Best Ethical Hacking Course Online In India [2024]

Best Ethical Hacking Course Online In India [2024]
Best Ethical Hacking Course Online
With the help of many information security professionals who are working soundly in numerous IT organizations in the market, hailing from almost every part of the planet, several expert ethical hacking institutions are offering their best-in-class Ethical Hacking courses online. Learn Hacking Online with world-class training facilities at Saket and Laxmi Nagar locations in Delhi NCR.
In the below-mentioned blog, we will study the prime Online Ethical Hacking Certification by Craw Cyber Security Institutions that offer every major and minor facility to give long-lasting study experience in the best ethical hacking course online in 2024.
What is Hacking?
Hacking is the process of identifying and exploiting a computer system vulnerability or a network to gain unauthorized access to system data and other system resources. In Simple Words, Hacking refers to Exploiting System Vulnerabilities. For example, exploiting the weakness of any service in a computer to gain unauthorized access to the data stored in the system.
What is Ethical Hacking?
Ethical Hacking (ethical hacking course online) is a legal practice of bypassing system security to test an organization’s defenses. The organization that owns the network or system allows cyber security analysts to perform this activity in order to test system or network weaknesses. Before malicious hacker does. And this whole process is called penetration testing.
Why Pick an Online Course in Ethical Hacking?
- Comfort and Flexibility
The flexibility that an online ethical hacking course provides is one of its main benefits. Online courses give you the flexibility to learn at your own pace and on your own schedule, in contrast to conventional classroom-based instruction. You can access course materials and lectures from anywhere, regardless of your location or time zone, whether you’re a working professional or a student.
- Curriculum
You can get a thorough curriculum that covers all facets of cybersecurity and ethical hacking from a credible online school. You will obtain a thorough grasp of how hackers exploit weaknesses and discover efficient defenses against cyber threats, from basic ideas to cutting-edge methods. Network security, online application security, cryptography, social engineering, and other topics are frequently covered in the curriculum.
- Possibility of Direct Experience
To learn the craft of ethical hacking, theory alone is insufficient. You need actual hands-on experience in this profession to become fully proficient. Virtual labs and real-world simulations are frequently offered in online courses on ethical hacking, allowing you to put your skills to use in a secure setting. This hands-on experience improves your ability to think critically, and solve problems, and fosters the attitude of a hacker.
- Professional Teachers and Assistance
