What is Phishing Simulation?
Phishing Simulation is a proactive cybersecurity tool that evaluates employees abilities to recognize and steer clear of actual phishing threats by sending them controlled, fictitious phishing emails. It's a useful tool for gauging security knowledge, tracking attack vulnerability, and creating a cyber-aware culture within your company.
Powerful Features for Complete Protection
Our comprehensive platform offers everything you need to run effective phishing simulations and security awareness training
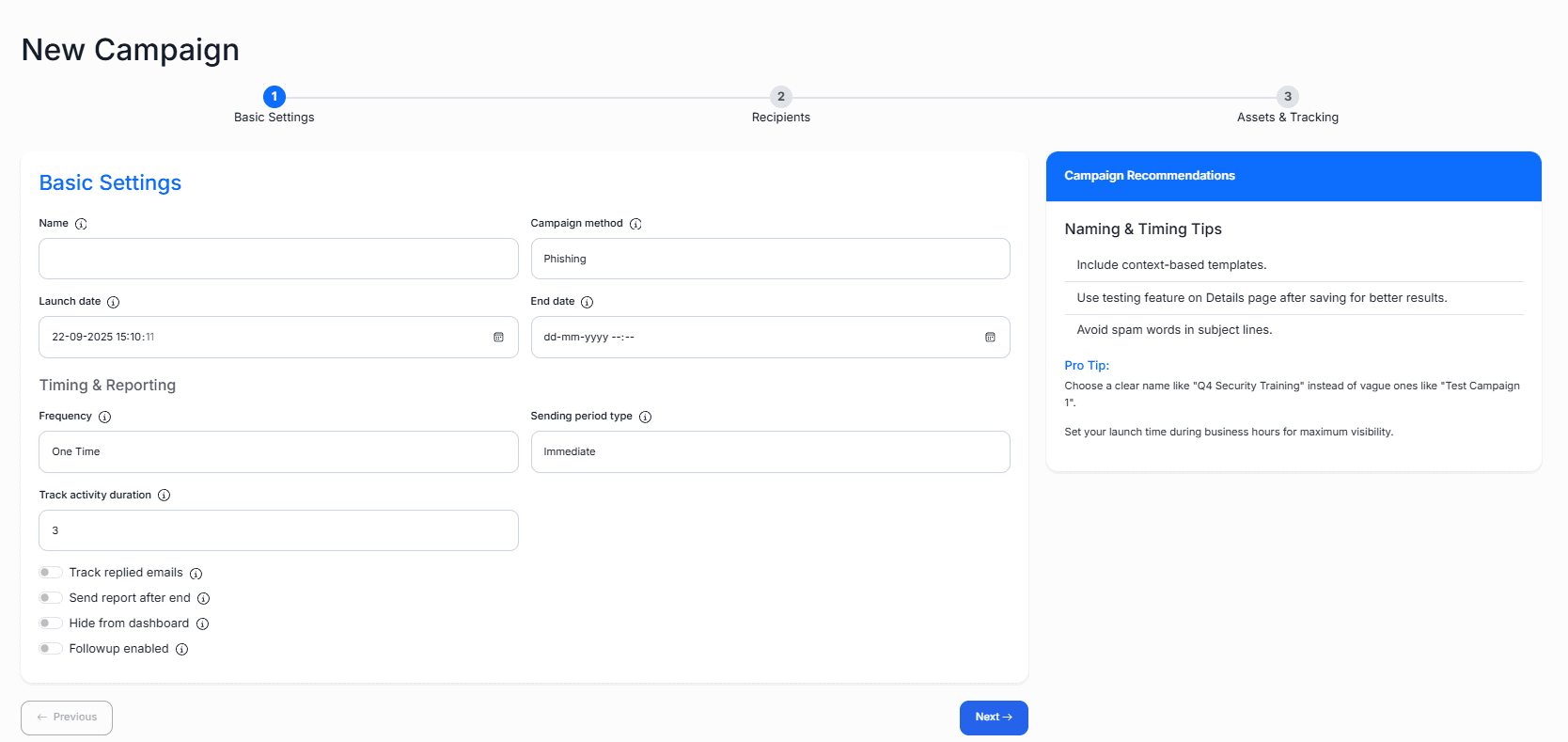
Step 1: Basic Settings
Campaign Setup
Configure campaign name, phishing method, launch dates, and timing preferences for optimal delivery.
