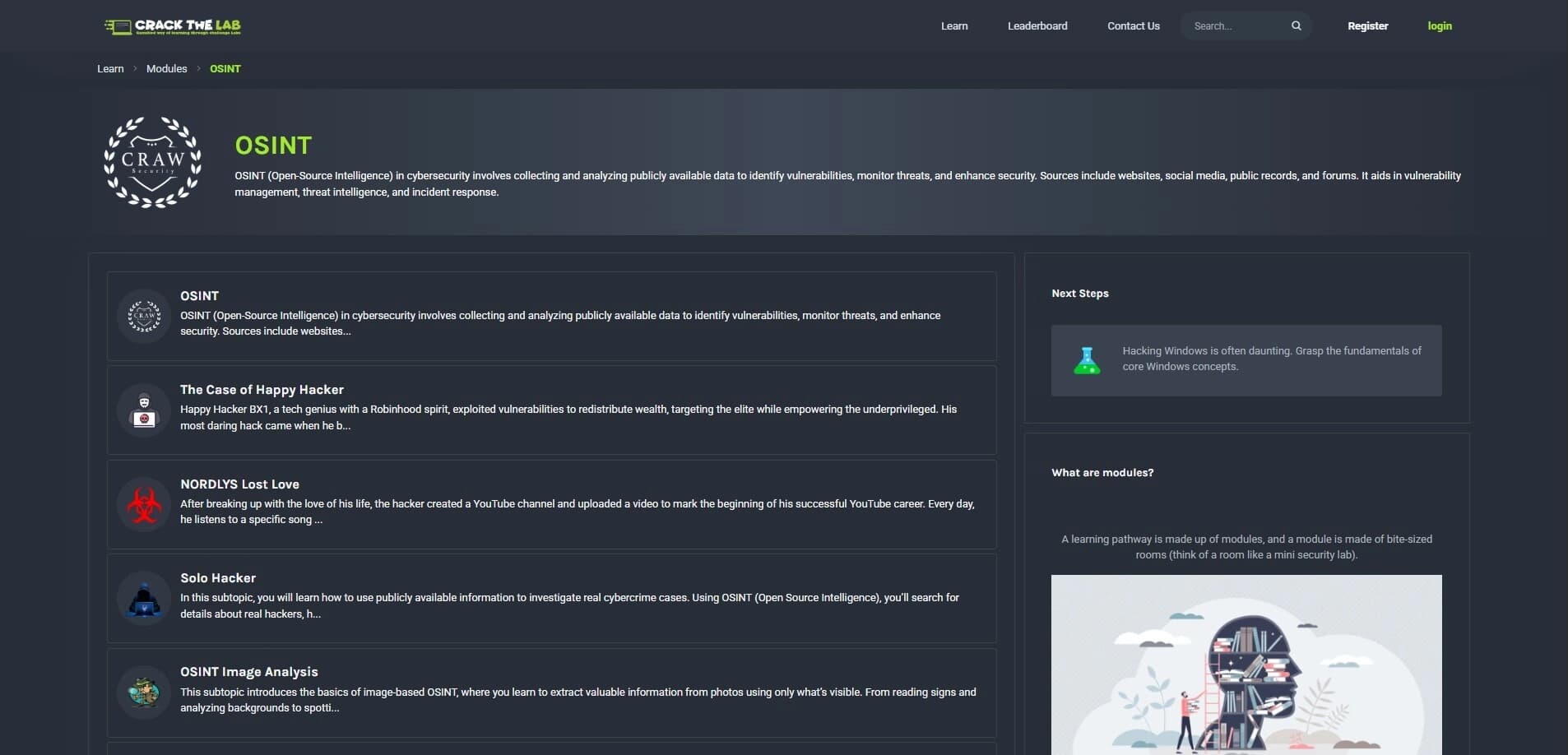
Hands-On Learning
Examine your abilities in a variety of areas, such as OSINT, Reverse Engineering, Forensics, Network Security, Web Exploitation, and Cryptography.