Selecting a respected online ethical hacking school gives you access to knowledgeable professors with years of experience in the cybersecurity sector. These educators enhance your learning process by bringing real-world perspectives and useful expertise to the table. Additionally, the majority of courses have specific support resources like discussion boards and interactions with fellow learners.
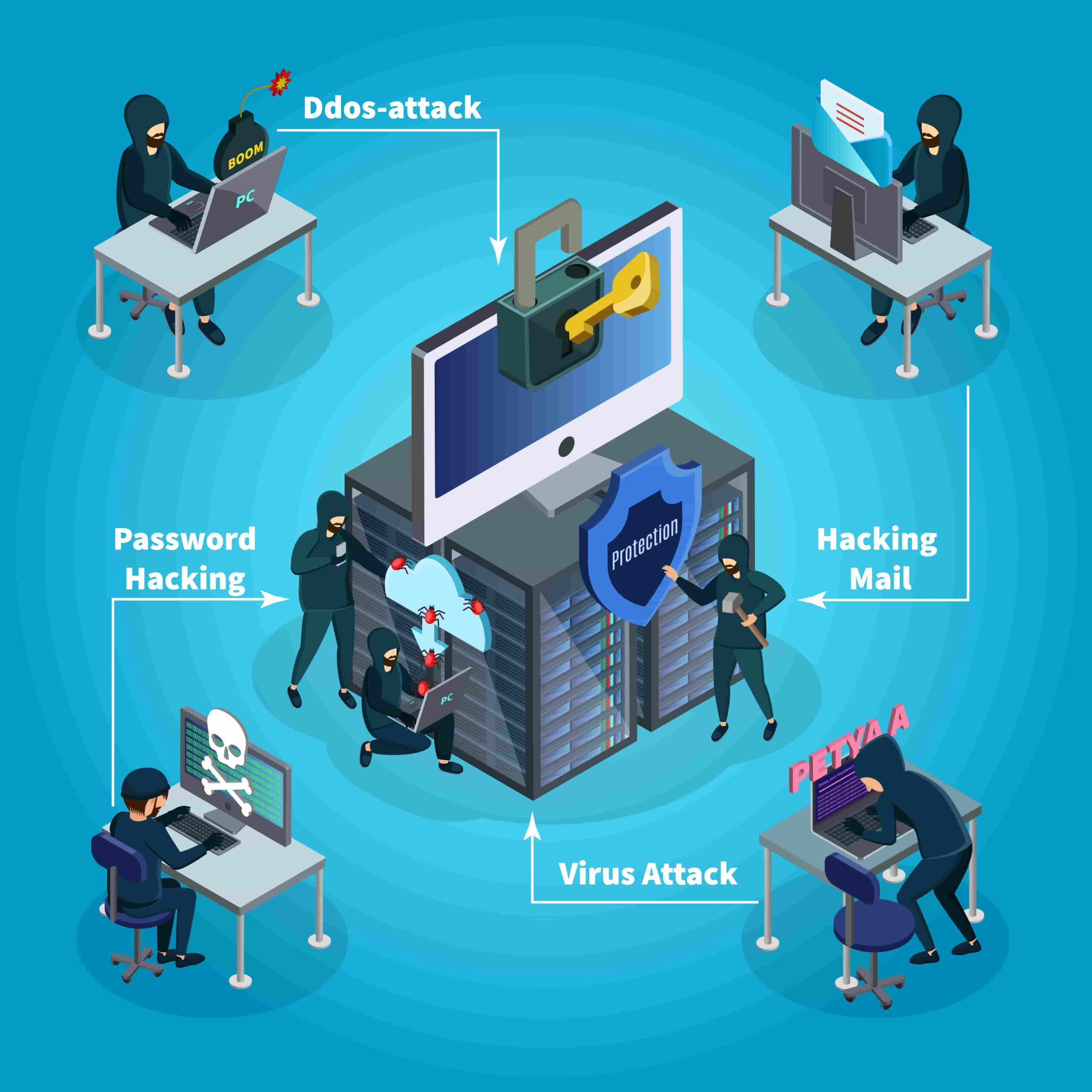
Certified Ethical Hacker Course Online
The CEH v12 Certified Ethical Hacker Course Online is a perfect IT Security/ Cybersecurity credential for a person who intends to enter this information security sector. Further, this Online CEH v12 Certification ensures that the learner is fully skilled in understanding the weaknesses and vulnerabilities in target systems. Moreover, the professionals with CEH v12 Certification in both online and offline formats will have advanced computer technology skills. They can take unauthorized access to devices by bypassing the security protocols and infiltrating the networks to secure the security parameters of the varied IT infrastructures.
In addition, the Online Certified Ethical Hacking (CEH) course consists of 20 informative modules covering more than 270 cyberattack technologies and mimics real-life scenarios. The Online Hacking Course – CEH v12 Certification will certainly help you find new ways to attack information systems and exploit system vulnerabilities.
Best Ethical Hacking Course Online with Certificate
Certified Ethical Hacker Training and Certification
Online CEH v12 Training
The Certified Ethical Hacker Online course provided by the EC-Council is one of the most popular and desirable certification courses in the field of information security. With Craw Cyber Security Institutions’ premium training faculty members related to varied backgrounds of ethical hacking, a dedicated learner can assuredly learn the hacking course online in Hindi medium where the friendly trainers will elaborate the fundamentals of ethical hacking in the easiest and most user-friendly manner.
In the same context, the EC-Council is one of the best-established and widely recognized offensive security certificates around. It’s ANSI-accredited and DoDD 8140-approved, which makes it exceptionally valuable for security professionals working in both the public and private sectors. CEH Training can be done by taking the Ethical Hacking Course Online also.
CEH v12 Certification
The Certified Ethical Hacker Certification is used to make system hackers preventive by considering the expanding security dangers to computer systems and web servers where a learner would be awarded a valid Online Ethical Hacking Certification after the successful completion of the online hacking course. Moreover, the certification one would get in this Online Ethical Hacking Course after the 12th will help you to understand the strategies utilized by hackers to interfere with systems.