Tracking Options
- Track activity duration (3-30 days)
- Monitor replied emails and engagement
- Send automated reports after completion
Campaign Workflow & Scheduling
One-Click Onboarding
Public signup form auto-provisions tenants, sends welcome emails and seeds sample campaigns.
Flexible Scheduling
One-time or recurring sends with auto throttling controls (msgs per minute/hr).
Conditional Follow-Ups
Trigger additional emails based on opens, clicks or non-responders.
Sending Profiles
Multiple SMTP servers or SendGrid API keys for reliable delivery.
One-Click Onboarding
Public signup form auto-provisions tenants, sends welcome emails and seeds sample campaigns.
Flexible Scheduling
One-time or recurring sends with auto throttling controls (msgs per minute/hr).
Conditional Follow-Ups
Trigger additional emails based on opens, clicks or non-responders.
Sending Profiles
Multiple SMTP servers or SendGrid API keys for reliable delivery.
Processing Engine & Scalability
Automation Campaigns
Run once, engage every day. Your email engine fires off targeted campaigns on a daily schedule—no manual campaign setup, no "send" button needed.
AI-based Scheduling
The right message, every time. Our AI-based algorithm analyzes user behavior and campaign history to automatically pick, and send the best email template.
Automation Campaigns
Run once, engage every day. Your email engine fires off targeted campaigns on a daily schedule—no manual campaign setup, no "send" button needed.
AI-based Scheduling
The right message, every time. Our AI-based algorithm analyzes user behavior and campaign history to automatically pick, and send the best email template.
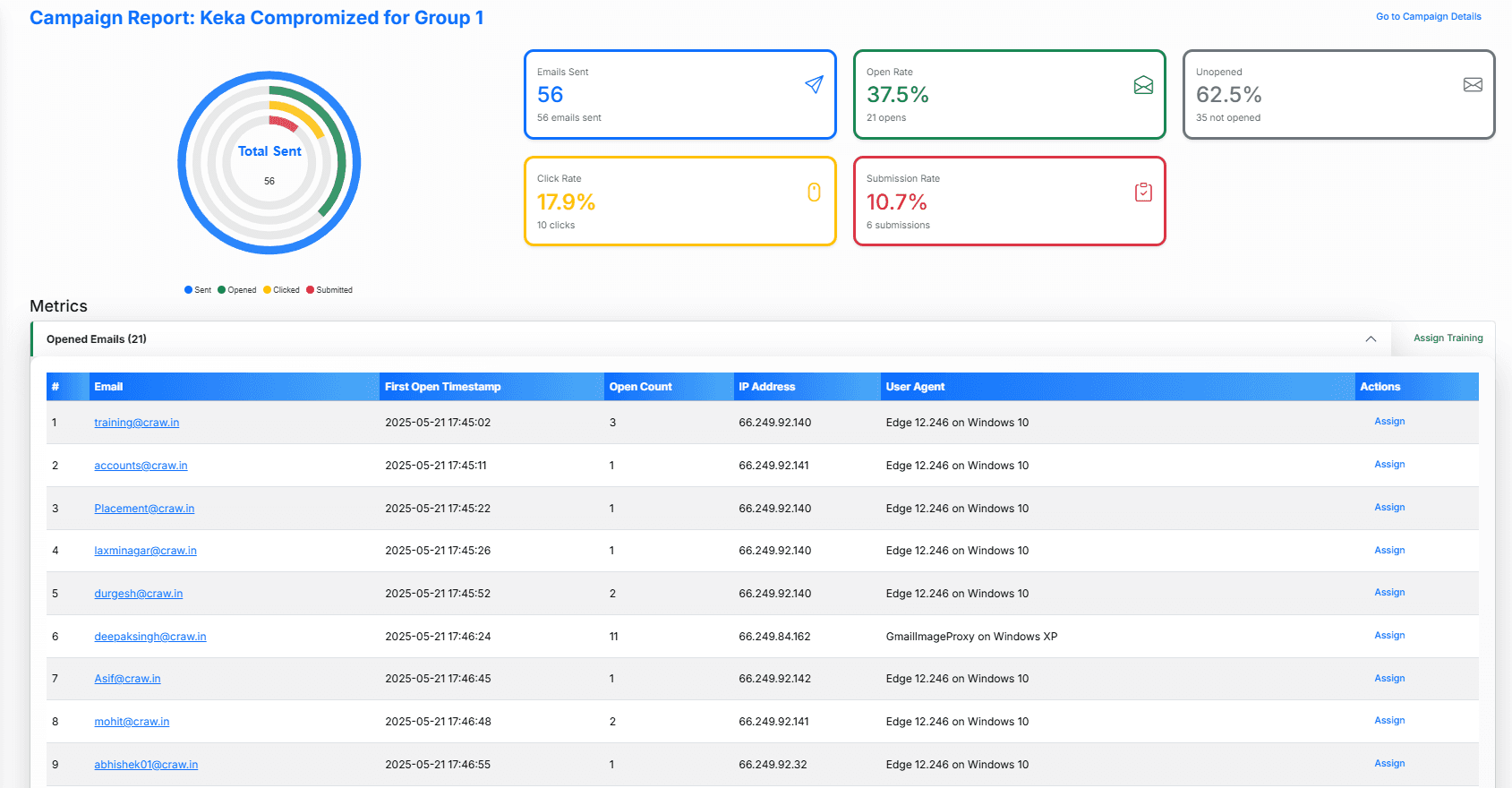
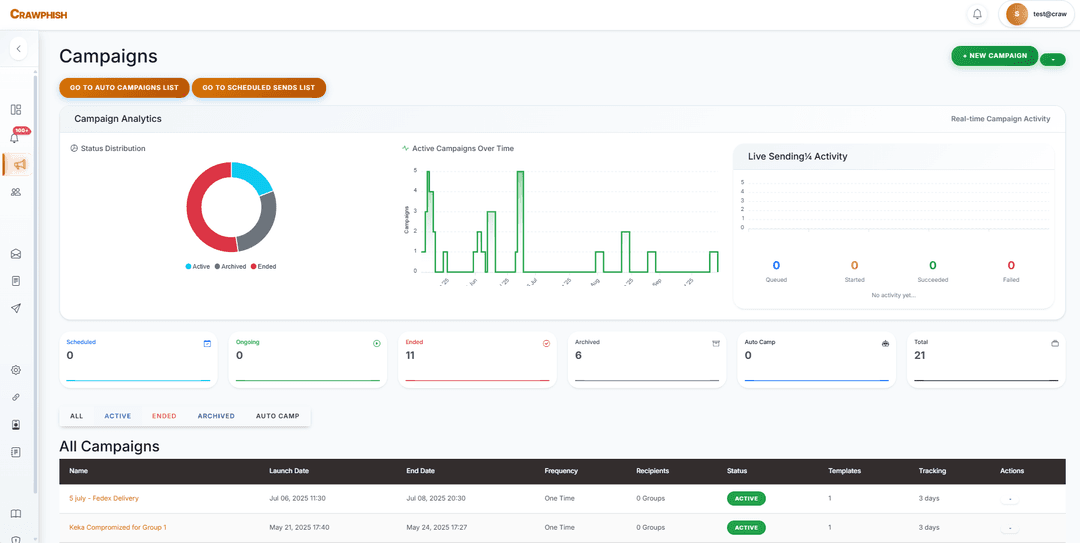
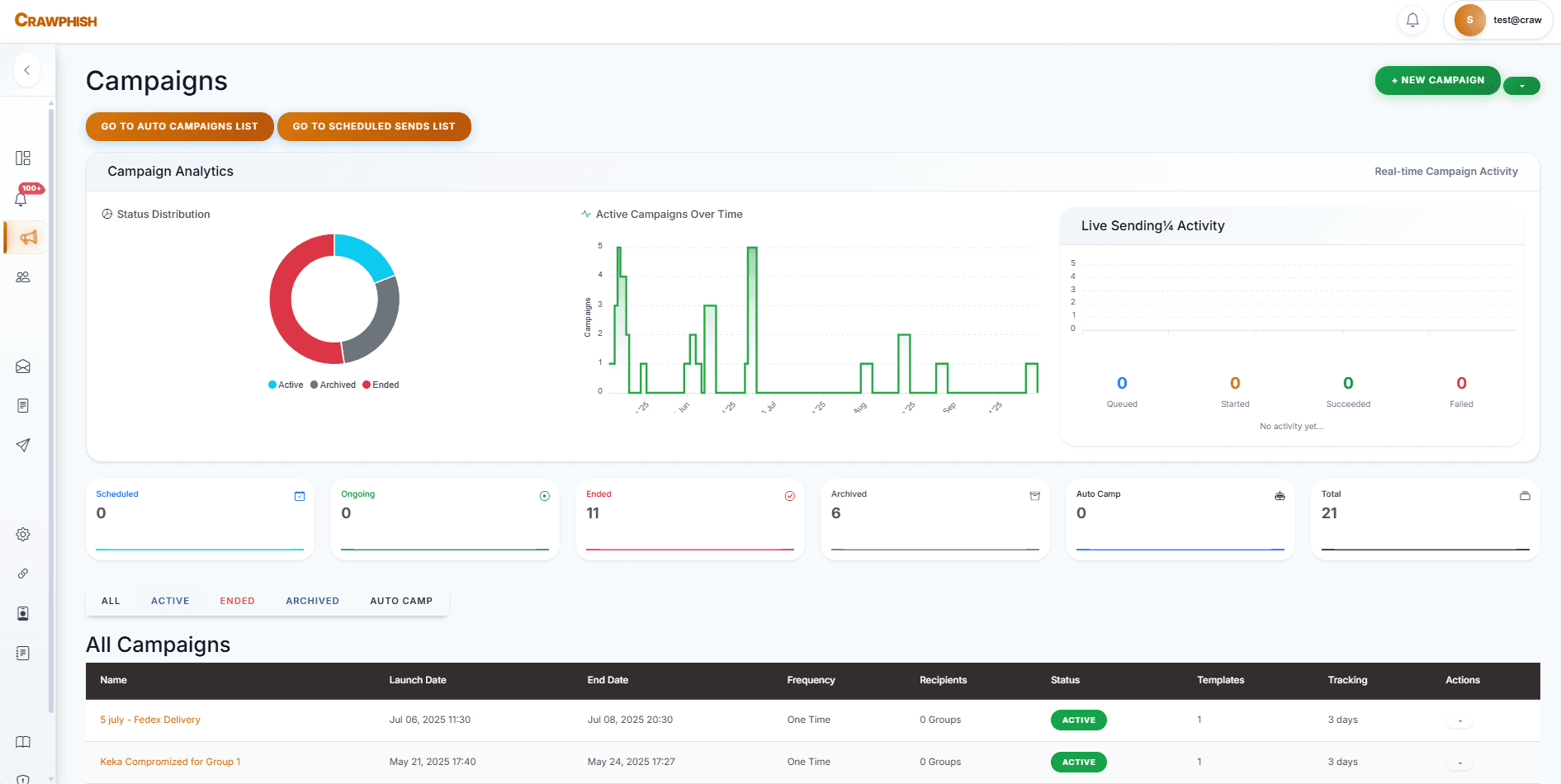
Analytics, Reporting & Integrations

Real-Time Dashboard
Live counters, charts, heatmaps, cohort retention and Sankey diagrams.