OSINT challenges for information gathering and reconnaissance
Web Application Security with OWASP Top 10 vulnerability exploitations
Network Security challenges including packet analysis and intrusion detection
Digital Forensics scenarios for incident response and evidence analysis
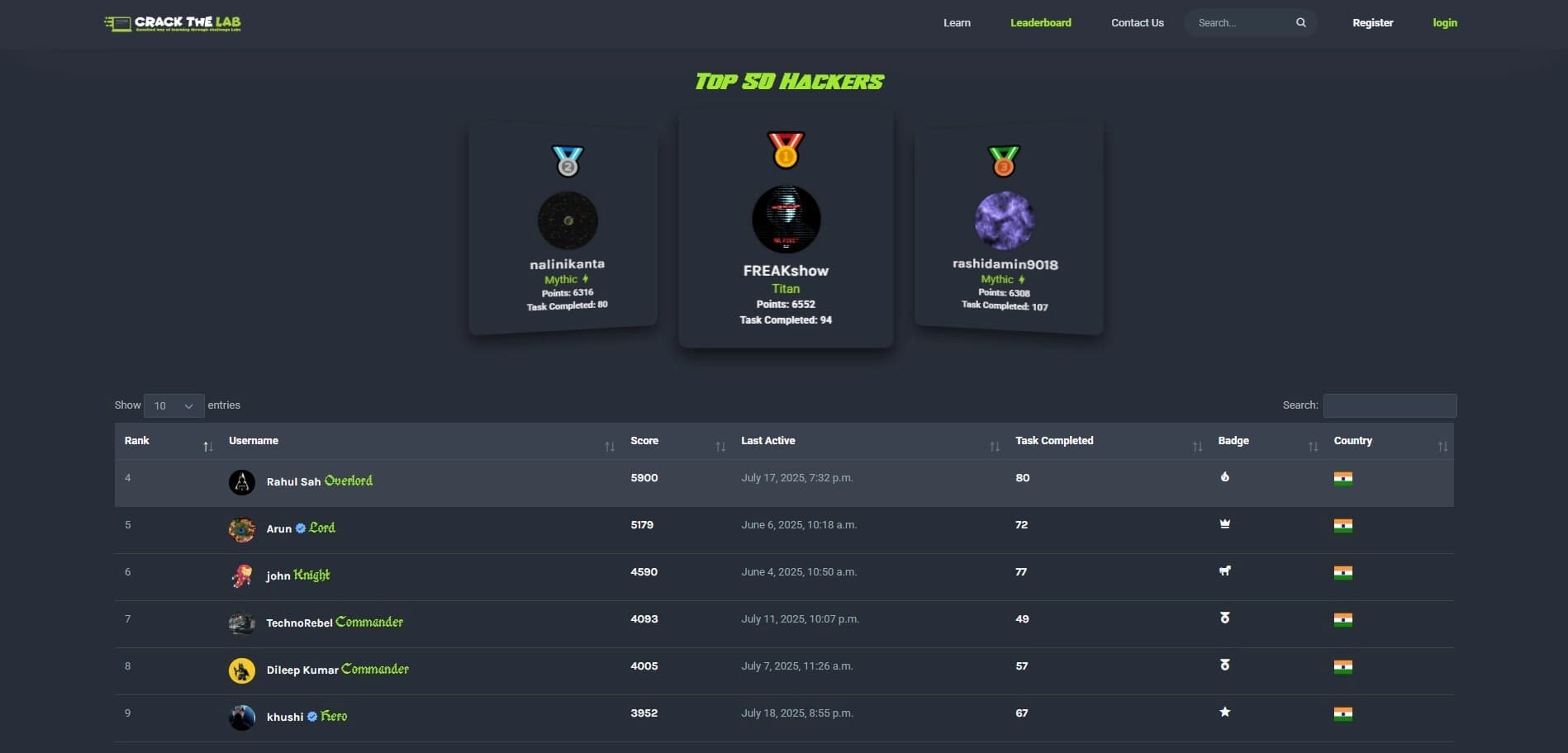
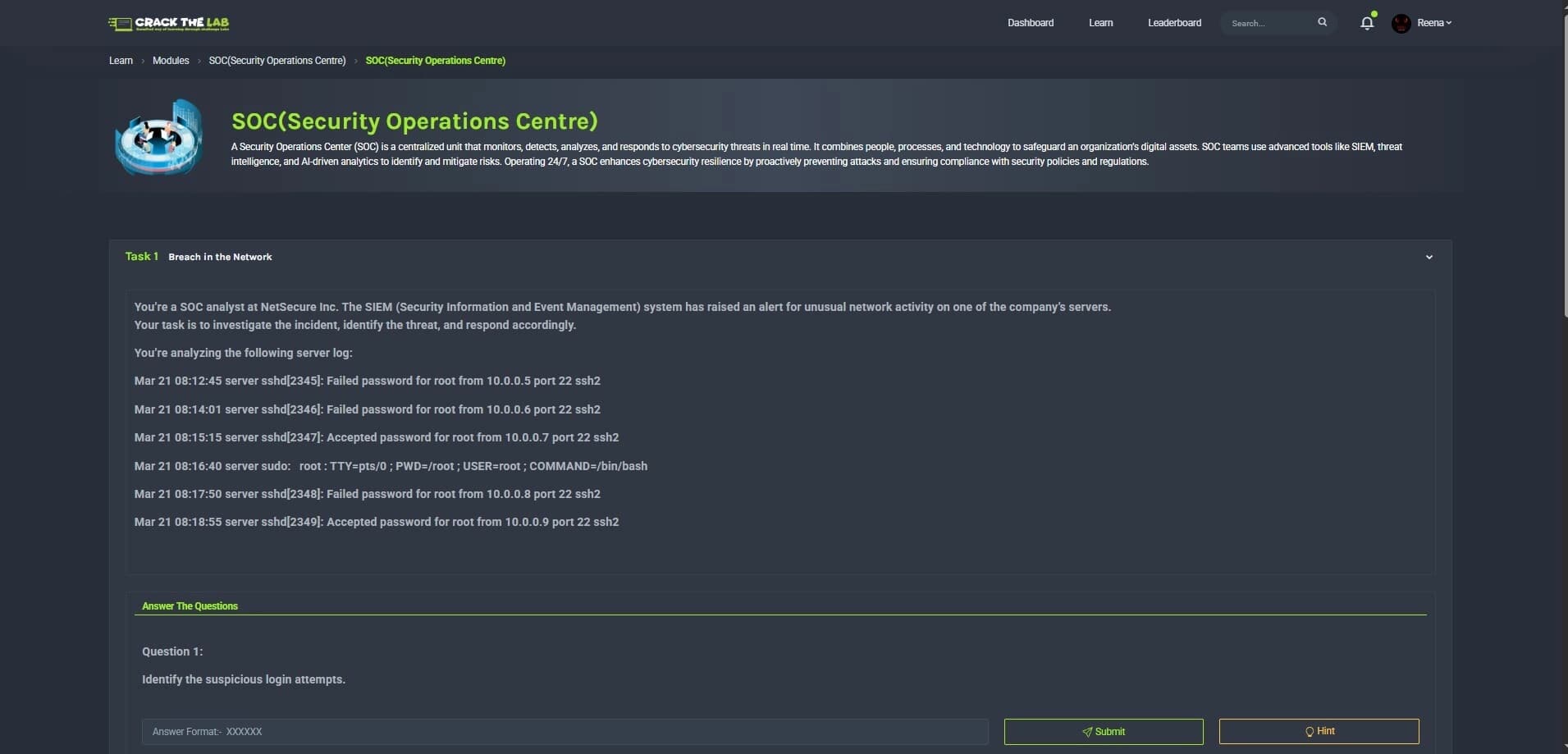
Live Leaderboards
Compete against professionals and your peers. Monitor your performance and rank in real time.
Real-time ranking system showing your progress against global participants
Monthly competitions with special recognition for top performers
Team-based challenges for collaborative problem solving
Achievement badges for completing specific challenge categories
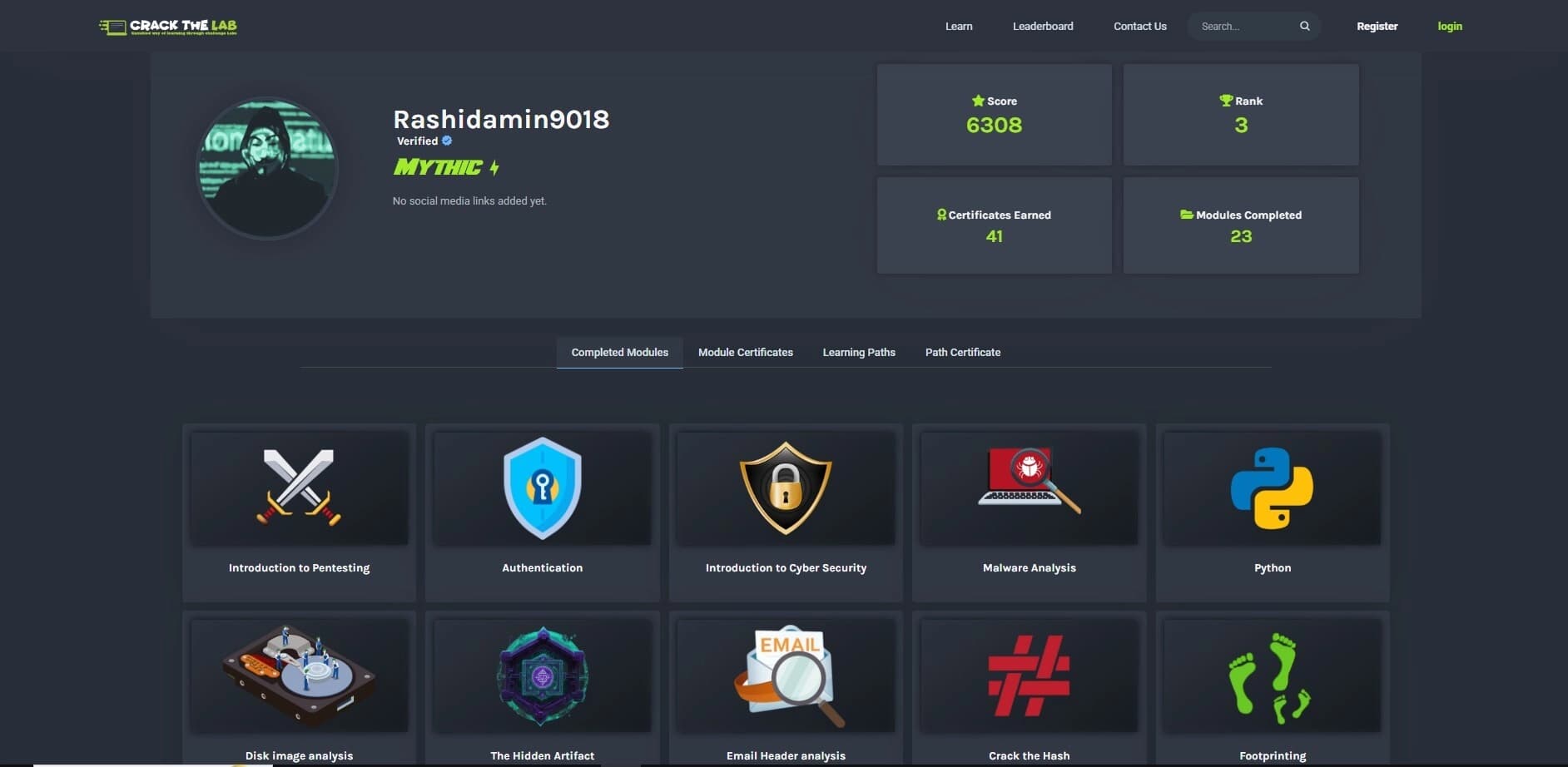
Isolated Lab Environments