Further, the CEH v12 Certification Online Course is a set of the latest hacking techniques, such as file-less malware, advanced social engineering practices, and the most advanced hacking tools. After having a CEH v12 Certification, a candidate will be recognized by the DoD (Department of Defense) and NCSC (National Cyber Security Centre) simultaneously altogether as additional benefits.
Online Ethical Hacking Course in India Key Skills
- Computer skills
- Security Concepts & Technologies
- Networking skills including ARP, DHCP, NAT, DNS, Subnetting, VLANs, MAC addressing, IPv4, IPv6, Public v Private IP, Routers and switches, OSI model
- Virtualization
- Database skills
- Advanced TCP/IP
- Wireshark for TCP Dump
- Digital Forensics
- Cryptography
- Web Application
- Scripting
- Linux Skills
- Wireless technologies, etc.
Ethical Hacking Course Online for Beginners
Who should do an Ethical Hacking Course Online?
The Ethical Hacking Course Online is not just for students or those pursuing graduation. This course is for anyone working in the IT field or somehow attached to the IT field. Professionals should go through this course because it will help them to understand how a small vulnerability can make a huge loss. We have enlisted the profiles that can take admission and enjoy the advantages of this genuine Online Ethical Hacking Course after the 10th:
- Cyber Security Engineer
- Cyber Security Analyst
- Network Security Engineer
- Penetration Tester
- Security Auditor
- Vulnerability Analyst
- IT Administrator
- IT Security Architect
- SOC Analyst
- Solution Architect

CEH v12 Certified Ethical Hacking Course Targets
CEH certification training will empower learners with a broad understanding of the following fundamental concepts:
- Information Security Overview, Cyber Kill Chain Concepts, Ethical Hacking Concepts, An Overview of Information Security, Information Security Controls, and Various Laws, Regulations, and Standards Related to Information Security
- Footprinting Concepts, and Footprinting Methodologies and Utilizing Footprinting Tools along with the Footprinting Countermeasures
- Network Scanning Concepts, Performing Network Scans, Using Scanning Tools, Host Discovery, Port and Service Discovery, and OS Discovery (Banner Grabbing/OS Fingerprinting)
- Enumeration Concepts, NetBIOS Enumeration, SNMP Enumeration, LDAP Enumeration, NTP and NFS Enumeration, SMTP and DNS Enumeration, NFS Enumeration, DNS Cache Snooping, and DNSSEC Zone Walking Along with the Countermeasures
- Vulnerability Assessment Concepts, Vulnerability Classification, Assessment Types, and Vulnerability Assessment Solutions, Along with a Hands-On Experience in Industrial Tools and Maintaining Vulnerability Assessment Reports.
- System Hacking Concepts, Phases of System Hacking, Attacking Techniques to Gain Access, Escalating Privileges, and Maintain Access on Victim Along with Covering Tracks by Clearing Logs
- Malware Concepts, APT Concepts, Trojan Concepts, Analysis of Various Viruses and Worms, File fewer Malware Concepts, Malware Analysis, Countermeasures, and Anti-Malware Software.