Exportable Reports
PDF exports of opens, clicks, submissions and vulnerability scores.
Webhooks & REST API
Push JSON payloads on events into Slack or your own tools.
Audit & Compliance
Field-level encryption, CSRF protection, and tenant-scoped audit logs.

Real-Time Dashboard
Live counters, charts, heatmaps, cohort retention and Sankey diagrams.
Exportable Reports
PDF exports of opens, clicks, submissions and vulnerability scores.
Webhooks & REST API
Push JSON payloads on events into Slack or your own tools.
Audit & Compliance
Field-level encryption, CSRF protection, and tenant-scoped audit logs.
Training Portal & Education
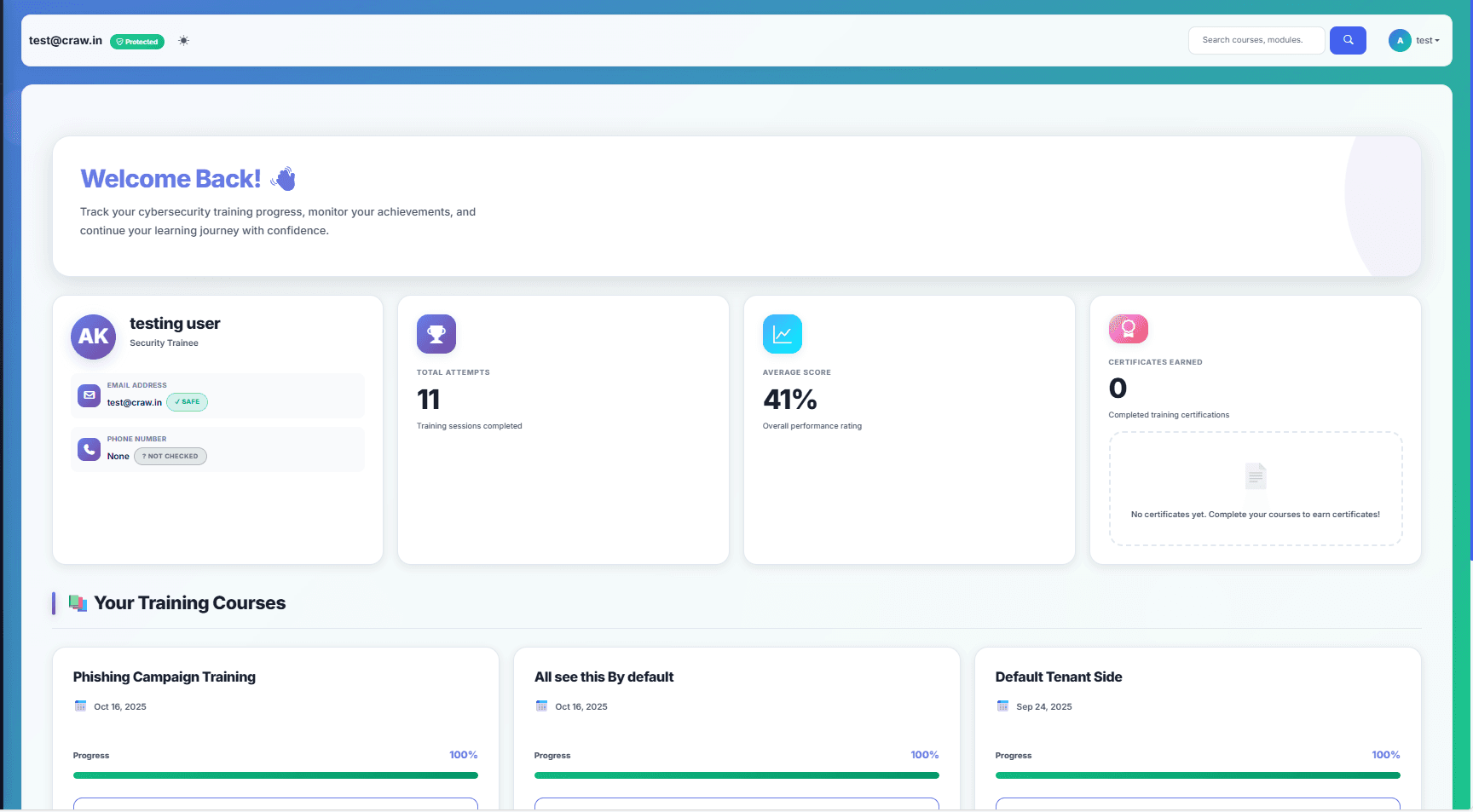
User Engagement & Post-Phish Training
Auto-assign courses, quizzes & interactive content to users who click or submit.