Practice in secure sandbox environments designed to mimic actual infrastructure.
Fully isolated virtual machines preventing any security risks
Pre-configured environments with vulnerable applications and systems
Cloud-based infrastructure ensuring 24/7 availability
Support for multiple operating systems and security tools
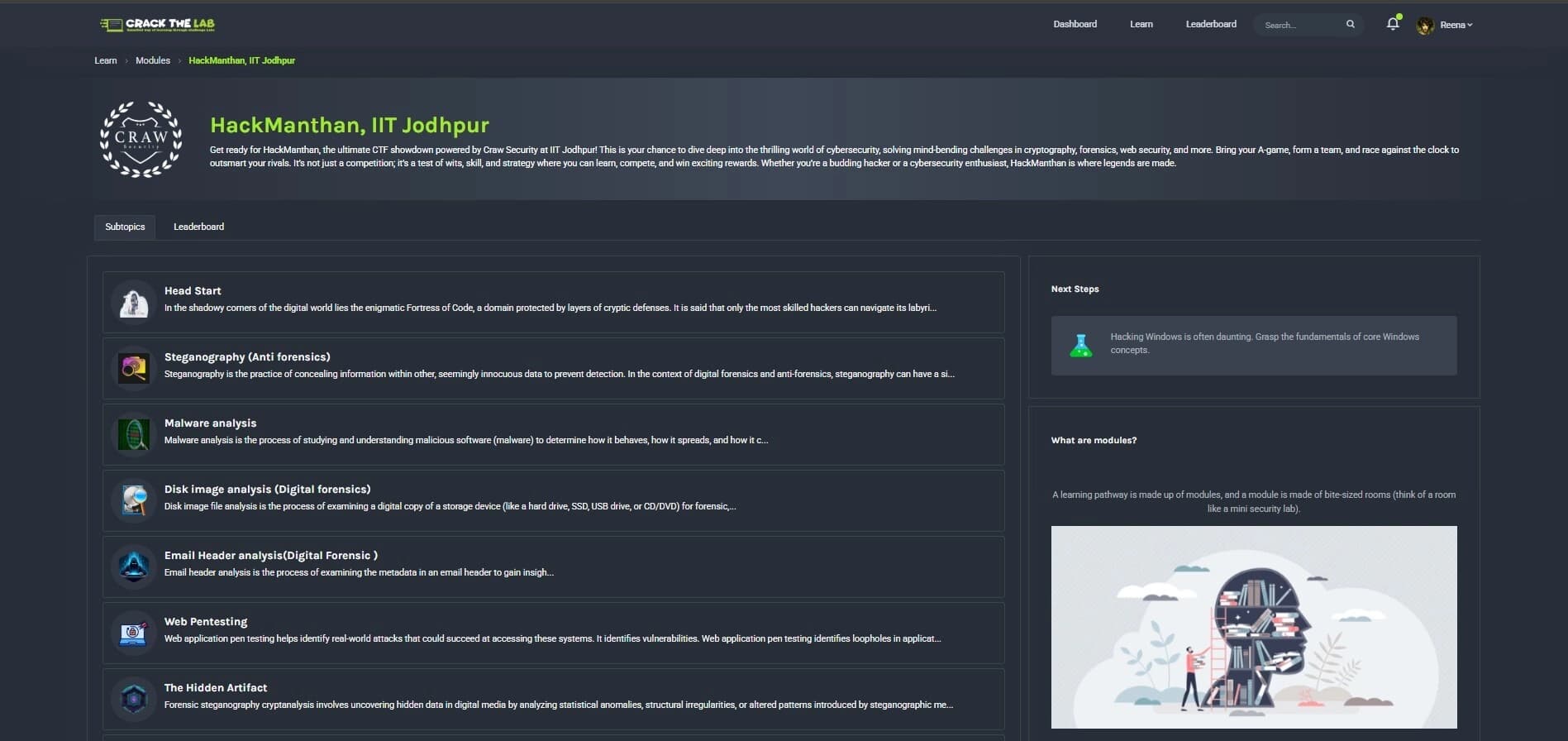
Regular Events & Hackathons
Take part in monthly battles, national-level cyber tournaments, and time-limited CTF events.
Monthly themed competitions focusing on specific security domains
National-level cybersecurity tournaments with industry recognition
Time-limited sprint challenges for intensive skill building
Corporate team-building events for organization-wide security training
How does it work?
Sign Up
Sign Up on the Craw CTF Platform
Choose Challenge
Choose Your Challenge from the available categories