- Packet sniffing concepts, Sniffing Techniques: MAC Attacks, DHCP Attacks, ARP Poisoning, Spoofing Attacks, and DNS Poisoning, Using Sniffing Tools, Countermeasures, and Sniffing Detection Techniques
- Social Engineering Concepts and Related Terminologies like Identity Theft, Impersonation, Insider Threats, Social Engineering Techniques, and Countermeasures
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) Concept, DoS/DDoS Attack Techniques, Botnets, DDoS Case Study, DoS/DDoS Attack Tools, Countermeasures, and DoS/DDoS Protection Tools
- Session Hijacking Concepts, Application-Level Session Hijacking, Network Level Session Hijacking, Session Hijacking Tools, and Countermeasures
- IDS, IPS, Firewall, and Honeypot Concepts and Solutions, Evading IDS, Evading Firewalls, IDS/Firewall Evading Tools, Detecting Honeypots, and IDS/Firewall Evasion Countermeasures
- Web Server Concepts, Attacks, Attack Methodology, Attack Tools, Countermeasures, Patch Management, and Web Server Security Tools
- Web Application Concepts, Threats, Hacking Methodology, Web API, Webbooks, Web Shell, and Web Application Security
- SQL Injection Concepts, Types of SQL Injection, SQL Injection Methodology, SQL Injection Tools, Evasion Techniques, and Countermeasures
- Wireless Concepts, Encryption, Threats, Hacking Methodology, Hacking Tools, Bluetooth Hacking, Countermeasures, and Wireless Security Tools
- Mobile Platform Attack Vectors, Hacking Android OS, Hacking iOS, Mobile Device Management, and Mobile Security Guidelines and Tools
- IoT Concepts, Attacks, Hacking Methodology, Hacking Tools, and Countermeasures
- OT Concepts, Attacks, Hacking Methodology, Hacking Tools, and Countermeasures
- Cloud Computing Concepts, Container Technology, Serverless Computing, Cloud Computing Threats, Cloud Hacking, and Cloud Security
- Cryptography Concepts, Encryption Algorithms, Cryptography Tools, Public Key Infrastructure (PKI), Email Encryption, Disk Encryption, Cryptanalysis, and Countermeasures
Online Ethical Hacking Course Fees
Along with providing the most crucial Ethical Hacking Course Online, Craw Security also prepares its students with career-oriented techniques that could be very helpful in shaping an individual into a highly qualified and sincere information security professional who can be a proven asset for a cyber security enterprise in a real-time job. All these Ethical Hacking Courses Online come in a very pocket-friendly mode as Online Ethical Hacking Course Fees in Craw Cyber Security Institution at Saket and Laxmi Nagar branches offer cost-efficient and budget courses with proper financial aid for the students belonging to economically weaker and deprived sections of the society.
Phases of Hacking
In this article, we discuss the phases of hacking. There are mainly 5 phases of hacking. These are just a methodology. A hacker has to follow these 5 steps in a sequential manner:
1. Information Gathering and reconnaissance
This is the first step of hacking. This is also called footprint. In this phase, hackers try to gather all available information about a victim in order to gain unauthorized access to a victim’s system or network. In this phase, you collect all victim or network information:
- Network information
- IP Address
- Services running on a network
- Identifies vulnerabilities
- Employee information and many more.
There are two types of Footprinting:
Passive foot-printing:
- Collecting information without interacting with the target directly.
- Through search engines or public records.
- Used when information gathering must not be detected by the target.
Active foot-printing:
- Collecting information by interacting with the target directly
- There is a chance that the target will become aware of the information gathering.
- Info more accurate and rapid
2. Scanning and Enumeration
scanning is a method of getting network information such as identification of host, port information, and services by scanning network ports. By network scanning, you can get open ports. Live host in a network, services running on a host, and OS information. You can also scan for vulnerabilities in any network or computer system. By scanning the network, you can get network topology, router, firewall server, and host information. This can be done manually or by automated tools like Nmap, Nessus, Nikto, and many more.
3. Gaining Access
by now attacker gathers all information about a victim’s network or computer system. By using all information now, attackers try to break into a victim’s network or anything. Using any vulnerability or weakness, attackers try to gain unauthorized access to a victim’s network or system. After gaining access to a system attacker also tries to gain admin-level access. To do that attacker also does privilege escalation. In this whole process, attackers use various tools and methods to break into a system.
4. Maintaining Access
Once a hacker has gained access to a victim’s network or system. Now they want to maintain that access for future exploitation and attacks. Once hackers own that system. Hackers can use this system in many ways, like zombies attacks and DDoS attacks, and use this system for malicious purposes. There are many ways to maintain that connection, like installing trojans, rootkits, backdoors, or other malicious files in the victim system.
5. Clearing Tracks
This is the last phase of hacking. In this phase, the attacker tries to clear all evidence so that at a later point in time, no one will find any trace leading to him. Hacker tries to clear out sent mails, clearing server logs, temp files, and any other evidence that leads to him. This is a very important step because it clears the system information, and that makes it harder to track a hacker.
Frequently Asked Questions
1: How much does CEH v12 certification cost?
The Certified Ethical Hacker Certification exam is a 4-hour Exam with 125 multiple-choice questions. The certification cost of CEH v12 is just INR 25,000. But if you choose CEH Training and Certification, the cost will be INR 35,000. One can also apply for a free demo class at the magnificent facilities of Craw Cyber Security Institution, remarkably present at Saket and Laxmi Nagar locations in New Delhi. The best part of CEH Training and Certification from Craw Cyber Security is you can go for this course even after 10th (Secondary School).