Issue PDF certificates and badges upon course completion.
Clean & Robust Training Portal
User Engagement & Post-Phish Training
- Embedded Training Modules
Auto-assign courses, quizzes & interactive content to users who click or submit.
- Automated Certifications
Issue PDF certificates and badges upon course completion.
Clean & Robust Training Portal
- Comprehensive course library
- Interactive modules with quizzes
- Certificate assignment for completed paths
- Shareable certificates with unique UUID

Realistic Phishing Templates
Our extensive library of phishing templates mimics real-world attacks to effectively test your employees awareness






200+ Pre-Built Templates
Business Email Compromise
Templates mimicking CEO fraud, invoice scams, and urgent payment requests from executives.
Account Security Alerts
Fake security warnings about password resets, suspicious activity, or account verification needs.
Reward & Prize Notifications
Templates for fake rewards, lottery wins, or exclusive offers to test greed-based attacks.
Document & File Sharing
Simulated file sharing notifications from popular platforms with malicious attachment scenarios.
Customization Available: All templates can be tailored to match your organization's branding and specific scenarios.
Realistic Attack Scenarios
Simulations that closely resemble actual attacks including social engineering, malware attachments, and credential harvesting.
Customizable Campaigns
Tailored simulations based on your industry, staff responsibilities, and organizational structure for meaningful testing.
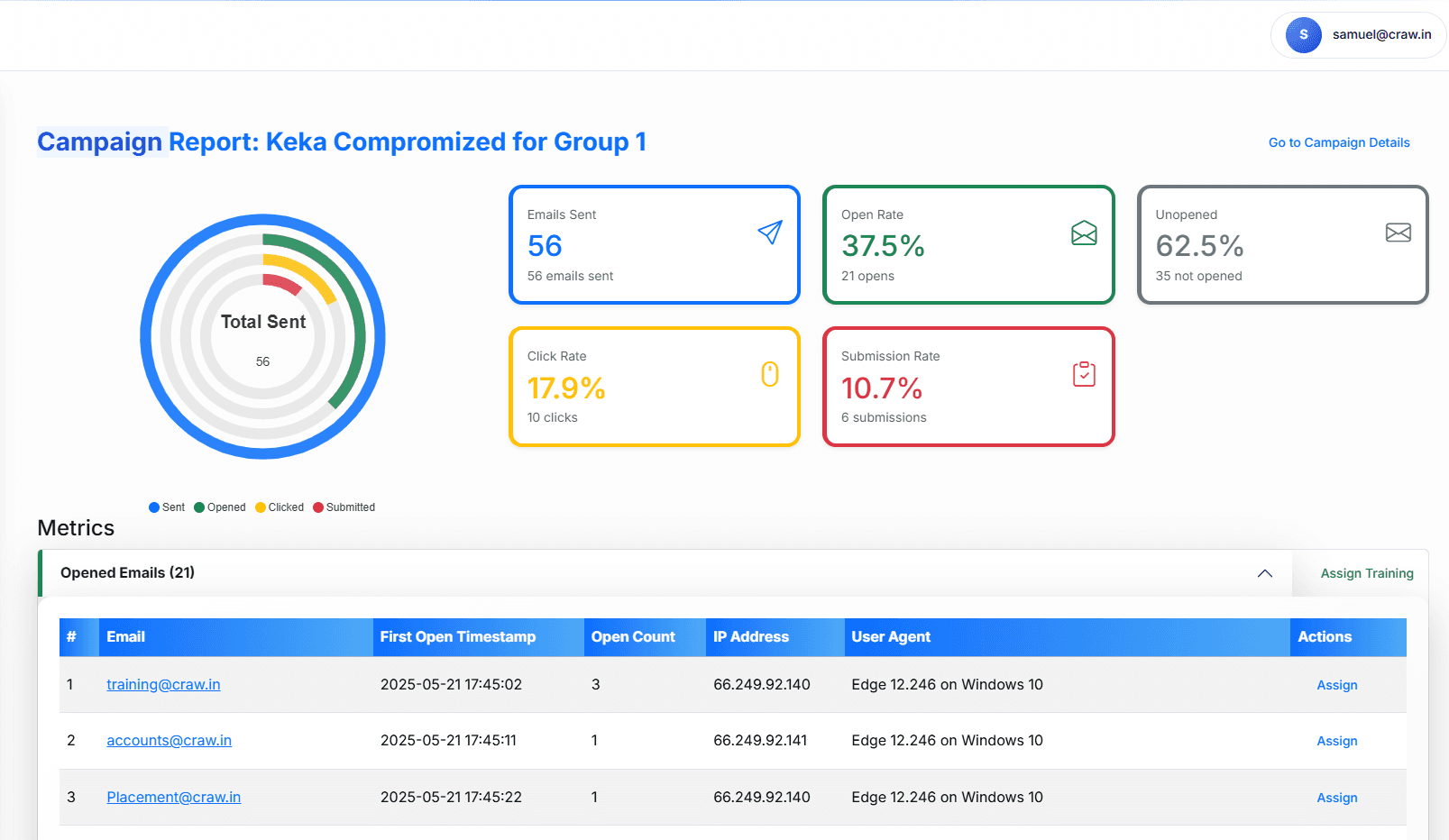
Detailed Analytics
Comprehensive reports with actionable insights including click rates, credential submissions, and risk assessment metrics.
Integrated Training
Automatic enrollment in security awareness training for employees who fall for simulated attacks.