Solve & Capture
Solve & Capture Flags to earn points
Climb Leaderboard
Climb the Leaderboard and earn your bragging rights
Win Rewards
Win Rewards, Certifications, and More!
Advantages of CTF Sessions from CrackTheLab
Practical Skill Enhancement
Go beyond theory and acquire practical VAPT and ethical hacking abilities.
Think Like a Hacker
To improve your defenses against threats, learn the strategies and attitude of actual attackers.
Team-Based or Solo Play
Develop critical thinking and coordination skills through group or solo missions.
Feedback & Hints System
Are you stuck on a task? Seek professional advice to aid in your educational process.
Portfolio Boosting
Include your CTF accomplishments in bug bounty submissions, LinkedIn profiles, and resumes.
Which organizations can use this?
Both people and companies can benefit from our CTF platform, which includes:
CTF Events at Different IITs - Capture The Flag Challenges







Loading Campus Image...

IIT Jodhpur
1 of 3
Use arrow keys to navigate
Certification Benefits
Those who finish the Craw Security CTF challenges successfully receive:
CTF Completion Certificates
Industry-wide recognition for confirming practical VAPT and ethical hacking abilities.
Digital Badges
Display your accomplishments on reputable websites such as GitHub and LinkedIn.
Hall of Fame Recognition
Become listed on the elite performers board of Craw Security.
Rewards & Prizes
Get a chance to win special prizes in hackathons held at the national level.
These qualifications improve your chances of getting high-paying positions in VAPT, SOC, Red Teaming, and InfoSec operations in addition to enhancing your credibility in the cybersecurity field.