2: Is CEH hard to pass?
This thing totally depends upon the learner as to which source one has studied. Craw Cyber Security provides well-qualified, certified, and experienced trainers, which makes Craw Cyber Security more efficient in providing more skills to its learners. Moreover, you should be aware that the EC Council has its own online and offline syllabus for training its students in Certified Ethical Hacker Courses. In the same context, Craw Security also trains their respective learners in a well-organized, nicely planned manner to train them with all the essential skills that a Certified Ethical Hacker (CEH) should have.
3: Is CEH certification valuable?
Certified Ethical Hacker (CEH) is the most advanced ethical hacking course online. It can help you gain knowledge about the IT Security/Cybersecurity domain or become any level of Security Expert. The CEH has a great combination of attainability and recognizability, which makes the CEH an ideal first penetration testing certification.
CEH is valuable because it measures your ability to perform reconnaissance, enumeration, gain access, maintain access (persistence), and cover your tracks. With the rate at which cyber-attacks and vulnerabilities are rising with every passing day, causing billions of dollars of damage to organizations across the world, the job profile in CEH (Certified Ethical Hacking Course Online) is highly in demand.
4: How long does it take to become a certified ethical hacker?
Ethical hacking is a broad background where things depend on how much time you can give to learning diverse methodologies related to hacking daily. The authentic Certified Ethical Hacking Course Online program takes five days to complete. To be a master in hacking would not take more than 5 years. To become a successful hacker, you need to think like a hacker.
5: What should an individual do after completing an Ethical Hacking course online?
After the completion of the course, you should go for global level CEH certification which is held by EC-Council; it can be done from Craw Cyber Security, Delhi because Craw Cyber Security is a partner of EC-Council.
6: Can I learn ethical hacking online?
Yes, you can learn the varied concepts associated with ethical hacking courses online through a varied methodology possessing a curriculum comprised of an Online Ethical Hacking Course through a team of genuine information security expert trainers in Craw Cyber Security Institution at its Saket and Laxmi Nagar educational branches.
7: Which online course is best for ethical hacking?
The Online Ethical Hacking Course in Delhi through the magnificent facilities of Craw Cyber Security Institution at Saket and Laxmi Nagar locations is the best that you can get in an online hacking course.
8: What are the 3 types of hacking?
The 3 types of hacking are mentioned as follows:
- White Hat Hackers
- Black Hat Hackers
- Grey Hat Hackers
9: Can I learn hacking at home?
Yes, you may nicely learn the varied functions of the ethical hacking course online while sitting at your home through the magnificent online ethical hacking course of Craw Cyber Security Institution, remarked its auspicious presence in the market for a continuous period of 10+ years.
10: Can hacking be a career?
Hacking cannot be a career; however, learning ethical hacking and using it for various genuine methods can be a proven career for someone who has a sincere intention of learning to hack online.
11. Who should pursue CEH Certification?
CEH certification is ideal for IT professionals interested in network security and understanding hacking techniques from an ethical standpoint. This includes security officers, auditors, security professionals, site administrators, and anyone concerned about the integrity of network infrastructure.
12. What are the prerequisites for CEH Certification?
There are no strict prerequisites for taking the CEH exam, but it is strongly recommended that candidates have a good understanding of networking, operating systems, and information security. Some choose to take relevant training or courses before attempting the certification exam.
13. What topics are covered in the CEH exam?
The CEH exam covers topics such as ethical hacking methodology, network traffic sniffing, system hacking, malware threats, social engineering, session hijacking, evasion techniques, cryptography, and various types of cyber attacks.
Conclusion
In the final words, I just want to say that this is a genuine methodology to learn hacking online through a high-end ethical hacking course online by the most sincere and experienced training faculty members having almost 10+ years of information security experience in reputed IT organizations. If you also possess a keen intention to build a shinier career in this domain of ethical hacking and information security, you can enroll in our upcoming batches of ethical hacking courses online offered via VILT (Virtual Instructor-Led Training) sessions to all the eligible students present at anywhere in this world.



