Phishing Simulation Analytics
Real-time insights from phishing simulation campaigns across organizations
Average Employee Risk Metrics
Attack Type Distribution
Types of Phishing Attacks We Simulate
Comprehensive coverage of modern phishing techniques to test your organization's defenses
Form-based Phishing
Web forms designed to capture sensitive information like usernames and passwords
Link-based Phishing
Malicious links leading to spoofed websites that mimic legitimate sites
Attachment-based Phishing
Infected attachments that install malware or steal sensitive information
QR Code Phishing
QR codes leading to malicious websites or triggering harmful downloads
Our Phishing Simulation Process
A dedicated process designed to deliver authentic results and maximum employee learning
Consultation & Scoping
We establish simulation goals and understand your company's unique requirements and threat landscape.
Simulation Design
Our team creates realistic phishing emails based on your sector's danger profile and current threat trends.
Execution
Simulated attacks are initiated without advance notice to guarantee authenticity and real-world results.
Analysis & Reporting
We examine user activity and produce thorough reports that highlight risks and areas for improvement.
Awareness Training
Optional post-campaign training for employee empowerment and education on phishing prevention.
Key Advantages
Who Can Use Our Service?
Compliance-Ready Solutions
Our phishing simulation services help you meet important compliance standards by showcasing continuous security awareness campaigns
Ready to Test Your Organization's Human Firewall?
Contact our experts for a customized phishing simulation plan tailored to your organization's structure, scope, and employees knowledge quotient.


